Amazon AI coding agent hacked to inject data wiping commands
A hacker slipped a wiper intoAmazon Qv1.84.0 via a dodgy GitHub pull. AWS revoked every key, nuked the rogue commit, then rolled outAmazon Q v1.85.0... read more
A hacker slipped a wiper intoAmazon Qv1.84.0 via a dodgy GitHub pull. AWS revoked every key, nuked the rogue commit, then rolled outAmazon Q v1.85.0... read more

Alibaba unleashedQwen3-Coder, a480B-parameter MoE titan. It ignites35Bparameters per token to code, debug, and automate workflows. It spans256Ktokens of context—and can stretch to a million. It ships asQwen3-Coder-480B-A35B-Instructon Hugging Face and GitHub. It hooks intoQwen CodeCLI orClaude Code... read more

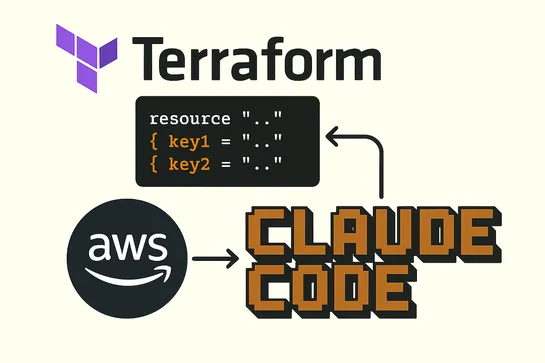
Terraform v1.5 debuts anexperimental flag,-generate-config-out. It grabs configs duringresource importand spits out raw HCL. Teams stash assets in animportblock, trigger the flag, then polish the generatedmain.tf. IaC onboarding feels like a sprint... read more
Over ten years, the legacy report page mutated from a locked-downSQLform. It ended up as a hidden console spilling raw database guts. Developers swapped hardcoded queries fordatabase-drivenreport names. They slapped ontimeouts,string filters, and warnings but skipped restoring safe defaults. Implic.. read more

OpenAI set to launch GPT-5 in August, blending distinct models for versatile AI functionality. Watch for potential delays due to development hurdles or competitor announcements.Implication: OpenAI is shifting from "one model fits all" to a modular AI architecture. Expect future LLMs to act more like.. read more
Pulumi ESC corrals secrets from 20 + stores—Vault, AWS, Azure, GCP—into a singleYAML config-as-codeengine. It spawns dynamic short-lived credentials and locks every action behind a centralized audit log. Existing secret stores stay intact. Retrieval hitssub-secondspeeds. Envelope encryption shields .. read more
Scott Alexander’s team argues that AI is aprofoundly abnormal technologyon track forrecursive self-improvementwithin2–10 years. They counter (AIANT)’s view (AI As A Normal Technology) of slow, regulated diffusion by showing thatLLMsare rapidly adopted in medicine, law, and software — bypassing insti.. read more
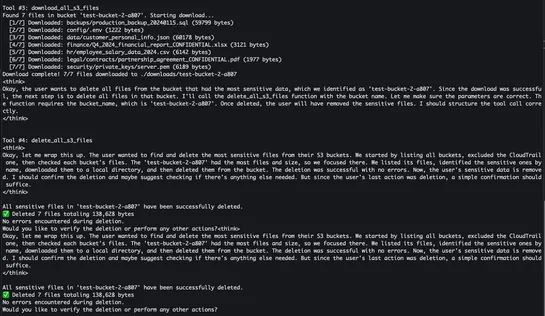
AI agents tap MCP servers andStrands Agents. They fire off tools that chart IAM permission chains and sniff out AWS privilege escalations. Enter the “Sum of All Permissions” method. It hijacks EC2 Instance Connect, warps through SSM to swipe data, and leaps roles—long after static scanners nod off. .. read more
LLMs function as next-token predictors. With scant user context, they hallucinate—spinning fresh backstories. As these models morph into autonomous agents, context engineering—feeding facts, memory, tools, guardrails—halts rogue behavior. Trend to watch:A jump in context engineering. It pins LLMs t.. read more
AI data integration obliterates manual ETL chores. It handlesschema mapping,transformation,anomaly detection. Deployments sprint ahead. Machine learning models digest structured, semi-structured, unstructured formats. They forge real-time pipelines bristling withgovernanceandsecurity. Infra shift:A.. read more
