We reported a security issue in AWS CDK's eks.Cluster component
Two sleuthing SREs uncovered an AWS security issue. Here's how they found it, why it matters, and what you need to do to resolve it... read more
Two sleuthing SREs uncovered an AWS security issue. Here's how they found it, why it matters, and what you need to do to resolve it... read more

A Progess Software study found that many companies still don't understand DevSecOps, but they know securing their systems is a must... read more
New tools, a pre-built Hyper-V image, a new audio stack, and more!.. read more

An analysis reveals striking similarities between the BlackSuit and Royal ransomware strains... read more
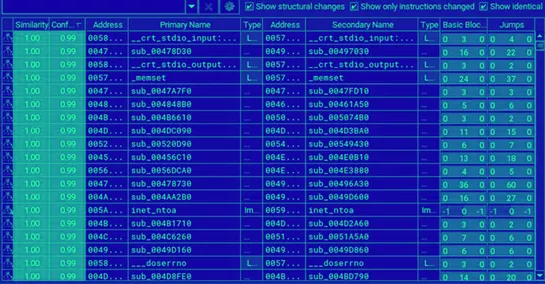
A look at how cgroups are used in Linux and container systems.. read more
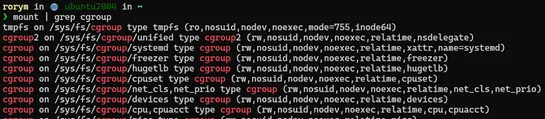
Find out how object lock can help prevent an object version from being modified or deleted to help combat ransomware attacks... read more
Learn how to use static application security testing (SAST) in your CI/CD pipelines to identify security vulnerabilities early in development and reduce risk... read more

Few articles exist on alerting strategies, but this article aims to fill that gap by sharing valuable knowledge on developing a robust alerting system... read more
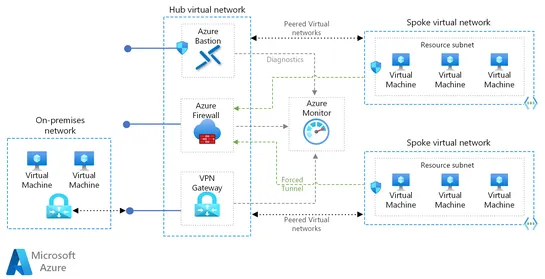
Azure DevOps CI/CD Pipeline with Terraform: a quick tutorial... read more
Azure Data Explorer now supports the ingestion of data from .NET Applications via theNLog sink... read more