What is Database Monitoring
Database monitoring tracks performance, health, and availability, helping detect issues early and maintain optimal operations.
Database monitoring tracks performance, health, and availability, helping detect issues early and maintain optimal operations.

June–August 2025 brought a surge in high-profile cyber incidents—from UNFI’s food supply disruption and Qantas’ customer data breach to sector-wide attacks on insurers. At the same time, AI-powered detection and new resilience features showed how fast response capabilities are evolving. At RELIANOID..

Learn how to seamlessly integrate Mailtrap with Windsurf to send transactional emails using simple AI prompts.
Japan has taken a bold step in reshaping its national cybersecurity posture with the new Active Cyberdefence Law (ACD) — a proactive response to the growing wave of cyber threats affecting critical infrastructure, airlines, and financial institutions. 🚨 Key highlights of the ACD Law: Legal authority..

Network Functions Virtualization (NFV) is transforming networking by moving critical functions like firewalls, routers, and load balancers from specialized hardware into software running on standard servers. This shift brings flexibility, scalability, and cost efficiency, enabling organizations to a..

At RELIANOID, security isn’t just a feature—it’s part of our foundation. Both our organization and load balancing platform are strongly aligned with the ISO/IEC 27001:2022 ISMS framework and its Annex A controls. This means our clients in finance, healthcare, public sector, and enterprise environmen..

Let’s not kid ourselves, Postmark is a great email service inalmostevery regard. However, if you’re reading this, the chances are that it doesn’t fit your needs anymore, and you’d like to switch it up a little bit. Luckily, you’ve come to the right place! I’ve interviewed our very own deliverability..
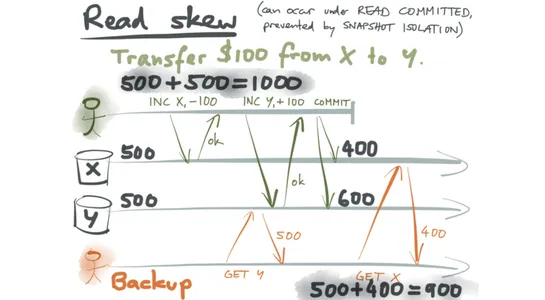
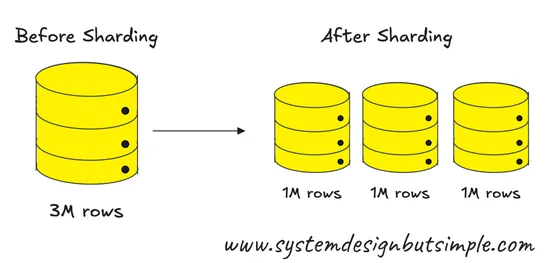
Sharding breaks a heavyweight database into bite-sized chunks spread across servers. That means better scalability, less strain on any one node. The key? Picking the right shard key. Get that wrong, and you’re in cross-shard query hell. Modulo, range, and consistent hashing each slice the pie diff..
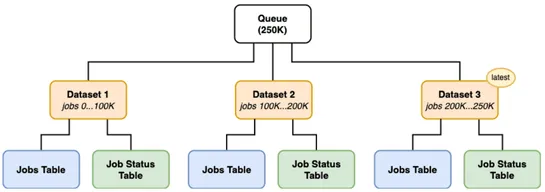
RudderStack crankedPostgreSQLup to100K events/secas a queuing engine. The secret sauce: tight tuning of job partitioning, smarter indexing, tuned VACUUM timing, and compaction that didn't choke. Recursive CTEs stood in for loose index scans. Caching cut I/O repeats. They ditched byte slices to side..
A sharp teardown ofWindows vs. Unix file deletion semanticslands on this: Windows leans on read-write locks; Unix rolls with a looser, non-blocking vibe—more likeweakly-isolated DB transactions. It trades consistency for concurrency, dodging locks even if it means the rules get fuzzy. The post zoom..