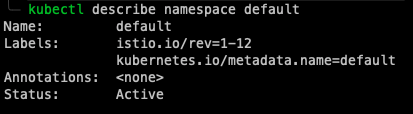
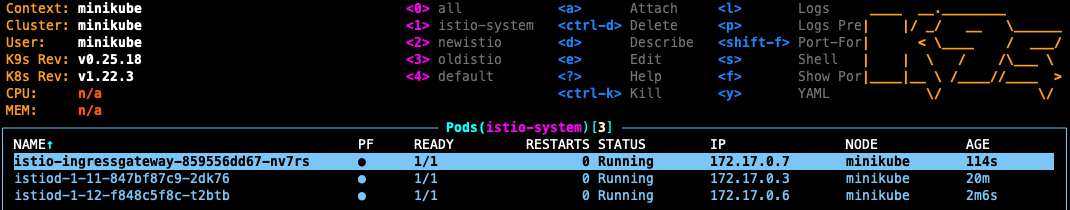
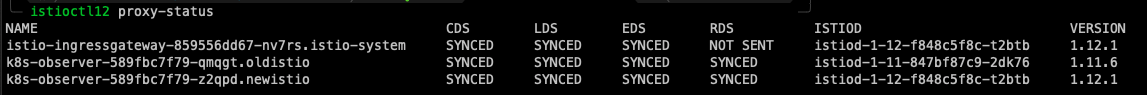
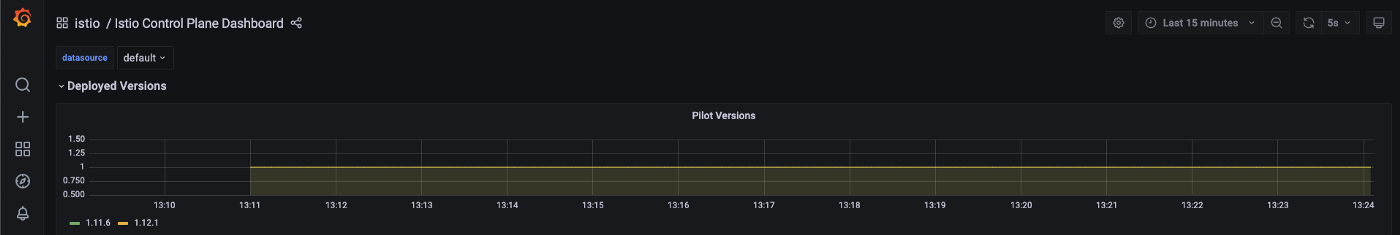
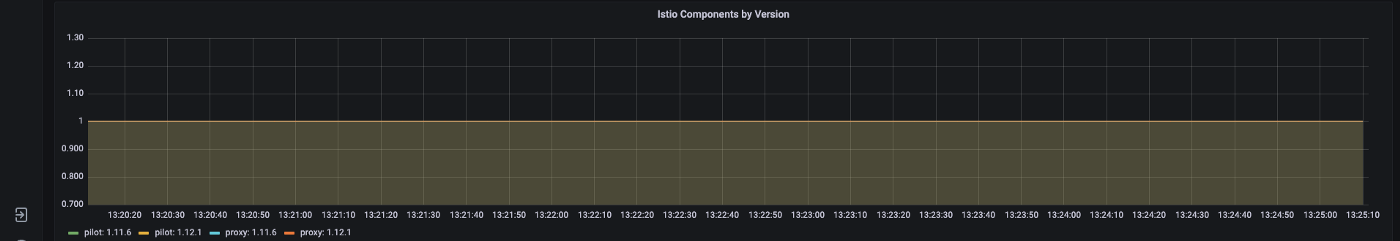
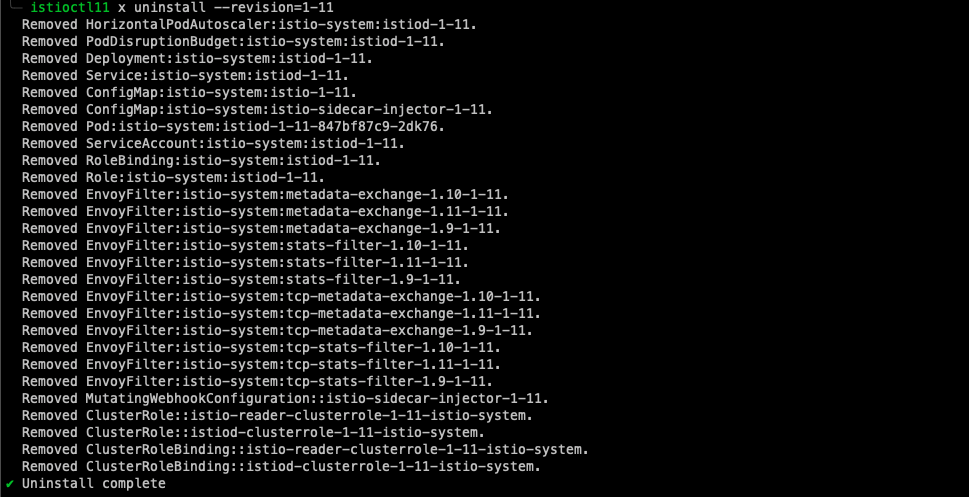
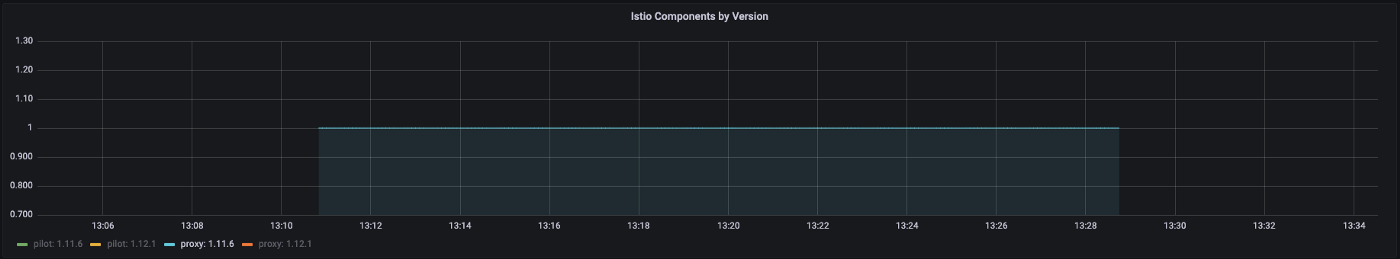
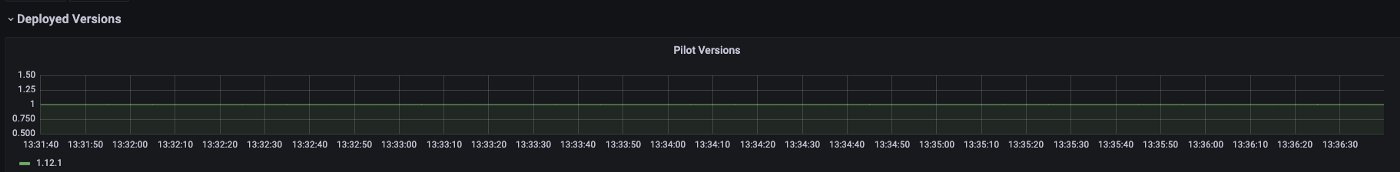
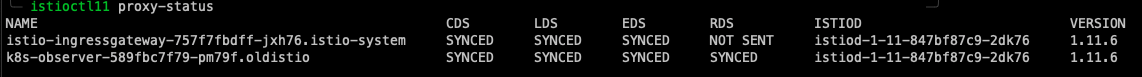By checking our Dashes, we can see clearly that our version 1.11.6 components are no more alive as our 1.12.1 components have taken their place, and our upgrade was nice and smooth.
Final conclusions
What’s so good about this?
The cool thing here is, whenever you want to do a Istio upgrade on your cluster, you can create a new namespace to do things smoothly, kind of thinking in a Canary way, which is awesome.
Also, by having Grafana to aid you on this task, you can monitor everything that is going on during your upgrade.
What’s the big difference against the istio-injection=enabled label method?
If we had labeled our namespaces using istio-injection, in the exact moment we applied the new Istio version, every Pod on namespaces with such label would start to inject the new version sidecar after restart, and then we would lose control on our rolling updates.
What are the downsides?
The downside here is a general downside on Istio upgrades.
Whether using istio.io/rev label or istio-injection, we would get a slight downtime in our istio-ingressgateway during our upgrade (remember when we talked about it earlier? That's it), which may cause some serious problem if not made with proper attention and care.
Saying again
To run such tools on your production environment, don't forget to read the proper documentation and set everything as we discussed before.
For example, when installing Istio in your production cluster you can (and you should!!) use the revision attributes to enable smooth rolling upgrades, but you also have to be extremely careful when configuring Istio profiles, log levels and more.
Thank you!
Thanks for reading this article (which is my first article, btw) and I hope it helps you on your journey!
References
- https://blog.chesterwood.io/2019/11/istio-now-released.html
- https://istio.io/latest/docs/setup/upgrade/canary/