Top 9 Web Application Performance Monitoring Tools for 2025
Explore 2025’s top APM tools — from open-source stacks to enterprise platforms — and see how each helps you monitor smarter.
Explore 2025’s top APM tools — from open-source stacks to enterprise platforms — and see how each helps you monitor smarter.

The Cloud Native Computing Foundation launched the Certified Kubernetes AI Conformance Program to set standards for AI workloads on Kubernetes, ensuring reliability and consistency.

OpenAI announces GPT-5.1, enhancing ChatGPT and OpenAI APIs with improved intelligence and conversational abilities, offering two models for better reasoning and personalization, initially for paid users.
Debian 13.2 Trixie, released on November 25th, 2025, offers significant updates, new software packages, and supports multiple architectures, emphasizing versatility for desktops and servers.

GitHub introduces Raptor mini for Copilot in VS Code, expanding AI capabilities for Pro and Free users.
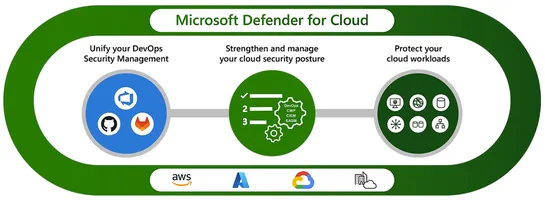
Microsoft Defender for Cloud enhances Kubernetes security with new features, updates container vulnerability re-scan policies, and expands support for Jfrog Artifactory and Docker Hub.
We are thrilled to announce that 𝗢𝗫𝗬 𝗦𝗼𝗹𝘂𝘁𝗶𝗼𝗻𝘀 — 𝘔𝘢𝘭𝘢𝘺𝘴𝘪𝘢’𝘴 𝘕𝘰.𝟭 𝘛𝘦𝘤𝘩𝘯𝘰𝘭𝘰𝘨𝘺 𝘚𝘰𝘭𝘶𝘵𝘪𝘰𝘯 𝘗𝘳𝘰𝘷𝘪𝘥𝘦𝘳 — is now RELIANOID’s exclusive partner in Malaysia. This week, we had the pleasure of welcoming part of the 𝗢𝗫𝗬 𝗦𝗼𝗹𝘂𝘁𝗶𝗼𝗻𝘀 𝘁𝗲𝗮𝗺 𝘁𝗼 𝗦𝗲𝘃𝗶𝗹𝗹𝗲, where we shared valuable discussions about the future, explored new..

📍 November 18 | The Glasshouse, Gateshead RELIANOID joins top experts and leaders at this one-day event to explore the UK’s evolving cyber defence strategy — from AI-driven threats to major breach lessons. Meet our team and discover how we strengthen digital resilience with intelligent ADC and secur..

Are you passionate about technology, networking, and innovation? At RELIANOID, we’re building cutting-edge solutions that power secure, scalable, and reliable infrastructures — and we’re looking for talented people to join us on this journey! - Whether you’re an experienced professional or just star..