The Hidden AWS Cost Traps No One Warns You About (and How I Avoid Them)
Calling outfive sneaky AWS cost traps—the kind that creep in through overlooked defaults and quiet misconfigs, then blow up your bill while no one's watching... read more
Calling outfive sneaky AWS cost traps—the kind that creep in through overlooked defaults and quiet misconfigs, then blow up your bill while no one's watching... read more

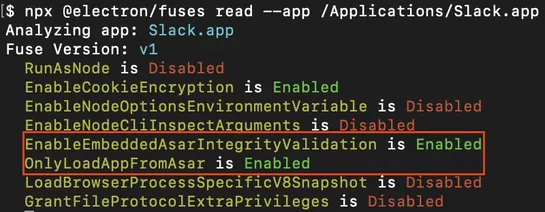
A fresh CVE (2025-55305) just put Electron apps in the hot seat. The bug? Chromium-based apps fail to treatV8 heap snapshot filesas potential attack vectors. That crack lets unsigned JavaScript slip past code signing and run inside heavyweight targets like Slack, 1Password, and Signal. The heart of.. read more
Klaviyo replaced ProxySQL on EC2 and moved toAWS RDS Proxy. Why? Less overhead. Simpler failovers. Smarter pooling. RDS Proxy handlesmultiplexing, packing thousands of client queries into way fewer DB connections. IAM access and built-in failover routing sweeten the deal... read more

Rich Hickey’s classic “Simple Made Easy” talk is making the rounds again—as a mirror held up to dev culture under pressure. The punchline: we keep picking solutions that areeasy but tangled, instead ofsimple and sane. The essay draws a sharp line between that habit and a concept from biology: exapt.. read more
TheExternal Secrets Operator (ESO)is moving again. After hitting pause from maintainer burnout, it’s back under CNCF incubation—with a rebooted structure in place. New governance, clear contributor paths, and support tracks for CI, core dev, and testing are all in. But don’t expect fresh releases ju.. read more

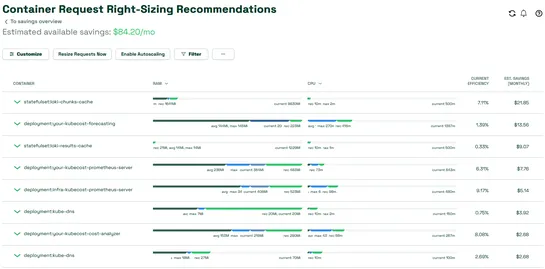
Kubecost’s Amazon EKS add-on now handlesautomated container request right-sizing. That means teams can tweak CPU and memory requests based on actual usage—once or on a recurring schedule. Optimization profiles are customizable, and resizing can be baked into cluster setup using Helm. Yes, that mean.. read more
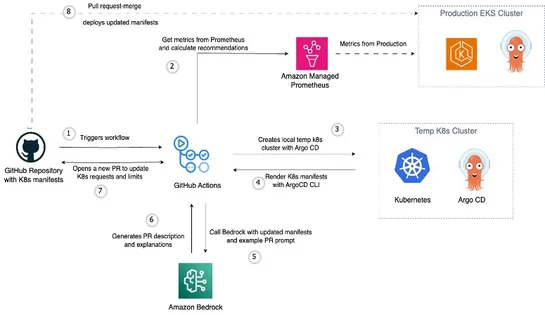
AWS just dropped a GitOps-native pattern for tuning EKS resources—built to runoutsidethe cluster. It’s wired up withAmazon Managed Service for Prometheus,Argo CD, andBedrockto automate resource recommendations straight into Git. Here’s the play: it maps usage metrics to templated manifests, then sp.. read more
Kubernetes'Vertical Pod Autoscaler (VPA)tries to be helpful by tweaking CPU and memory requests on the fly. Problem is, it needs to bounce your pods to do it. And if you're also runningHorizontal Pod Autoscaler (HPA)on the same metrics? Now they're fighting over control. VPA sees a narrow slice of .. read more

A new attack chain messes withKubernetes DNS resolutionandArgoCD’s certificate injectionto swipe GitHub credentials. With the right permissions, a user inside the cluster can reroute GitOps traffic to a fake internal service, sniff auth headers, and quietly walk off with tokens. What’s broken:GitOp.. read more
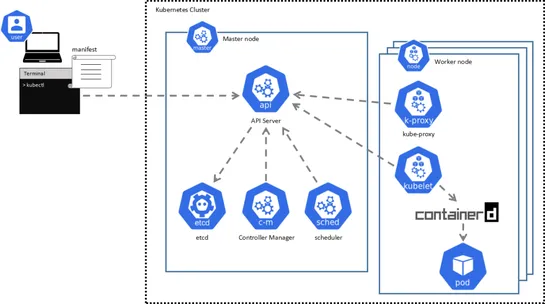
Older container technologies like Docker have been prone to security vulnerabilities, such as CVE-2019-5736 and CVE-2022-0847, which allowed for potential host system compromise. Podman changes the game by eliminating the need for a persistent background service like the Docker daemon, enhancing sec.. read more