Intelligence Insights: April 2023
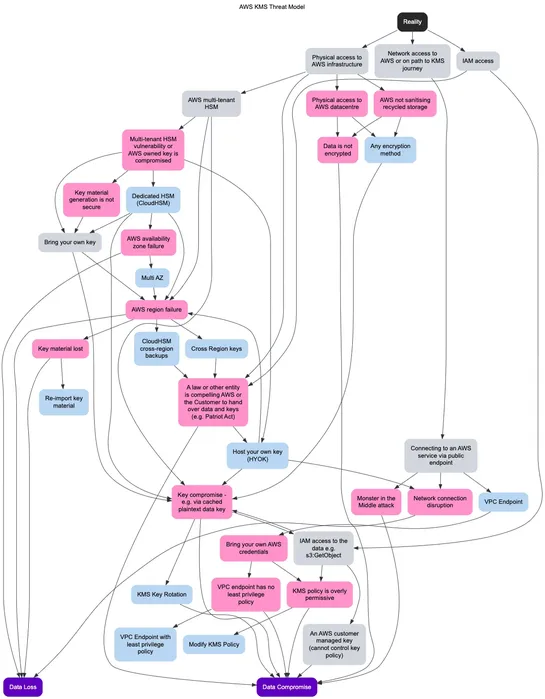
CrowdStrike's recent report reveals that the Labyrinth Chollima threat moved up in rank, with a significant increase in activity. The report also highlights a supply chain compromise involving malicious code in a softphone application. Defender preparation, detection, and response are key to reducin.. read more