Post-Quantum Cryptography in Kubernetes
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses... read more
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses... read more
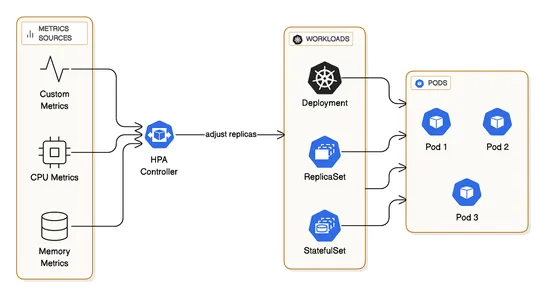
Horizontal Pod Autoscaler(HPA) cranks up pods based on CPU, memory, or custom quirks. A dream for stateless adventures, but you'll need a metrics server.Vertical Pod Autoscaler(VPA) fine-tunes CPU and memory for pods. Works like a charm for jobs where scaling out is sketchy, though it demands restar.. read more
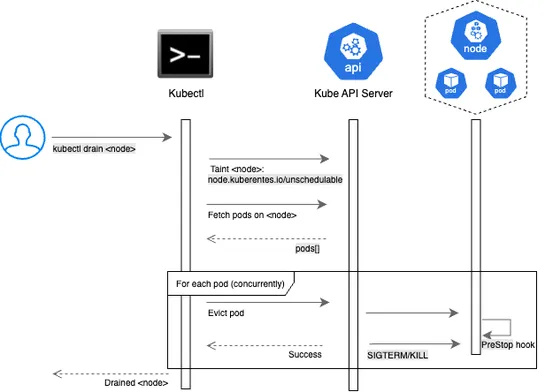
Eviction Reschedule Hooksticks its nose in Kubernetes eviction requests, letting operator-managed stateful apps wriggle their way through node drains without breaking a sweat. 🎯.. read more
Zendeskhas tossed out the old playbook with itsFoundation Interface. Forget the guessing games of infrastructure provisioning; engineers now scribble their demands in YAML, and voilà—magic happens. Kubernetes operators step in, spinning these requests into Custom Resources. It’s self-service nirvana.. read more

Red Hat OpenShift and NIC bonding for high availability is getting popular in data centers. Consider layer2/layer2+3 configurations for balanced traffic distribution across bonded links. Layer3+4 hashing offers highest throughput but may lead to out-of-order packets due to 802.3ad non-compliance. It.. read more
A cyberattack can strike at any time—causing operational disruption, financial loss, and reputational damage. Preparing for and effectively managing a cyber crisis is no longer optional—it's essential. At RELIANOID, we help businesses build robust cyber resilience through advanced solutions and expe..

Instrument NGINX with OpenTelemetry to capture traces, track latency, and connect upstream and downstream services in a single request flow.

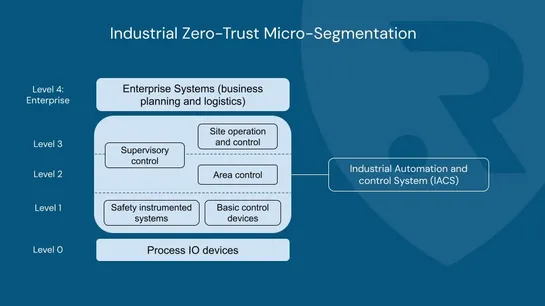
In today's connected industrial world, the convergence of IT & OT brings efficiency—but also new risks. That’s why Zero-Trust Micro-Segmentation is no longer optional. 📌 It divides your network into isolated zones, applies strict access rules, and assumes no user or device is inherently trusted. ✅ K..
Visualize AWS metrics like Lambda, API Gateway, and RDS in Grafana using Last9. No agents, no code, set it up in under 10 minutes.

📅 July 21–22 | 📍 Grand Hyatt at SFO Where business, tech, and innovation collide. Join us to explore the future of: 🔹 Internet, Mobile, AdTech, MarTech, SaaS 🔹 Live demos & emerging technologies 🔹 Real conversations with real innovators Let’s talk secure, high-performance solutions — and how RELIANO..
