TL;DR
GitLab's team discovers a large-scale npm supply chain attack with malware that spreads through npm packages, threatening data destruction if disrupted.
Key Points
Highlight key points with color coding based on sentiment (positive, neutral, negative).A large-scale npm supply chain attack has been identified, involving a malware variant that spreads through npm packages.
The malware features worm-like propagation, credential harvesting, and a "dead man's switch" that threatens data destruction if disrupted.
The malware propagates by automatically infecting other npm packages maintained by affected developers.
The malware attempts to harvest credentials from GitHub, npm, AWS, GCP, and Azure.
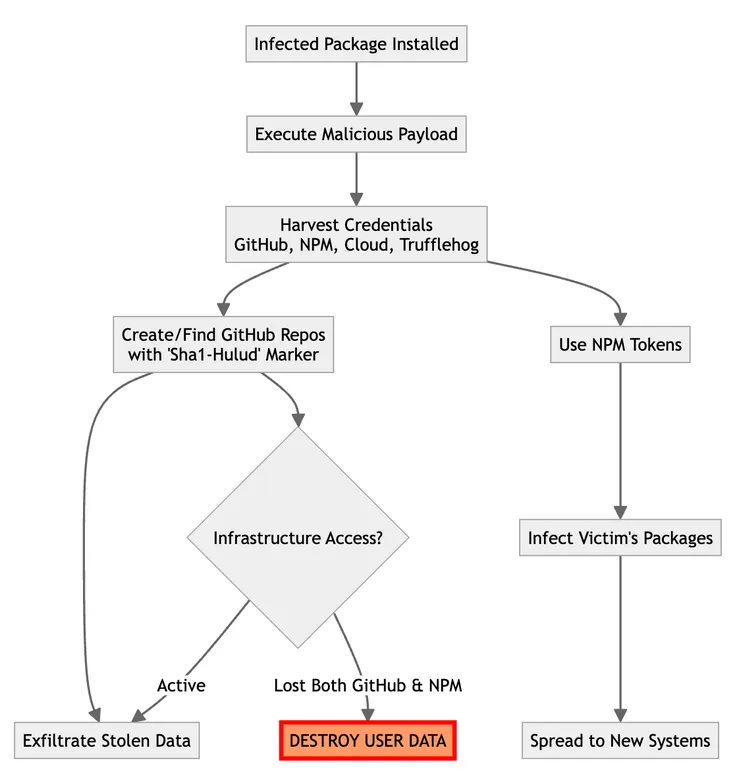
GitLab's Vulnerability Research team has discovered a pretty alarming npm supply chain attack. This isn't just any malware - it's a sophisticated variant of "Shai-Hulud," and it's causing quite a stir. The malware spreads through npm packages, and it's got a nasty habit of worming its way into systems, harvesting credentials, and even packing a destructive "dead man's switch."
How does it work? It automatically infects more packages maintained by developers who've been hit, using stolen npm tokens to download, tweak, and republish packages with malicious scripts. The whole thing kicks off with a seemingly harmless script, setup_bun.js, which sets up the malware's execution environment.
How this malware goes about its dirty work? It's on the hunt for credentials from all sorts of places - GitHub, npm, AWS, GCP, and Azure, to name a few. It digs through environment variables and configuration files, and even uses tools like Trufflehog to sniff out secrets. Once it gets its hands on this data, it sends it off to attacker-controlled GitHub repositories. These repositories are marked with a specific identifier, making it easy for attackers to retrieve compromised tokens. It's like a web of infected systems, all interconnected and ready to do the attackers' bidding.
One of the more chilling aspects of this malware is its "dead man's switch." This feature is designed to protect the malware's infrastructure by monitoring access to GitHub and npm. If both channels go dark, it triggers data destruction on infected systems. This is a big deal because if there's a mass takedown, it could lead to widespread data loss across all the compromised machines.
GitLab, for its part, has confirmed that it's not using any of these malicious packages. They're sharing their findings to help the security community tackle this threat head-on. The investigation is still ongoing, as they work to understand the full scope of the campaign and come up with safe ways to remediate the situation.
Key Numbers
Present key numerics and statistics in a minimalist format.The number of npm packages backdoored by the Shai-Hulud 2.0 worm
The total weekly downloads of the compromised npm packages (according to DataDog Security Labs)
The minimum estimated number of GitHub users whose data was exfiltrated (according to DataDog Security Labs)
The minimum number of GitHub organizations impacted through exfiltrated credentials
Stakeholder Relationships
An interactive diagram mapping entities directly or indirectly involved in this news. Drag nodes to rearrange them and see relationship details.Organizations
Key entities and stakeholders, categorized for clarity: people, organizations, tools, events, regulatory bodies, and industries.GitLab's Vulnerability Research Team discovered the npm supply chain attack and is actively involved in analyzing and sharing information about the threat.
Tools
Key entities and stakeholders, categorized for clarity: people, organizations, tools, events, regulatory bodies, and industries.The npm package manager is the medium through which the malware spreads, affecting the JavaScript ecosystem.
Industries
Key entities and stakeholders, categorized for clarity: people, organizations, tools, events, regulatory bodies, and industries.The cybersecurity industry is involved in understanding the threat, developing mitigation strategies, and protecting against future attacks.
The software development industry, particularly those using npm packages, is directly impacted by the supply chain attack.
Additional Resources
Enjoyed it?
Get weekly updates delivered straight to your inbox, it only takes 3 seconds!Subscribe to our weekly newsletter DevOpsLinks to receive similar updates for free!
Give a Pawfive to this post!
Start writing about what excites you in tech — connect with developers, grow your voice, and get rewarded.
Join other developers and claim your FAUN.dev() account now!
FAUN.dev()
FAUN.dev() is a developer-first platform built with a simple goal: help engineers stay sharp withou…

DevOpsLinks #DevOps
FAUN.dev()
@devopslinksDeveloper Influence
18
Influence
1
Total Hits
132
Posts



















