DevOps vs Agile: Which one is going to win?
In the ongoing debate of DevOps vs Agile, this blog post delves deep into the key differences, benefits, and challenges of each method for long-term success.
In the ongoing debate of DevOps vs Agile, this blog post delves deep into the key differences, benefits, and challenges of each method for long-term success.

Transfering 1 billion rows of data from a Postgres database to Snowflake involves challenges like data integrity, error recovery, and cost optimization. Techniques such as using open-source tools, parallel processing, and data compression can help minimize costs and improve performance. With careful.. read more

Google has launched an AI-powered open-source project called Magika for filetype identification with a claimed outperformance of traditional tools. The tool is already being integrated with security-focused services like VirusTotal for analyzing suspicious files and URLs... read more

Over the past few years, I used the Censys API to track the number of Kubernetes clusters exposed on the internet. The latest scan showed an increase in the number of clusters with visible version numbers, indicating a significant adoption of Kubernetes among operators... read more

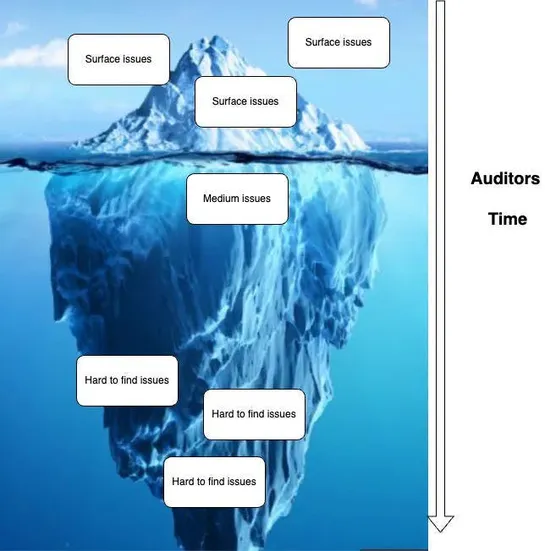
The article discusses the synergy between bug bounties and audits, their importance, and introduces Hexens.io's project, Remedy, aiming to enhance decentralized security through innovative tools and a comprehensive security ecosystem. It highlights the significance of community engagement in identif.. read more
Discover the top 8 artificial intelligence trendsfor businesses in 2024 to stay proactive and harness the huge potential of AI for a growing future.

Implementation
Fortify SCA executes it vulnerability test by looking at the JAVA pom.xml file which contains all the dependencies. As the scanning is performed at the code level, the best practice is that it is performed as early as possible. This is achieved by running the scan after the code checkout, as to stop further processing of the build in case vulnerabilities are detected.


Mass email marketing is easy. It’s like eating, except you’re eating soup with a fork in the middle of a zombie apocalypse 🔥.
But, luckily, there’s one thing that can alleviate your struggles and simplify the task – a reliable mass email service provider.
We scraped the market to find the best contenders and compared them based on key features, use cases, pricing, and other criteria. Let’s dive in!
