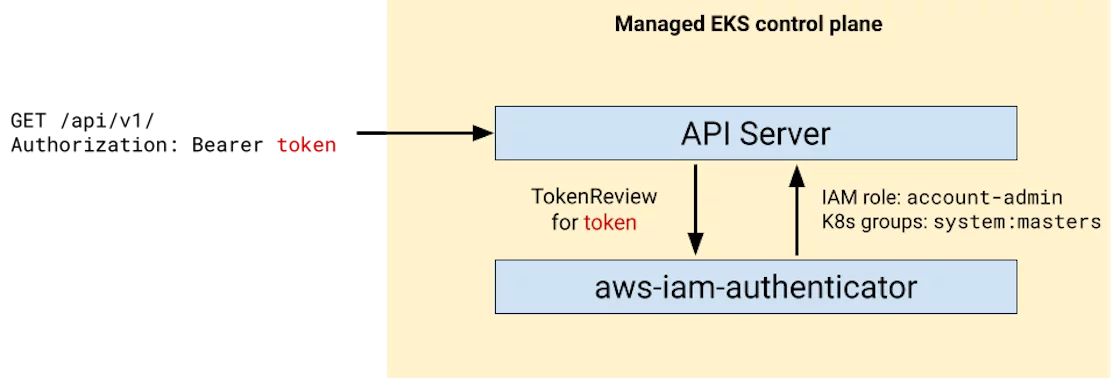
The post discusses authentication and authorization in Amazon Elastic Kubernetes Service (EKS). It explains how EKS authenticates requests and authorizes access using IAM. It also explores attack vectors like SSRF vulnerabilities and stealing pod identities. The defender-focused section covers preventing pod access to node credentials and auditing with MKAT.
Give a Pawfive to this post!
Start writing about what excites you in tech — connect with developers, grow your voice, and get rewarded.
Join other developers and claim your FAUN.dev() account now!















