
Every week, we share the most popular articles, tutorials, and resources from FAUN Topics about Programming, DevOps, DevSecOps, Cloud Native, Cloud Computing, and Blockchain.
If you want to learn more about FAUN Topics (our weekly newsletters), join us here.
How to Test Microservices
To test a microservice application, one should follow a modified testing pyramid that includes Unit Tests, Contract Tests, Integration Tests, Component Tests, and End-to-end Tests.
- Unit tests check code in isolation, either with mocked external dependencies or allowing the tested code to call other microservices in a non-deterministic way.
- Contract tests check that microservices adhere to the agreed-upon interfaces, input and output characteristics, performance, and time limits.
- Integration tests check the communication and cooperation between microservices.
- Component tests examine the behavior of a group of microservices working together.
- End-to-end tests test the entire system as a whole.
Fzf: A tool that will transform your CLI life
Fzf is an interactive fuzzy search tool for the terminal that can greatly improve your command line productivity.
It can be applied to any list of items, such as files or packages in a Debian distribution, and offers fast fuzzy searching with real-time reordering of results and preview capabilities.
Fzf can also be used as a framework to run commands on elements within the list and display results in a preview window. Practical examples of fzf's application include using it to search for packages in a Debian distribution and improving the Salesforce CLI experience by fuzzy searching through its commands and switches, with the help docs and examples displayed as you cycle through the list.
Best Practices for Kubernetes Readiness and Liveness Probes
The biggest mistake Kubernetes admins make with health probes is configuring the probes the same way for all apps.
To ensure appropriate configuration, it's recommended to follow these 6 best practices:
- Configure the probes based on the time required for your app to load, by adjusting the initialDelaySeconds parameter.
- Configure the probes based on the time required for your app to respond, by adjusting the timeoutSeconds parameter.
- Raise the probe frequency for critical applications, by decreasing the periodSeconds and increasing successThreshold, and decreasing failureThreshold.
- Lower the probe frequency for non-critical applications, by increasing the periodSeconds, decreasing the successThreshold and increasing the failureThreshold.
- Give flaky apps more time to respond, by increasing the failureThreshold and periodSeconds.
- Check the entire application to determine its real state, by setting the probe to check all dependencies of the application rather than just a single endpoint.
A Simple Overview of Authentication Methods for Kubernetes Clusters
Authentication and authorization are key areas of interest in Kubernetes. The main objective is to validate identity and validity of users/machines. X.509 certificates, service account tokens, and nodes joining must be authorized to protect against imposters.
Kubernetes has a wide range of authentication methods, and the article will detail each of them and their uses.
Cloud Functions Best Practices - Optimize the Cloud Functions
In this article, the author provides advice on optimizing Google Cloud Functions. They recommend splitting up code that performs similar tasks into separate, generic functions. This way, if a change to an API used by multiple Cloud Functions is needed, it only has to be done in one place instead of having to update each function individually.
The author provides an example of creating a generic Cloud Function for sending messages to Slack and then linking to it from other Cloud Functions via Pub/Sub. By doing this, the code is not repeated, functions are faster, and debugging is easier.
5 steps to help make your software supply chain more secure
In summary, you can:
- Enhance your Google Cloud security features with the Google Cloud security foundation guide and engage Mandiant experts for an assessment.
- Use Google Cloud DevOps capabilities for fast and secure software delivery, and review software license terms in dependencies.
- Document your organization's policies and incorporate them into your development, build, and deployment processes.
- Use Google Cloud's Software Delivery Shield, a fully managed software supply chain security solution.
- Enable the Assured Open Source Software (OSS) service for secure and verifiable OSS packages.
Simplifying internal AWS Lambda APIs
AWS Lambda has 3 APIs that run inside a lambda function along with the user code:
- Extensions API,
- Telemetry API,
- and the Runtime API.
The Extensions API serves as an extension registry and it communicates with the lambda runtime to let it know about the extension code to be run.
The Telemetry API is a webhook that allows the lambda runtime to send events to a locally running web server inside the lambda function. The telemetry API can provide limited telemetry information about the runtime of the app, as well as log information sent to standard out.
The Runtime API is meant for building custom runtimes for lambda and it allows the user to publish to internal Runtime API endpoints. It is good to understand the life cycle of a lambda function to understand the role of each API during the life cycle.
This article is going to focus mostly on the Extensions and Telemetry API.
2023 State of Databases for Serverless & Edge
Lee Robinson, VP of Developer Experience at Vercel, provides an overview of databases that are well-suited for use with modern application and compute providers, such as serverless and edge compute.
The author focuses on transactional workloads, and evaluates databases based on the following criteria: compatibility with serverless and edge compute, compatibility with JavaScript and TypeScript codebases, being connectionless, web-native, lightweight, and type-safe.
They also discuss the new programming model that has emerged in response to the requirements of serverless and edge compute, as well as the current trends in the backend space.
1500 most common data structures and algorithms solutions
Here is a list of the 1500 most common and useful solutions for data structure and algorithm programs, which are often asked in interviews and programming practices.
Efficient DevSecOps workflows: Hands-on python-gitlab API automation
The blog post discusses the use of the python-gitlab library to interact with the GitLab API.
It covers basic usage of the library, such as working with API objects, attributes, pagination, and resultsets. The post then moves on to advanced DevSecOps use cases for API read and write actions, such as checking project settings, creating issue indexes, and optimizing code performance. Finally, the post provides tips for advanced custom configuration and CI/CD integration, as well as suggestions for further use cases.
The 10 Coolest Open-Source Software Tools Of 2022
The coolest open-source software tools in 2022 include the Apache Druid database, Apache Iceberg data analytics tool, Grafana observability software and TensorFlow machine learning platform.
OpenAI's ChatGPT could replace some software engineers, report suggests.
