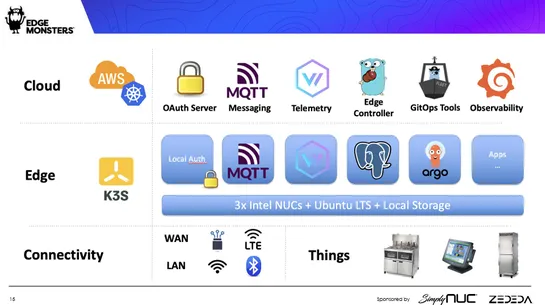
6 Design Principles for Edge Computing Systems
Edge systemseach have their eccentricities, needing solutions as unique as they are:Chick-fil-Aswears byKubernetesto herd its standard operations. TheAir Force, however, prizes nimbleness and ironclad security for deployments scattered across the globe. Smart edge management? It’s a mix ofInfrastruc..