I have never found a good guide for how to create my own Zabbix LLD rule and create a template for that.
In this post I will take you through these steps.
So, how is it works? What we need for it works?
How is it works
We need a script which return to us a JSON with a list of <key>:<value>. Where the keys are our LLD macros and the values are the data to use in our items prototypes.
When we create an example you will understand better.
Hands-on
In this case, I needed monitoring CPU usage and Memory usage by Pods in an Azure managed cluster Kubernetes (AKS) with nodes Windows and Linux.
I found a ready script fot it: https://github.com/ikzelf/zbx_kubernetes/blob/master/zbx_k8s_lld.py
Then, I put it on: /usr/lib/zabbix/externalscripts/ and change your permission execution: chmod +x zbx_k8s_lld.py
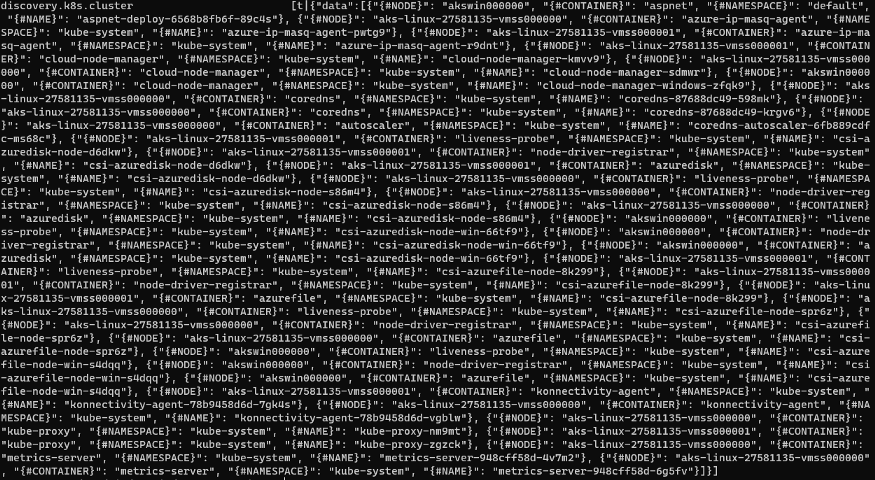
Then, test it:
That’s cool!
Now, we can create a UserParameters to run this script in our discovery rule.
So, edit the zabbix_agentd.conf en add it:
Test it again!
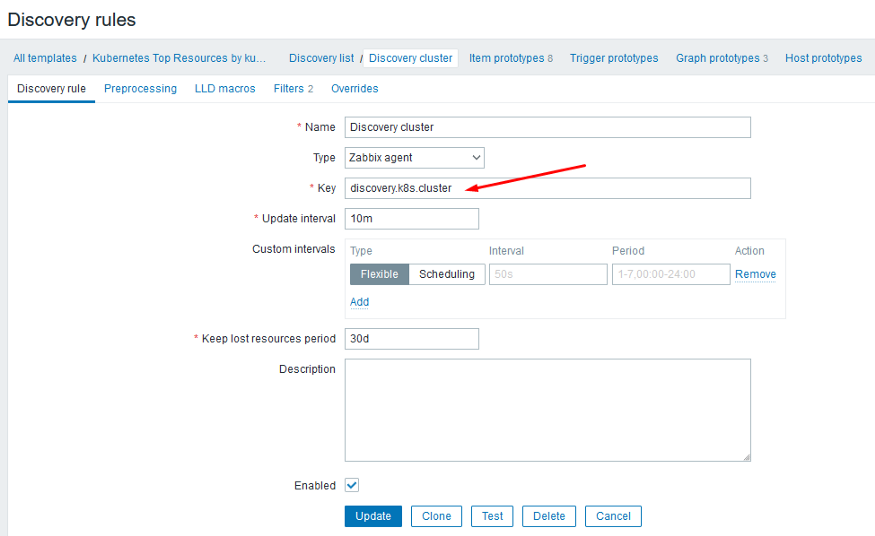
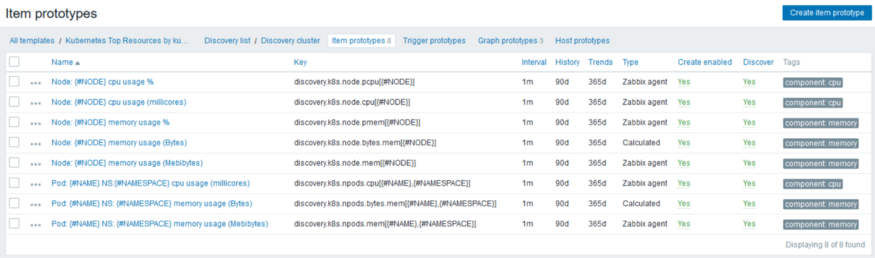
Now, we can create our template and our rule and items.
This is the point where we use the LLD macros to create each node and pod found.
The data passed as a param ({#NODE}) will be received by the UserParam to get the values and then return only one thing for for us.
For each item prototype we need add more line in our zabbix_agentd.conf
Test again and again:
I created some graphs too.
Some template macros for filters.
And the discovery rule filter using template macros.
To zabbix user can connect in my AKS was needed to do login in Azure CLI and get-credentials to merge kubectl config.
I created a user in Azure AD for it and assigned the roles for it:
Test more one time:
And finally create a host and associate a template.
For download of template: https://github.com/filipisaci/zabbix-kubernetes-top
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!
User Popularity
72
Influence
7k
Total Hits
1
Posts

















Only registered users can post comments. Please, login or signup.