The Hidden AWS Cost Traps No One Warns You About (and How I Avoid Them)
Calling outfive sneaky AWS cost traps—the kind that creep in through overlooked defaults and quiet misconfigs, then blow up your bill while no one's watching... read more
Calling outfive sneaky AWS cost traps—the kind that creep in through overlooked defaults and quiet misconfigs, then blow up your bill while no one's watching... read more

TheExternal Secrets Operator (ESO)is moving again. After hitting pause from maintainer burnout, it’s back under CNCF incubation—with a rebooted structure in place. New governance, clear contributor paths, and support tracks for CI, core dev, and testing are all in. But don’t expect fresh releases ju.. read more

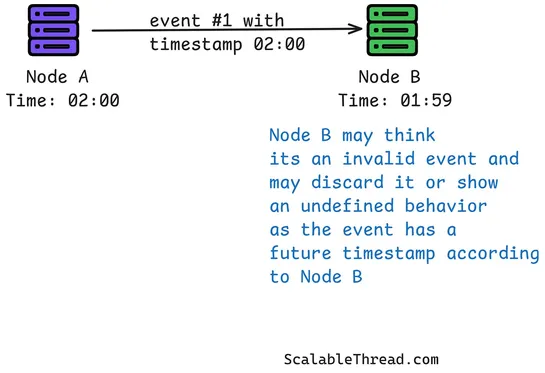
Logical clocks trackevent orderin distributed systems—no need for synced wall clocks. Each node keeps a counter. On every event: tick it. On every message: tack on your counter. When you receive one? Merge and bump. This flips the script. Instead of chasing global time, distributed systems lean int.. read more
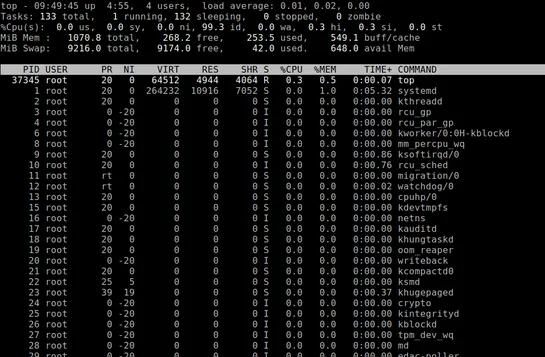
A fresh look at Linux monitoring tools shows the classics still hold—but the visual crowd’s moving in. Old-school command-liners liketopandvmstatremain go-to’s for quick reads. But picks likeNetdata,btop, andMonitbring dashboards, colors, and actual UX. Tools likeiftop,Nmon, andSuricatastretch deep.. read more
Rich Hickey’s classic “Simple Made Easy” talk is making the rounds again—as a mirror held up to dev culture under pressure. The punchline: we keep picking solutions that areeasy but tangled, instead ofsimple and sane. The essay draws a sharp line between that habit and a concept from biology: exapt.. read more
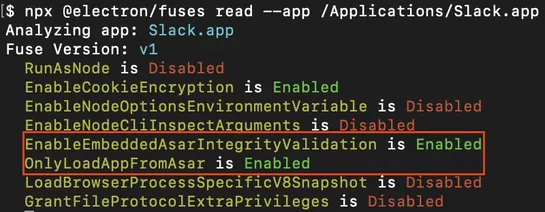
A fresh CVE (2025-55305) just put Electron apps in the hot seat. The bug? Chromium-based apps fail to treatV8 heap snapshot filesas potential attack vectors. That crack lets unsigned JavaScript slip past code signing and run inside heavyweight targets like Slack, 1Password, and Signal. The heart of.. read more
Klaviyo replaced ProxySQL on EC2 and moved toAWS RDS Proxy. Why? Less overhead. Simpler failovers. Smarter pooling. RDS Proxy handlesmultiplexing, packing thousands of client queries into way fewer DB connections. IAM access and built-in failover routing sweeten the deal... read more

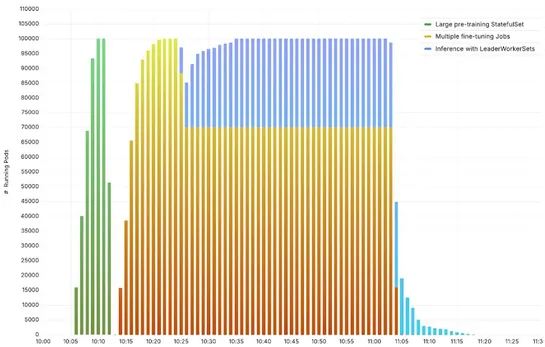
Amazon EKS just cranked its Kubernetes cluster limit to100,000 nodes—a 10x jump. The secret sauce? A reworkedetcdwith an internaljournalsystem andin-memorystorage. Toss in tightAPI server tuningand network tweaks, and the result is wild: 500 pods per second, 900K pods, 10M+ objects, no sweat—even un.. read more
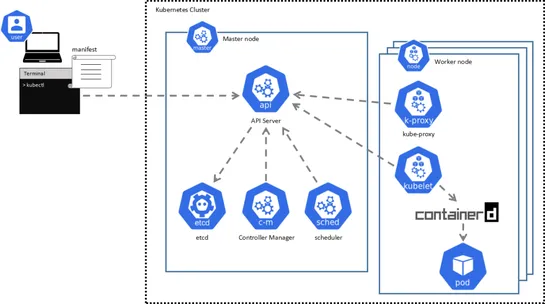
Nigel Douglas discusses the challenges of security in Kubernetes, particularly with traditional base operating systems. Talos Linux offers a different approach with a secure-by-default, API-driven model specifically for Kubernetes. CISOs play a critical role in guiding organizations through the shif.. read more
A new attack chain messes withKubernetes DNS resolutionandArgoCD’s certificate injectionto swipe GitHub credentials. With the right permissions, a user inside the cluster can reroute GitOps traffic to a fake internal service, sniff auth headers, and quietly walk off with tokens. What’s broken:GitOp.. read more