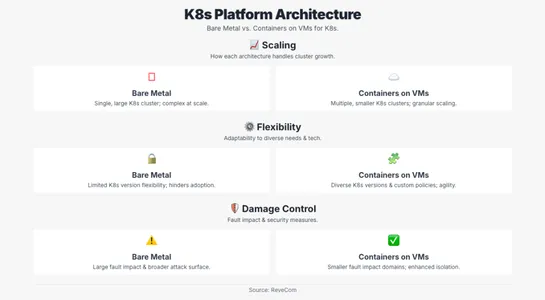
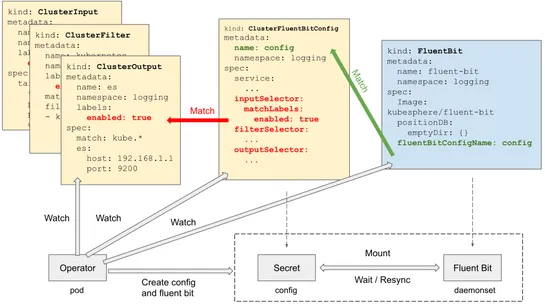
Kubernetes Image Builder Vulnerability Grants Root Access to Windows Nodes
A critical CVE-2025-7342 hauntsKubernetes Image Builder v0.1.44and earlier. It shipsNutanix/OVAimages with defaultWindows Administratorcreds intact. That slip-up invites root access on Windows nodes. Linux builds and other providers dodge this bullet. Mixed clusters run hot until images rebuild or p..