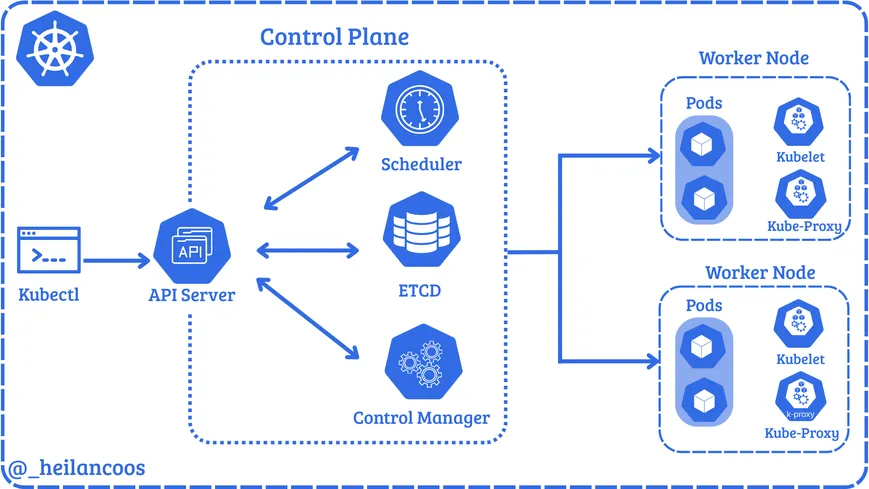
A sharp teardown of Kubernetes’ attack surface maps out where things go sideways: pods, the control plane, RBAC, admission controllers, and etcd. Misconfigurations like anonymous API access, wildcard roles, and hostPath mounts aren't just sloppy- they're attack vectors.
Fixes? Think Falco, RBAC lockdowns, API hardening, and mutating admission controls. Defense-in-depth with actual depth.