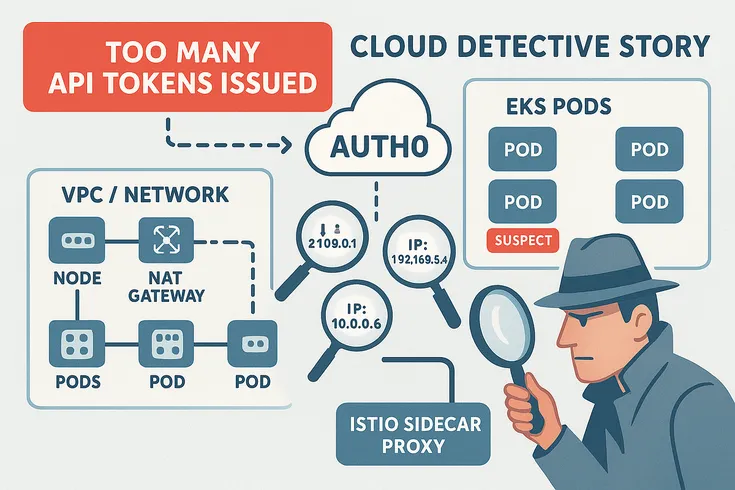
A production network got hammered by too many Auth0 token requests. The source? EKS workloads tucked behind a shared NAT Gateway. No easy trail.
Engineers stitched it together using VPC Flow Logs, pod-to-node maps, and some sharp Istio ServiceEntry logs. Even with Kubernetes CNI doing its NAT-obscuring thing, they pinned the blame on the exact pod.