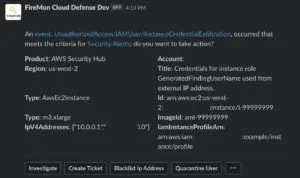
AWS has released new policy options to secure instance credentials and reduce the risk of attackers stealing and abusing them.
- There are multiple techniques for containing compromised instance credentials, but the easy ones are most likely to break things.
- More creative options are available to lock out attackers without breaking applications, such as revoking active sessions or adding a VPC endpoint.
- However, containing IAM credentials is nuanced, and there are unexpected behaviors when IAM service interacts with Instance Metadata Service (IMDS) and SDKs.
- A firm foundation in core principles can be used in other situations.