
Automatic package signing — diagram
In this post, I will show you how to sign your AWS Lambda packages as soon as they are uploaded to your Amazon S3 Bucket.
How to sign your AWS Lambda packages as soon as they’re uploaded to your Amazon S3 bucket.
In a previous post, I wrote about AWS Signer and how to sign your AWS Lambda packages — it’d be best if you read and implement the steps there before starting this one:
Sign your AWS Lambda packages
In this post, I will show you how to sign your AWS Lambda packages as soon as they are uploaded to your Amazon S3 Bucket.
It eases the burden of having to sign your packages one by one in the AWS Signer service.
Prerequisites
- IAM User must have permissions to AWS Signer, AWS Lambda, Amazon IAM Roles, and Amazon S3.
- Create an AWS Signer profile. https://medium.com/@jean.velez2/sign-your-aws-lambda-packages-39d3be4b18b8
- Create AWS Lambda function (Python 3.9).
https://docs.aws.amazon.com/lambda/latest/dg/getting-started.html
- Create Amazon S3 Buckets with versioning enabled. https://docs.aws.amazon.com/AmazonS3/latest/userguide/create-bucket-overview.html
AWS Lambda
We will be setting up the AWS Lambda function which takes care of the signing of the Amazon S3 object through the Event notification.
Go to AWS Lambda service:
Access the AWS Lambda function instance you will be using for this demo.
The following will display the required “Environment variables” the AWS Lambda function requires.
In this case, the Environment variable will be the AWS Signer profile name you’ll be using to sign the packages from Amazon S3 (The value of the environment variable is blank in the image, cause the name I chose was a bit embarrassing).
Now you must access the Execution Role.
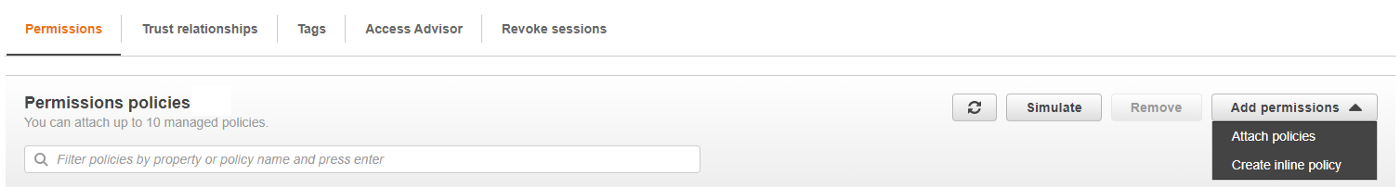
In the “Configuration” tab, click on “Permissions” and click the “Role Name”:
Once inside your Execution role.
On the “Permissions” tab click “Add permissions > Create inline policy”:
Click the “JSON” tab, copy-paste the following, then click “Review policy”:
Fill in the required fields and then click “Create policy”:
Now head back to the AWS Lambda function.
You will upload the following code:
https://github.com/jeanvelez2/sign-aws-lambda-packages-as-upload-to-aws-s3
Amazon S3 — Event Notifications
Amazon S3 has a feature called “Event Notifications” which sends event data related to the activity occurring in the Bucket.
https://docs.aws.amazon.com/AmazonS3/latest/userguide/NotificationHowTo.html
We will be using this detection whenever a file is uploaded to Amazon S3 in a specific folder.
Let’s get started!
Go to Amazon S3 service:
Access the bucket you wish to use for this demo.
Click on the “Objects” tab:
Create two folders named “unsigned” and “signed” with the “Create folder”:
Click on the “Properties” tab:
Scroll down until you see “Event notifications”, and click the “Create event notification” button:
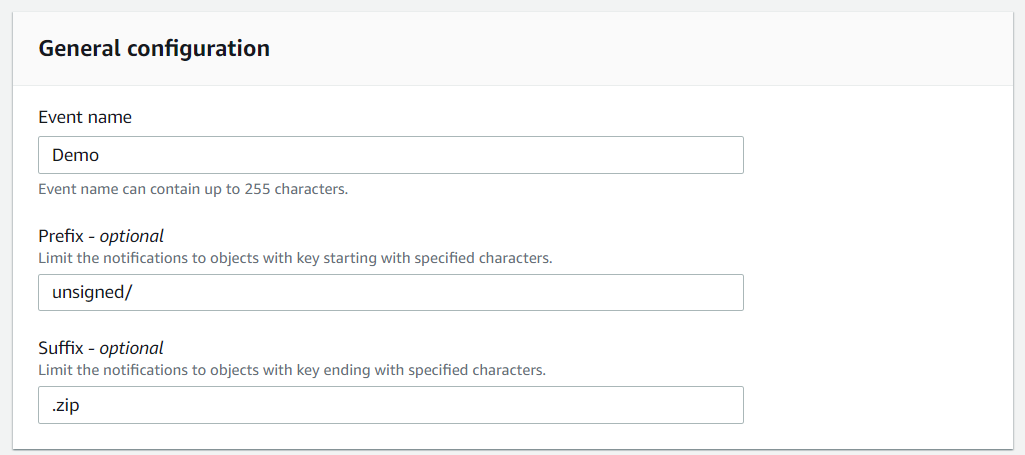
The “General configuration” will request which prefix and suffix of the Amazon S3 Object will activate the event notification.
