Post-Quantum Cryptography in Kubernetes
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses...
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses...
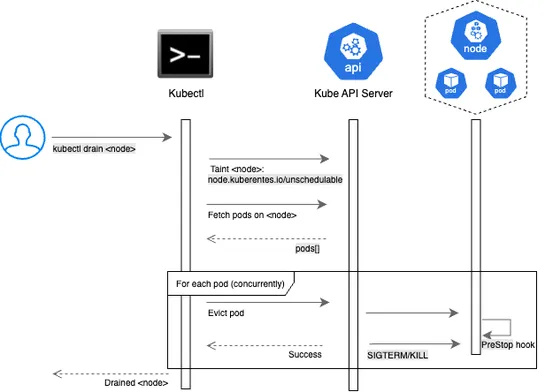
Eviction Reschedule Hooksticks its nose in Kubernetes eviction requests, letting operator-managed stateful apps wriggle their way through node drains without breaking a sweat. 🎯..
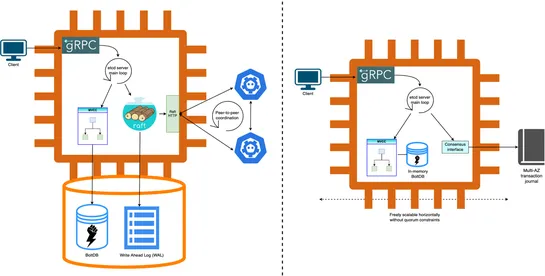
Amazon EKScranked up its gear—you can now spin up clusters with a staggering100,000 nodesat your beck and call. That’s a cozy home for either1.6 million AWS Trainium chipsor800,000 NVIDIA GPUs. Welcome to the playground for ultra-scale AI/ML. Performance soars skyward by ditching old etcd consensus ..
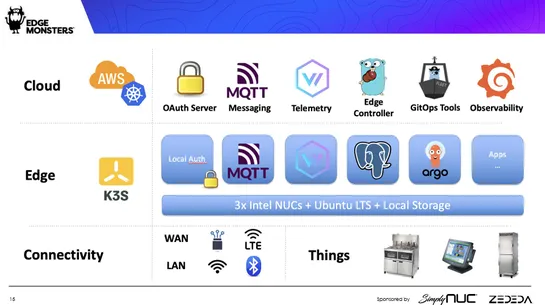
Edge systemseach have their eccentricities, needing solutions as unique as they are:Chick-fil-Aswears byKubernetesto herd its standard operations. TheAir Force, however, prizes nimbleness and ironclad security for deployments scattered across the globe. Smart edge management? It’s a mix ofInfrastruc..
Kubernetes 1.33rolls out with a security upgrade. It flips the switch onuser namespacesby default, shoving pods into the safety zone as unprivileged users. Potential breaches? Curbed. But don't get too comfy—idmap-capable file systems and up-to-date runtimes are now your new best friends if you want..
Red Hat OpenShift and NIC bonding for high availability is getting popular in data centers. Consider layer2/layer2+3 configurations for balanced traffic distribution across bonded links. Layer3+4 hashing offers highest throughput but may lead to out-of-order packets due to 802.3ad non-compliance. It..
Bitnamiclears out the virtual cobwebs by tucking its oldDebian-based imagesinto a digital time capsule, also known as theLegacy repository. It throws a friendly nudge to devs: get with the times and swap to the "latest" images. In production-ville, serious users should hitch a ride on theBitnami Sec..
A cyberattack can strike at any time—causing operational disruption, financial loss, and reputational damage. Preparing for and effectively managing a cyber crisis is no longer optional—it's essential. At RELIANOID, we help businesses build robust cyber resilience through advanced solutions and expe..

Instrument NGINX with OpenTelemetry to capture traces, track latency, and connect upstream and downstream services in a single request flow.
