Shifting Left with Security Policy as Code (SPaC)
WAF: Web Application Firewall
NeuVector provides a Web Application Firewall (WAF) feature that allows you to protect your applications against common web application attacks like SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities.
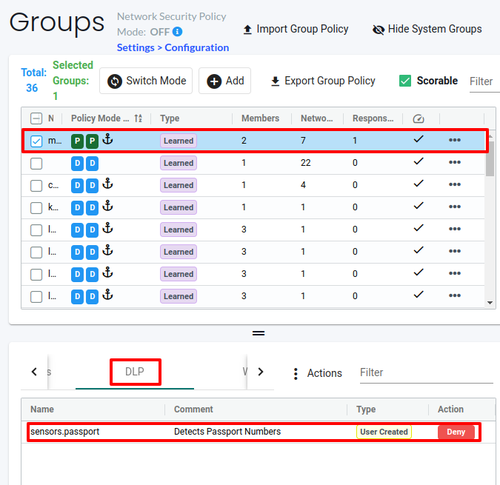
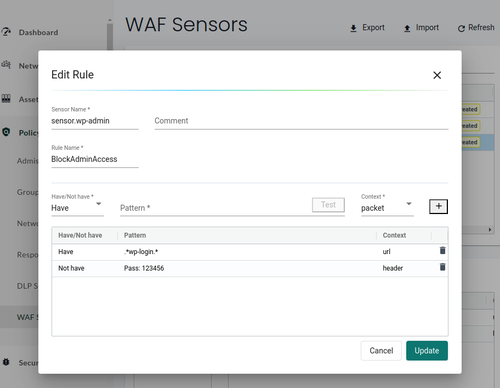
You can also create Security Policy as Code for WAF rules, share it, and enforce it across all environments, including the running groups in your current environment. The idea is the same: using regular expressions to detect and block malicious requests. For example, if we want to block all requests that go to the /admin paths without sending a particular header, we can create a WAF rule to do so.
WAF Rule
You can also add the WAF rule to the WordPress group (nv.my-wordpress.wordpress) and configure it to Deny requests that match the rule.
Enable WAF Rule
You can test this using curl, but don't start by triggering the WAF rule; otherwise, you will be blocked from accessing the path /wp-login:
# This request should not be blocked
while true; do curl -ILkv -H "Pass: 123456" \
http://wordpress.167.99.244.81.sslip.io/wp-login.php; sleep 2; done;
# This request should be blocked
while true; do curl -ILkv -H "Pass: 654321" \
http://wordpress.167.99.244.81.sslip.io/wp-login.php; sleep 2; done;
WAF: Web Application Firewall
NeuVector provides a Web Application Firewall (WAF) feature that allows you to protect your applications against common web application attacks like SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities.
You can also create Security Policy as Code for WAF rules, share it, and enforce it across all environments, including the running groups in your current environment. The idea is the same: using regular expressions to detect and block malicious requests.
Let's consider the following example: you have a WordPress application running in your cluster, and you want to protect the /wp-login path from unauthorized access. For example, we can only allow requests to this path if they contain a specific secret header (Pass: 123456 as an example).
To test this, install a WordPress application in your cluster:
# Add the Bitnami repository
helm repo add bitnami https://charts.bitnami.com/bitnami
# Install the WordPress Helm chart
helm upgrade --install my-wordpress bitnami/wordpress \
--version 24.1.5 \
--namespace my-wordpress \
--create-namespace \
--set mariadb.architecture=DevSecOps in Practice
A Hands-On Guide to Operationalizing DevSecOps at ScaleEnroll now to unlock all content and receive all future updates for free.