Connect Codex to MCP Servers via MCP Toolkit
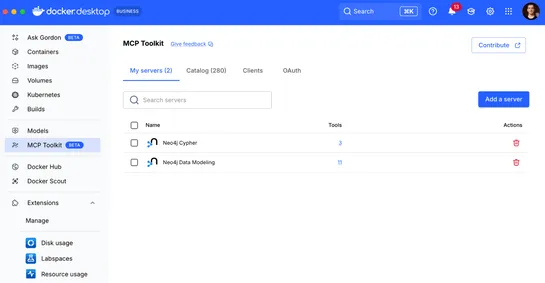
OpenAI Codex just leveled up. It now hooks into Docker’sModel Context Protocol (MCP) Toolkit, which means it can tap directly into 200+ infrastructure tools—likeNeo4j graph databases—as if they were built-in features. With MCP, Codex doesn’t just code. It runs containers, spins up data models, eats .. read more