QuickBooks Online Payment Integration
It permits to do online transactions while keeping other QuickBooks payment gateway options open to clients and customers can travel along to assist your SMBs.
It permits to do online transactions while keeping other QuickBooks payment gateway options open to clients and customers can travel along to assist your SMBs.

To implement an efficient database backup strategy, we need to learn the methods, understand the pros and cons, and then learn how to avoid pitfalls. Let’s see different backup methods that we can apply in our business to make it grow.

Explore the world of Cloud Computing - a revolutionary force in IT! Learn about its key concepts, deployment models, emerging technologies, and challenges.#CloudComputing#TechRevolution Discover how load balancers optimize cloud performance and availability by distributing traffic across multiple se..

🔒 Troubleshooting Authentication Token Manipulation Error in Linux User Passwords Encountering password change issues on your Linux system? Don't fret! Here's a quick guide to resolve the Authentication Token Manipulation Error. Keep your system secure and operational with these simple fixes! #Linu..

Join us at#QConLondon, a premier software development conference, for unparalleled learning and networking opportunities. With over 18 years of experience, QCon London guides senior software engineers, architects, and tech leaders in adopting the right patterns and practices. Explore emerging trends..

Discover essential strategies to boost your Incident Management efficiency. Learn about proactive monitoring, team integration, continuous training, and the importance of thorough documentation and continuous improvement.

How IMAP protocol works, what it’s used for, its pros and cons, and how to test it out efficiently.

Go is great for building command-line applications. There are many great tools available for creating command-line applications in Go. abiosoft/ishell is a solid choice for building interactive shells in Go... read more
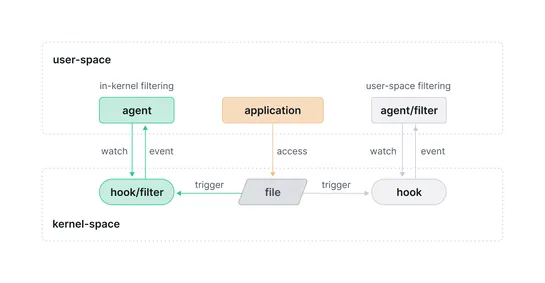
Tetragon's file monitoring capabilities use eBPF for in-kernel filtering and policy enforcement, going beyond traditional monitoring features. By implementing hooks into in-kernel functions like security_file_permission, Tetragon can track file accesses and perform FIM effectively. In-kernel filteri.. read more
The author shares their experience with reducing AWS expenses by migrating applications to a single ECS cluster and shared RDS instance, managing infrastructure with a Terraform mono-repo. They detail the setup, including Cloudflare, Rust services, DB migration with Golang-migrate, and Terraform usa.. read more
