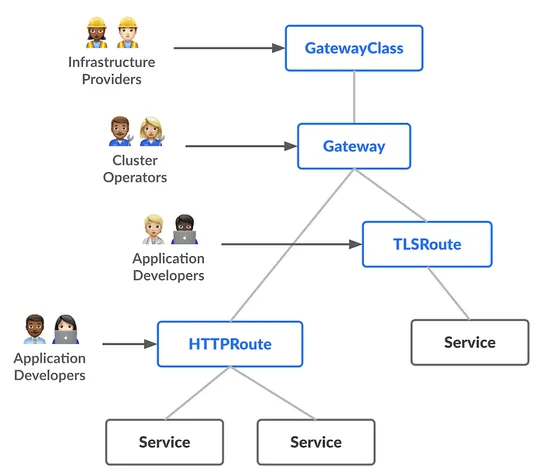
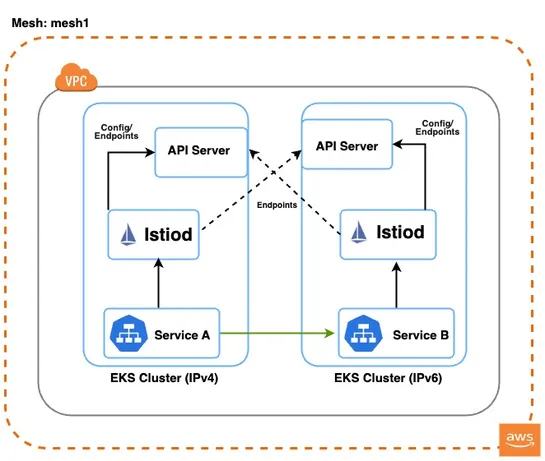
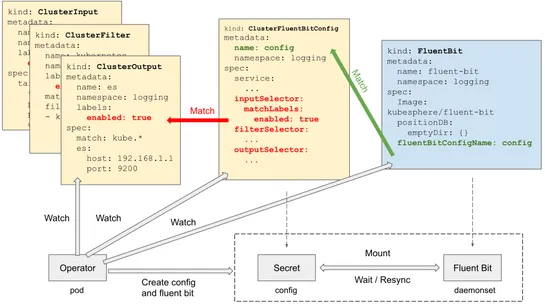
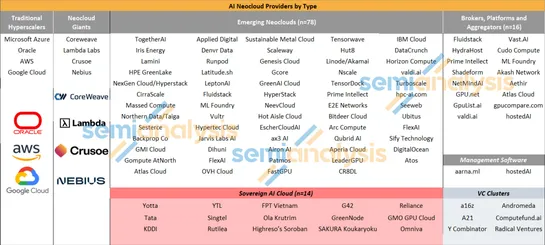
Critical Container Registry Security Flaw: How Multi-Architecture Manifests Create Attack Vectors
ContainerHijack hijacksDocker Image Manifest V2 Schema 2. It taints images inDocker Hub,Amazon ECR,GCR. Scanners shrug. Signature checks buckle. Defenders deploypolicy-as-code admission controllers. They lock down Terraform ECR push policies.Falco rulesflag strange layers, ghost pushes, rogue proces.. read more