Threat group UNC3944 uses SIM swapping to breach BPOs and telecoms, then leverages Microsoft Azure Serial Console to install remote admin tools within the compromised environment.
Mandiant warns that cloud resources are often poorly understood and vulnerable to attackers, emphasizing the need for stronger security measures to prevent attacks.
- The group utilizes SIM-swapping attacks to breach telecommunications and business process outsourcing (BPO) companies.
- They employ a loader named STONESTOP and a malicious signed driver called POORTRY to carry out BYOVD (Bring Your Own Vulnerable Device) attacks.
- The initial access methodology involves SMS phishing messages targeting privileged users to obtain their credentials and then conducting a SIM swap.
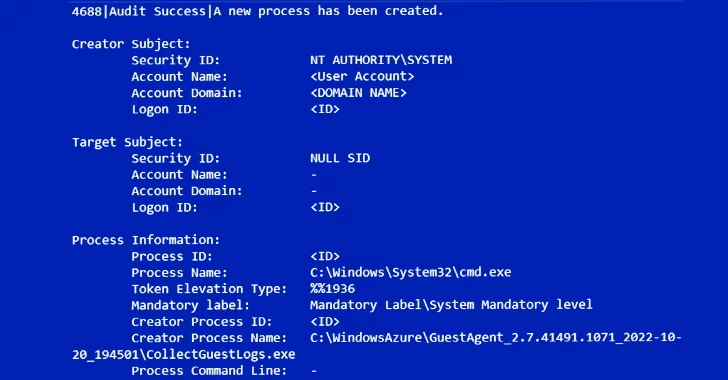
- Once inside the compromised environment, the threat actors exploit Azure VM extensions such as Azure Network Watcher, Azure Windows Guest Agent, VMSnapshot, and Azure Policy guest configuration for further reconnaissance.
- UNC3944 uses the serial console functionality to gain administrative access and deploys legitimate remote administration tools using PowerShell.