
Threat Intelligence is a crucial subject under the umbrella of cybersecurity. There might exist a lot of doubts in specific terminologies associated with ‘Cyber Threat Intelligence’. While various resources have taken excellent efforts to define them, let us take up some examples while we understand the classification of data collated while researching.
The Process
CTI refers to collecting bits of data from all the possible resources. It is somewhat similar to a nostalgic childhood game of finding a coin tossed in the pool. This collection of data while researching might still be unstructured and irrelevant leading to a rabbit hole.
But if we look and sort this data according to the classified categories, then suddenly the whole picture starts conjuring up. To be more specific, the data that we look at during our research can be categorized as strategic, tactical, technical, and operational.
Technical Threat Intelligence
Discussing technical threat intelligence includes collating all the data which is machine generated and machine readable. This data is often traced by security devices or fed into security devices to be traced in future.
A very prominent example of it would be a malware campaign that leaves back its IOCs (Indicators of Compromise). Technical threat intelligence collects hashes, checksum, IP addresses used for hosting C2 servers, email headers collected from phishing campaigns, malicious URLs etc.
Operational Threat Intelligence
I have always found operational threat intelligence and tactical threat intelligence overlapping each other in most cases. But to draw a thin line between these two forms of actionable intelligence, the operational intelligence classifies all the data related to evolving attack vectors, predictive immediate patterns with respect to an operation, common frameworks abused, and future announcements made by the group.
This might include the researcher being actively alert on chat rooms, private communication channels, and open forums where the hackers are popular. They might also want to investigate the activities of the hacker group, their interactions, associations, and open source exploits discussed by them.
These are some of the examples of the data classified in the operational threat intelligence used by threat actors to fulfill their motives.
Tactical Threat Intelligence
Tactical Threat Intelligence talks all about the TTPs (Tactics, Techniques, and Procedures). This defines a fixed way of operation and tools of a threat actor group. Malware, cracking tools such as Mimikatz, infiltration methods such as phishing campaigns, mass mailings, or compromised credentials are some of the ways that add characteristics to a subject threat actor group.
MITRE ATT&CK is one such huge knowledge base of known TTPs of threat actors. For a researcher’s investigation in attributing a threat actor group- highlighting its TTP is crucial.
Strategic Threat Intelligence
Strategic Threat Intelligence collects the pattern, trend, attribution, or motivation behind a cyber attack.
This type of intelligence looks at the bigger picture or rather adds the missing piece to the puzzle.
When a cyber attack occurs, there are various aspects to discuss that can help researchers identify elements like region of attack, motivation of the attack (which can be financial, hacktivism, geo-political scenario, etc) and then make attempts to predict the future chain of events.
People across various roles specific to cybersecurity consume this information differently. Some roles are particular of the volatile data such as IOCs while some might want to understand the bigger picture, i.e on a strategic level to understand the motivation of a group.
Across multiple roles, the classified intelligence helps us to be proactive, identify the pattern or motivation, and engage businesses into taking mitigation steps.
Case Study I: Data Breach
Given below is a case study of a ransomware attack. This case study is completely fictitious and its connection with any real-life entity is a mere coincidence. The purpose of sharing this case study is to break down the collected data into the categories of actionable intelligence while trying to complete the whole picture.
Please note that getting intelligence is not as easy as mentioned below, these are just some extreme cases merged together for quick grasping and better understanding. Let’s move on!
Synopsis: A well known company Molar Associates based in Australia was a target of ransomware attack by ‘Notorious Group’ on 6 August 2022. While investigating into the details of the incident, following data was collated.
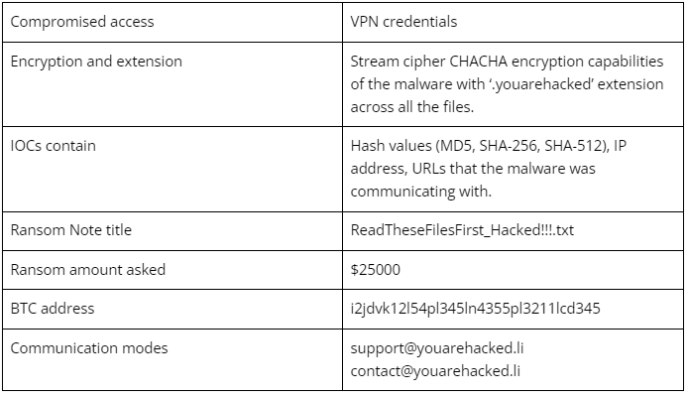
Technical Threat Intelligence
Tactical Threat Intelligence
Based on the analysis of the incident, the researcher here can try to identify the TTPs used by the threat actor group. Evidence indicates that the initial way to get access into the private network of the company was found to be compromised VPN credentials. Further, deployment of ‘Demomalware’ was initiated that starts scanning for the sensitive directories and steals the data before encrypting it. The malware looks sophisticated and relatively new.
Operational Threat Intelligence
Chat rooms, trends of activity, and announcements by the group indicate that most of their victims are private organizations from Australia amongst the revenue range of $150 million to $300 million. The group’s inclination towards Australia helped us identify a set of companies within that revenue range. Dark web forum activities hint at some cybercriminals selling access to Australian entities which can attract a buyer like subject ransomware group.
Strategic Threat Intelligence
Emergence of new ransomware groups isn’t new, however in this case we identified similar ransomware notes shared by another two ransomware groups, indicating a possible rebranding. The group rebranded itself once in April 2021 and then in December 2021, before coming out as a new group in August 2022. The motivation of the group is financial gains while following the ‘name and shame’ policy to pressure the companies into giving ransom. As far as previous rebrands are concerned, one group targeted all the US based entities and the other focused on South African regions. Based on mild confidence, in future a group targeting single region entities can be linked to this group with a new set of TTPs.
Concluding on the article, I tried to explain the different types of data that is critical to evaluate to have comprehensive information on the adversaries, their TTPs, and new campaigns.
Hope you liked the article. Let me know what you think. Coming up with exciting topics soon!
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!














Only registered users can post comments. Please, login or signup.