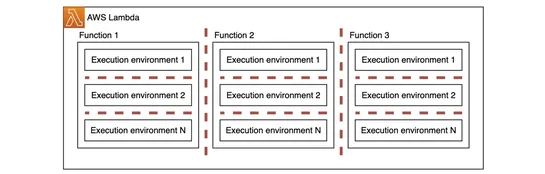
Seeing like an LLM
LLMs function as next-token predictors. With scant user context, they hallucinate—spinning fresh backstories. As these models morph into autonomous agents, context engineering—feeding facts, memory, tools, guardrails—halts rogue behavior. Trend to watch:A jump in context engineering. It pins LLMs t..