Post-Quantum Cryptography in Kubernetes
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses... read more
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses... read more
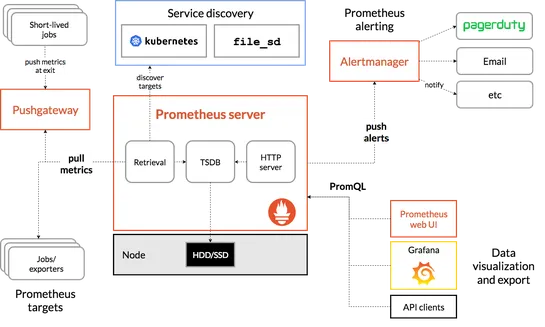
GitGuardian's 2024 reportsounds the alarm:23 million secrets slipped through leaks in 2023. A whopping 70% hung around for months. Talk about a security nightmare! EnterHashiCorp VaultandAkeyless. These tools mastered the multi-cloud juggling act and automated secrets management. Result? A satisfyin.. read more

Devtronis Kubernetes monitoring on overdrive. It ropes inPrometheusandGrafana, automates the pesky setup, and shoots real-time insights straight into a slick UI. Effort? Minimal. Results? Maximal... read more
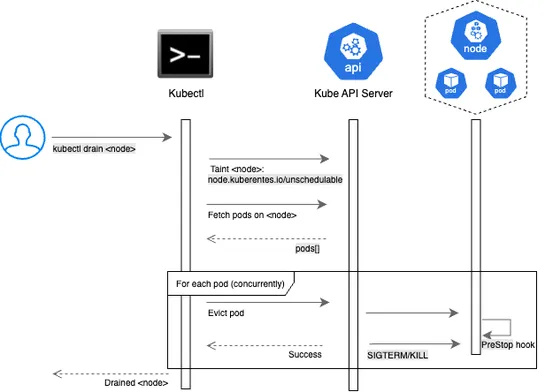
Eviction Reschedule Hooksticks its nose in Kubernetes eviction requests, letting operator-managed stateful apps wriggle their way through node drains without breaking a sweat. 🎯.. read more
Kubernetes 1.33rolls out with a security upgrade. It flips the switch onuser namespacesby default, shoving pods into the safety zone as unprivileged users. Potential breaches? Curbed. But don't get too comfy—idmap-capable file systems and up-to-date runtimes are now your new best friends if you want.. read more
Zendeskhas tossed out the old playbook with itsFoundation Interface. Forget the guessing games of infrastructure provisioning; engineers now scribble their demands in YAML, and voilà—magic happens. Kubernetes operators step in, spinning these requests into Custom Resources. It’s self-service nirvana.. read more

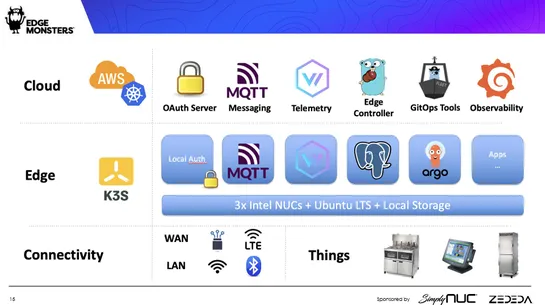
Edge systemseach have their eccentricities, needing solutions as unique as they are:Chick-fil-Aswears byKubernetesto herd its standard operations. TheAir Force, however, prizes nimbleness and ironclad security for deployments scattered across the globe. Smart edge management? It’s a mix ofInfrastruc.. read more
Kubernetes security tools usually drop the ball. Enter the dynamic duo:Tetragonwielding eBPF magic for deep observability, and smart notifications for sniper-precise alerts.Fluent Bitpairs withAzure Logic Appsin an automated setup so you can hunt down threats in real-time. Not a drop of sweat needed.. read more

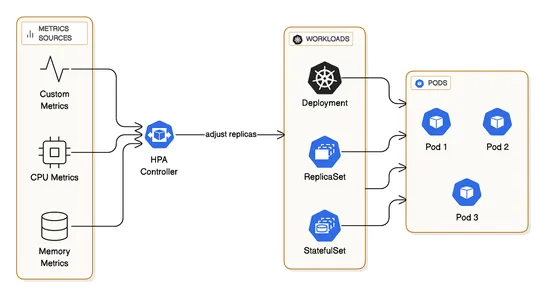
Horizontal Pod Autoscaler(HPA) cranks up pods based on CPU, memory, or custom quirks. A dream for stateless adventures, but you'll need a metrics server.Vertical Pod Autoscaler(VPA) fine-tunes CPU and memory for pods. Works like a charm for jobs where scaling out is sketchy, though it demands restar.. read more
A cyberattack can strike at any time—causing operational disruption, financial loss, and reputational damage. Preparing for and effectively managing a cyber crisis is no longer optional—it's essential. At RELIANOID, we help businesses build robust cyber resilience through advanced solutions and expe..
