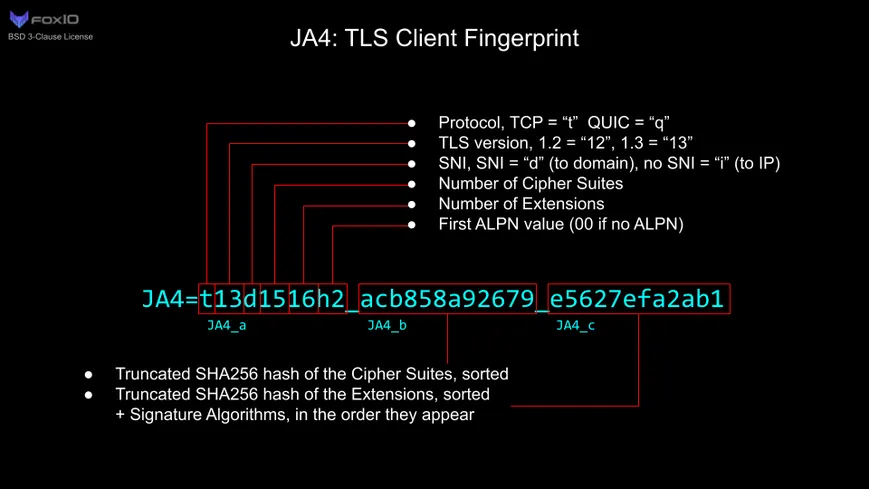
A developer built a razor-sharp TLS fingerprinting and blocking tool - all in kernel space - with eBPF and XDP. It hooks into incoming packets, scrapes TLS Client Hello messages, and cranks out simplified JA4-style hashes from their cipher suite lists.
The fun part? It's running under tight stack limits, so the dev stuffed a custom O(n²) sort into the hash logic. Yeah - bubble-sort energy, in 2024. But it fits. For state management, it leans on eBPF maps as on-the-fly blacklists. No stack overflows. No userspace detours.
System shift: This isn’t just clever - it’s a trend. Real-time packet filtering is moving down the stack. Kernel-level signals. No more babysitting by bloated firewalls or load balancers.