In this demo, we will use “unsigned/” as Prefix and “.zip” as Suffix, which states that the Event notification will be triggered by .zip objects in the unsigned folder.
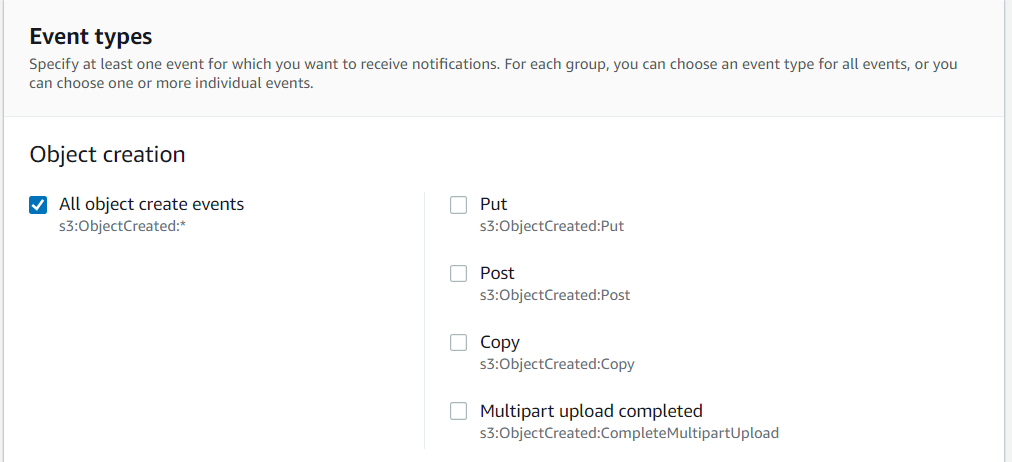
Select “All object create events” in Event types:
Scroll down to “Destination”, you will specify the AWS Lambda function that the Amazon S3 Event Notification will trigger:
Click “Save changes”:
Amazon S3 — Upload package
Now that we have everything set up, we will test if the package was signed and sent to the destination path in Amazon S3.
Go to the “unsigned” folder in the Amazon S3 bucket and upload a file:
Great, to confirm it has been signed you must now go to the “signed” folder:
I’m grateful it all worked (And I didn’t embarrass myself).
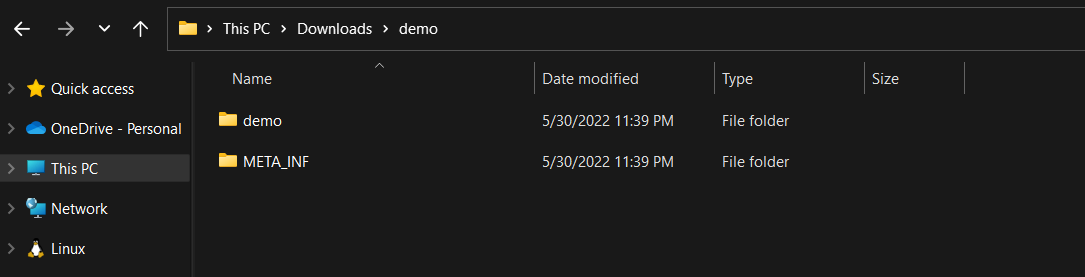
To double-check you must download the file to your local machine and decompress it.
You will see the following:
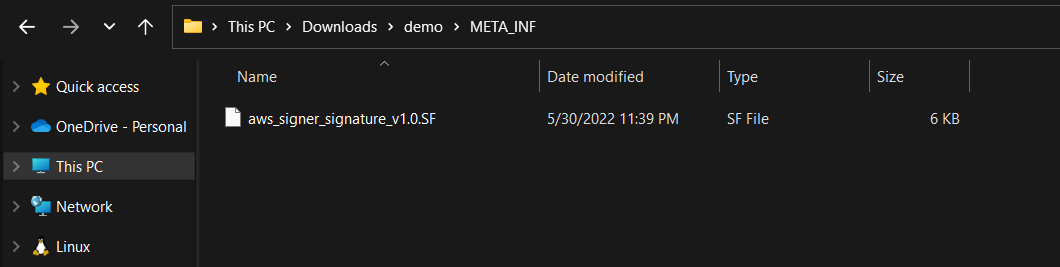
When signing your packages, it will include the “META_INF” inside your package which contains the signature.
Open it and see the eye-sore than any human will ever witness:
Conclusion
You are now able to easily sign your AWS Lambda packages as they’re uploaded to your Amazon S3 bucket, instead of manually signing them manually in the AWS Signer profile (which can be daunting).
It has been fun writing this post.
Any questions or comments, please let me know.
Hope you have a nice day, Thank you and Gracias!!!
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!
User Popularity
103
Influence
10k
Total Hits
6
Posts























Only registered users can post comments. Please, login or signup.