Amazon AI coding agent hacked to inject data wiping commands
A hacker slipped a wiper intoAmazon Qv1.84.0 via a dodgy GitHub pull. AWS revoked every key, nuked the rogue commit, then rolled outAmazon Q v1.85.0... read more
A hacker slipped a wiper intoAmazon Qv1.84.0 via a dodgy GitHub pull. AWS revoked every key, nuked the rogue commit, then rolled outAmazon Q v1.85.0... read more

Terraform v1.5 debuts anexperimental flag,-generate-config-out. It grabs configs duringresource importand spits out raw HCL. Teams stash assets in animportblock, trigger the flag, then polish the generatedmain.tf. IaC onboarding feels like a sprint... read more
Over ten years, the legacy report page mutated from a locked-downSQLform. It ended up as a hidden console spilling raw database guts. Developers swapped hardcoded queries fordatabase-drivenreport names. They slapped ontimeouts,string filters, and warnings but skipped restoring safe defaults. Implic.. read more

The Gemini CLI on Windows bungled a failedmkdir. It flagged the error as success, then ranmovecommands. Files landed in a ghost folder and got overwritten. Data vanished. WindowsmkdirsetsERRORLEVELon failure.movetreats missing targets as rename directives. No exit-code checks. No read-after-write ve.. read more
OpenAI set to launch GPT-5 in August, blending distinct models for versatile AI functionality. Watch for potential delays due to development hurdles or competitor announcements.Implication: OpenAI is shifting from "one model fits all" to a modular AI architecture. Expect future LLMs to act more like.. read more
Pulumi ESC corrals secrets from 20 + stores—Vault, AWS, Azure, GCP—into a singleYAML config-as-codeengine. It spawns dynamic short-lived credentials and locks every action behind a centralized audit log. Existing secret stores stay intact. Retrieval hitssub-secondspeeds. Envelope encryption shields .. read more
Scott Alexander’s team argues that AI is aprofoundly abnormal technologyon track forrecursive self-improvementwithin2–10 years. They counter (AIANT)’s view (AI As A Normal Technology) of slow, regulated diffusion by showing thatLLMsare rapidly adopted in medicine, law, and software — bypassing insti.. read more
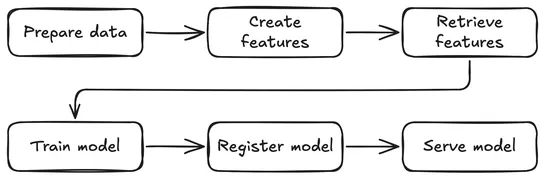
Post maps out aKubeflow Pipelinesworkflow onSpark,Feast, andKServe. It tackles fraud detection end-to-end: data prep, feature store, live inference. It turns infra into code, ensures feature parity in train and serve, and registers ONNX models in theKubeflow Model Registry... read more
Bugbot hunts bugs in PR diffs, flagging logic slip-ups and strange edge cases. It then detects security gaps, blending top LLMs with custom heuristics. It plugs into the Cursor dashboard and runs dedicated Bugbot rules.Beta stats: 1M+ reviews, 1.5M+ issues found. Half the bugs are fixed before merge.. read more
![[Cursor] Bugbot is out of beta](https://cdn.faun.dev/prod/media/public/images/cursor-bugbot-is-out-of-beta-1d97.width-545.format-webp.webp)
METRran an randomized controlled trial (RCT) with 16 open-source devs. They tackled real-world code tasks usingClaude 3.5andCursor Pro. The pitch:40%speed boost. Reality:19%slowdown. A deep dive into 246 screen recordings laid bare friction in prompting, vetting suggestions, and merging code. That .. read more