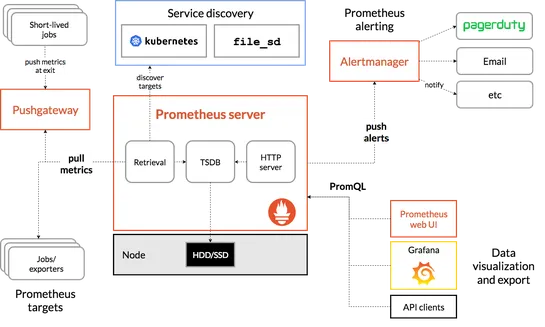
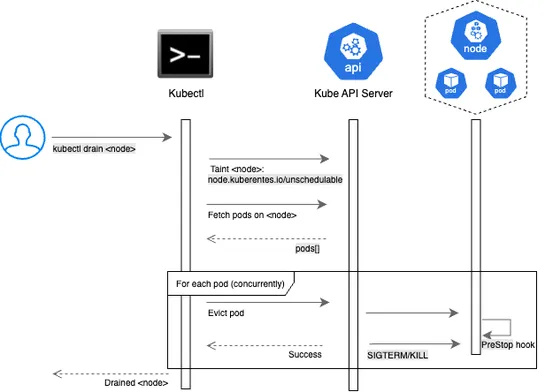
A four day hiking trip into ScreenshotOne infrastructure to solve an issue
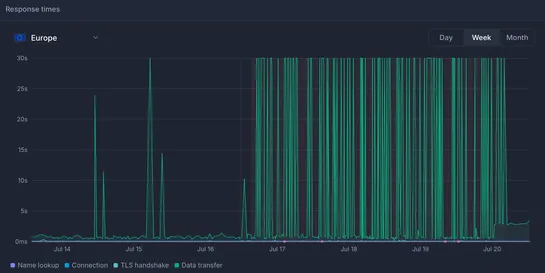
Misleading monitor alerts: Turns out, the villain wasexample.comblocking those pesky automated requests. No real service drama here. Just a wake-up call to tame those testing environments!..