OpenAI is expanding its AI capabilities by hiring hundreds of international contractors to teach its AI software engineering. The company aims to advance its Codex technology, which converts natural language into code, potentially replacing some human coders.
OpenAI's contractors are tasked with finding bugs in AI code and providing explanations for fixing them. This training data will be fed into OpenAI's AI technology. ChatGPT, owned by OpenAI, already threatens to disrupt several industries and might add software engineering to its list.
State of Infrastructure-from-Code 2023
Infrastructure-from-Code (IfC) is a new way of thinking about cloud infrastructure that seeks to derive infrastructure from the application code, rather than defining it as code. This process analyzes the application code to infer the cloud resources needed and creates and maintains them without manual configuration.
There are two main approaches to IfC, with language-based tools introducing new programming languages and SDK-based tools introducing their own SDKs. Both aim to make it easier for developers to provision and tear off infrastructure, unlocking a generational leap in productivity.
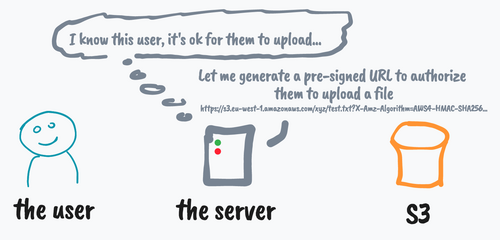
The illustrated guide to S3 pre-signed URLs
S3 pre-signed URLs provide a way for various clients to upload and download files in a controlled manner from Amazon S3. By default, all objects in S3 are private and require proper credentials or the AWS SDK to add new objects or retrieve the content of an object.
Pre-signed URLs are specially crafted S3 URLs with embedded credentials and time-limited availability, generated by the server using its own credentials. The user can make an HTTP request (PUT or POST) to the pre-signed URL to upload or download the object, without having to know anything about S3 or the AWS authentication protocols.
Pre-signed URLs can be used in various use cases such as uploading photos, downloads of large files, document management, marketing campaigns, and inter-system communication.
More details and most importantly illustrations are available in this article.
Generate diagrams programmatically using D2
This article is about generating diagrams programmatically using D2, a modern text-to-diagram language.
D2 has a built-in API for manipulating the abstract syntax tree (AST), allowing developers to build and edit diagrams programmatically. The article demonstrates a concrete example of building a diagram that visualizes a schema after each line of a SQL statement.
The code goes through the SQL statements and turns them into structured data, which can then be translated into d2oracle calls. The demo involves reading in a .sql file, converting each raw string statement into a structured command, passing each command into a function to programmatically edit the diagram, and rendering an SVG file after each line.
The final result is a D2 script that visualizes the schema being built up.
JWT in Golang — How to Implement Token-Based Authentication
The article explains how to implement JSON Web Token (JWT) authentication in Golang using the go-jwt package.
The process consists of the following steps: generating tokens, validating tokens, and refreshing access tokens using the refresh token. A secret key and claims (user_id, email, and token lifetime) are used to generate the tokens. The tokens are then validated using the secret key and the claims are extracted. The refresh token is used to refresh the access token when it has expired.
The article also uses an example of a residential locking system to relate the JWT terminologies to real-life scenarios.
Composable Architecture: all the flexibility your software needs
By @pmartinoli, Technical Writer, Mia-Platfom
The Composable Architecture pattern is a modern approach to software architecture that allows for the rapid and continuous evolution of services, with individual modules called Packaged Business Capabilities (PBCs) that can be developed internally, purchased from third-party vendors, or open-source components.
This approach provides speed, reuse, standardization, flexibility, and scalability, and can reduce costs by 40% by 2024.
An Introduction to GitOps and Argo
GitOps is a framework or set of best practices for managing cloud-based infrastructure using Git as a single source of truth. The configuration in Git is treated as a set of facts about how the infrastructure should look rather than instructions to perform. Automated processes take this configuration and make sure the environment matches the state described in the repository. The benefits of GitOps include faster and frequent deployments, faster error resolution, and built-in auditing.
Argo is a collection of tools that helps make implementing GitOps easier for Kubernetes-based applications. The Argo project includes Argo Workflows, Argo CD, Argo Events, and Argo Rollouts. Argo Workflows is a workflow engine for Kubernetes that creates multi-step workflows using Kubernetes Custom Resource Definitions. It can be used in a standard CI/CD pipeline, data processing pipeline, or as an MLOps tool.
FTX’s implosion and SBF’s arrest, explained
FTX declared Chapter 11 bankruptcy after a run on the crypto exchange prompted by questions from rival Binance and revelations about its relationship with Alameda Research. Now he’s under arrest in the Bahamas and could face extradition.
2023: The Year Blockchain Becomes a Sustainability Solution
Blockchain technology can contribute to sustainability by tracking and proving emissions from organizations and supply chains through their immutable, transparent and accountable nature.
Using smart contracts, companies can track and report carbon emissions produced at every step of their operations, and the use of zero-knowledge technology can ensure privacy. Blockchain can also be used in the carbon credit market to tokenize digital environmental assets and to manage electrical grids. The United Nations is also supporting initiatives in the Web3 community for blockchain applications in climate action.
In 2023, there is expected to be an increase in sustainability-focused systems using blockchain to track environmental impact and to provide clear standards for acceptable levels of impact.
Each week, we share the best tutorials, news, tools, and other resources from the software engineering community and send them in multiple newsletters, each focused on a given topic: DevOps, DevSecOps, Golang, Python, Blockchain, Google Cloud, AWS, Azure, Kubernetes, Serverless and more!
Subscribe to one or more of our FAUN Topics here.
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!
User Popularity
3k
Influence
319k
Total Hits
44
Posts


























Only registered users can post comments. Please, login or signup.