Choosing the Right APM for Go: 11 Tools Worth Your Time
Explore 11 APM tools built for Go—from lightweight open-source options to enterprise-grade platforms that simplify debugging.
Explore 11 APM tools built for Go—from lightweight open-source options to enterprise-grade platforms that simplify debugging.

PostgreSQL 18 just hit stable. Big swing! Async IO infrastructureis in. That means lower overhead, tighter storage control, and less CPU getting chewed up by I/O. Adddirect IO, and the database starts flexing beyond traditional bottlenecks. OAuth 2.0? Native now. No hacks needed. UUIDv7? Built-in su.. read more
OpenAI’sAgent Builderdrops the guardrails. It’s a no-code, drag-and-drop playground for building, testing, and shipping AI workflows - logic flows straight from your brain to the screen. Tweak interfaces inWidget Studio. Plug into real systems with theAgents SDK. Just one catch: it’s locked behind P.. read more
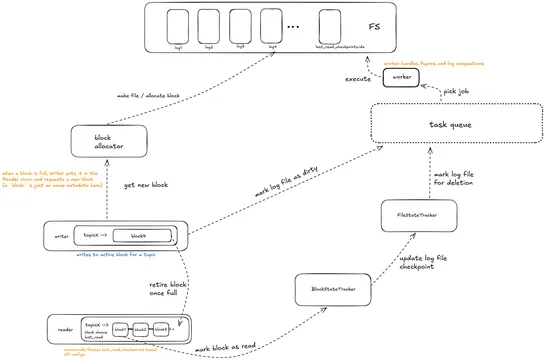
Walrusis a lock-free, single-nodeWrite Ahead Log in Rustthat rips through a million ops/sec and moves 1 GB/s of write bandwidth - on bare-metal, nothing fancy. It leans on mmap-backed sparse files, atomic counters, and zero-copy reads to get there. Each topic gets its own line of 10MB memory-mapped .. read more
SteamPipe just gutted its real-time storage engine and rebuilt it inRust. Expect faster performance and better scaling. Now runs oncolumnar storage, ships withvectorized queries, and rolls anobject store-backed WAL. Serious firepower for time series data. System shift:Another sign that high-throughp.. read more
A longtime AWS insider, Werner Vogels, breaks down the shift from slow-and-steady software growth to the generative AI rocket ride. Capabilities soared. Guardrails? Not so much. No docs, no handrails - just launch and learn. AWS didn’t chase the hype. It pulled a classic AWS move: doubled down on B2.. read more
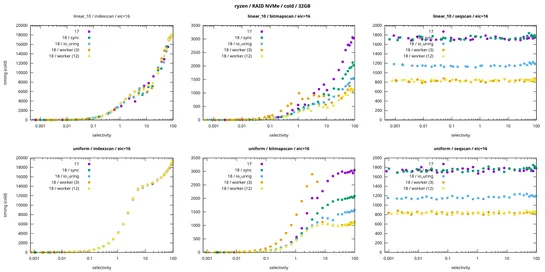
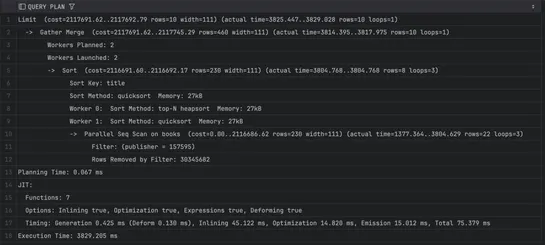
Advanced PostgreSQL tuning gets real results: composite indexes and CTEs can cut query latency hard when slicing huge datasets. AddLATERALjoins and indexed subqueries into the mix, and you’ve got a top-N query pattern that holds up—even when hammering long ID lists... read more
A researcher rolled their ownChromium forkwith a customDevTools Protocol (CDP) domain- not for fun, but to surgically probe browser internals. It reaches into Canvas, WebGL, and other trickier APIs, dodging the usual sandbox and spoofing all the bot blockers they'd rather you leave alone. It injects.. read more
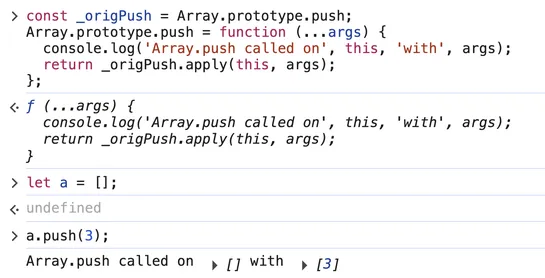
Modal cuts the drama out of deep learning ops. Devs write Python like usual, then fire off training, eval, and serving scripts to serverless GPUs - zero cluster wrangling. It handles data blobs, image builds, and orchestration. You focus on tuning with libraries like Unsloth, or serving via vLLM... read more

UiPath just droppedAgent Builder in Studio- a legit development environment for AI agents that can actually handle enterprise chaos. Think production-grade: modular builds, traceable steps, and failure handling that doesn’t flake under pressure. It’s wired forschema-driven prompts,tool versioning, a.. read more