Configurations
Configurations are attributes needed by an application when it runs. These configurations are values which are used frequently across the application. They may be used to provide dynamic behavior of an application based on customer, geographical region, language and locale. Frequently used configurations are database url, username, password, etc. These values are not hardcoded along with the application code as they may change depending on different factors.
There is a 12 Factor recommendation which advises to separate configuration out of code. Now the question arises if configurations are to be separated from code, how the application will access them during runtime. The answer is PLATFORM. Platform meaning the system on which the application runs. The configurations would be added on the platform as environment variables.
To execute the examples given in the artcle, you must be using a Linux system having connected to a Kubernetes cluster via kubectl tool. This is the prerequisite.
Configurations in Kubernetes
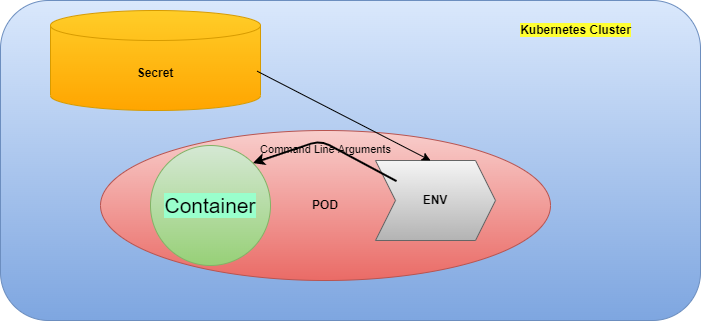
Application workloads run on Kubernetes Pods. If a developer is transforming his application to run on Kubernetes, he must use Kubernetes ConfigMaps and Secrets to store configurations which then could be injected into Pods to be consumed by applications running inside the Pod.
ConfigMap
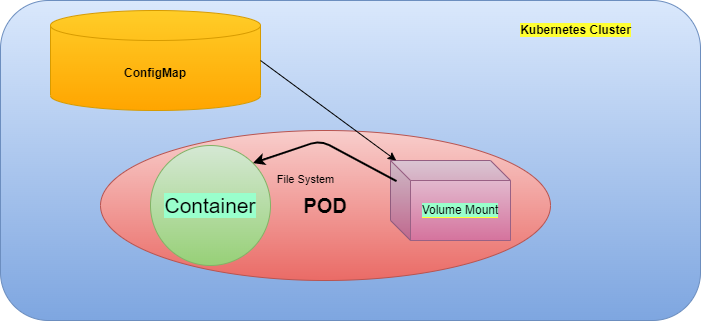
ConfigMap is a Kubernetes API object which stores data in form of a set of name and value pairs. It stores non-confidential data to be used by application workloads. It stores data upto 1 Mb.
ConfigMaps could be used inside a Pod in below 3 ways.
- As a container command argument
- As an environment variable in container
- As a volume inside container
Below examples shows the above three use cases.
Usage of ConfigMaps
Before we use a configmap in a Pod we have to first create it. ConfigMaps could be created using command line (kubectl commands) or using manifest files.
Create ConfigMap
ConfigMap could be created in varieties of ways. We can create it using a manifest file with a ConfigMap spec. We can create it using kubectl create configmap command with literal, files option.