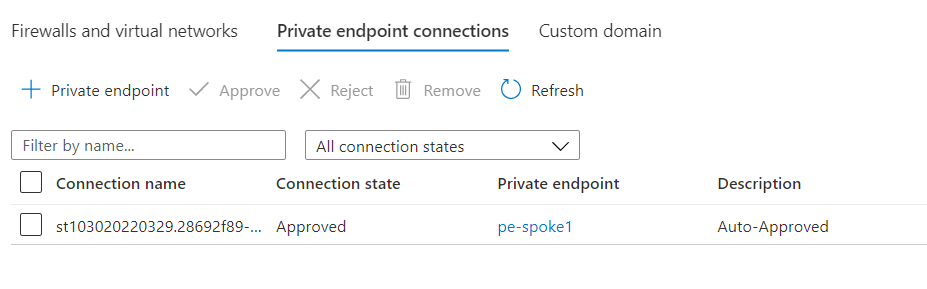
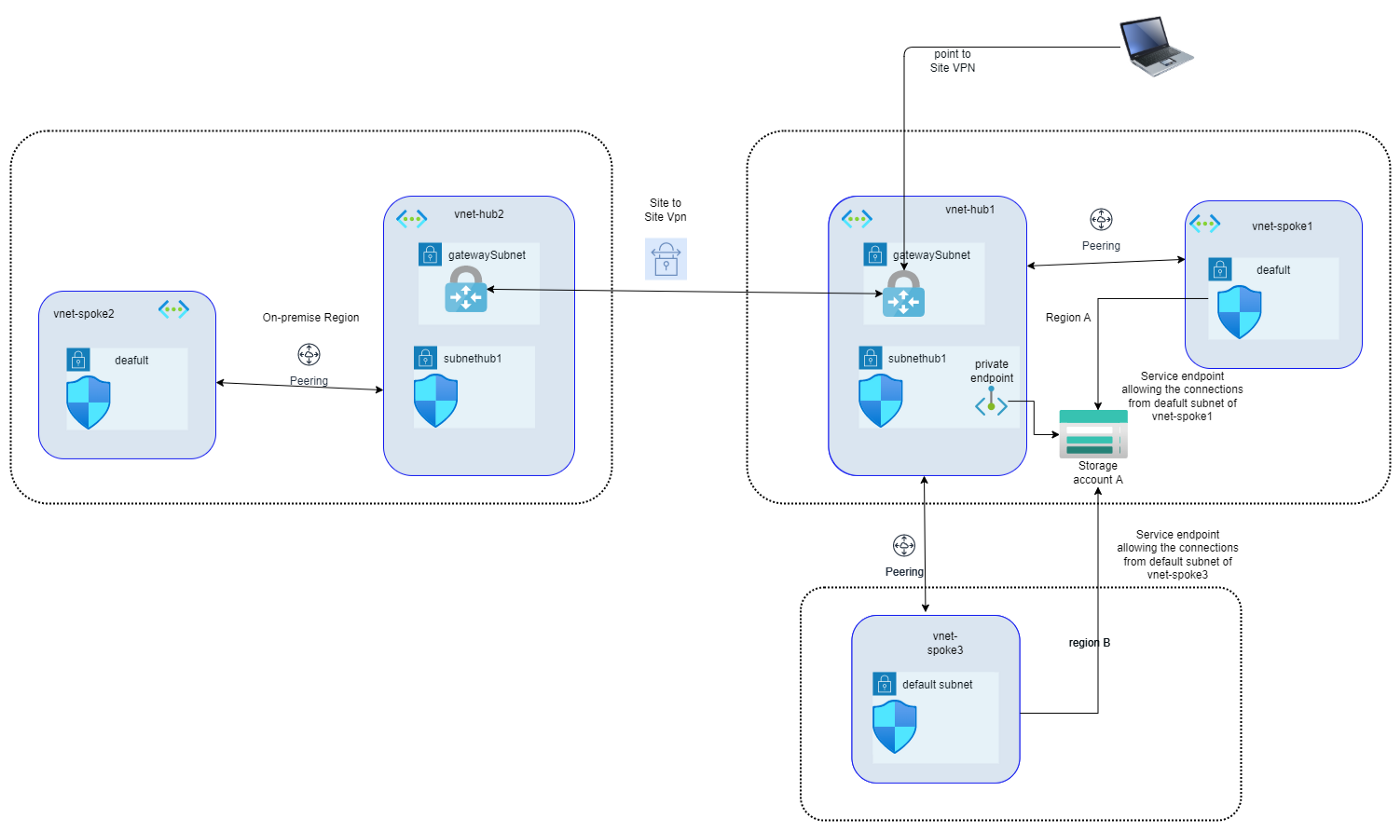
Securing access to Storage accounts at network layer
You can limit access to your storage account to requests originating from specified IP addresses, IP ranges, subnets in an Azure Virtual Network (VNet), or resource instances of some Azure services. And thats what is the focus of this article.
Azure offers two similar but distinct services to allow virtual network (VNet) resources to privately connect to other Azure services. Azure VNet Service Endpoints and Azure Private Endpoints (powered by Azure Private Link) both promote network security by allowing VNet traffic to communicate with service resources without going over the internet, but there are some differences.
Point to note is that these two secure ways to connect to Azure services are not limited to Azure Storage accounts. We will focus on how to use these services to secure access to Storage accounts in different scenarios.
Lets begin with brief introduction to each way of securing network access to Storage accounts.
Service Endpoints
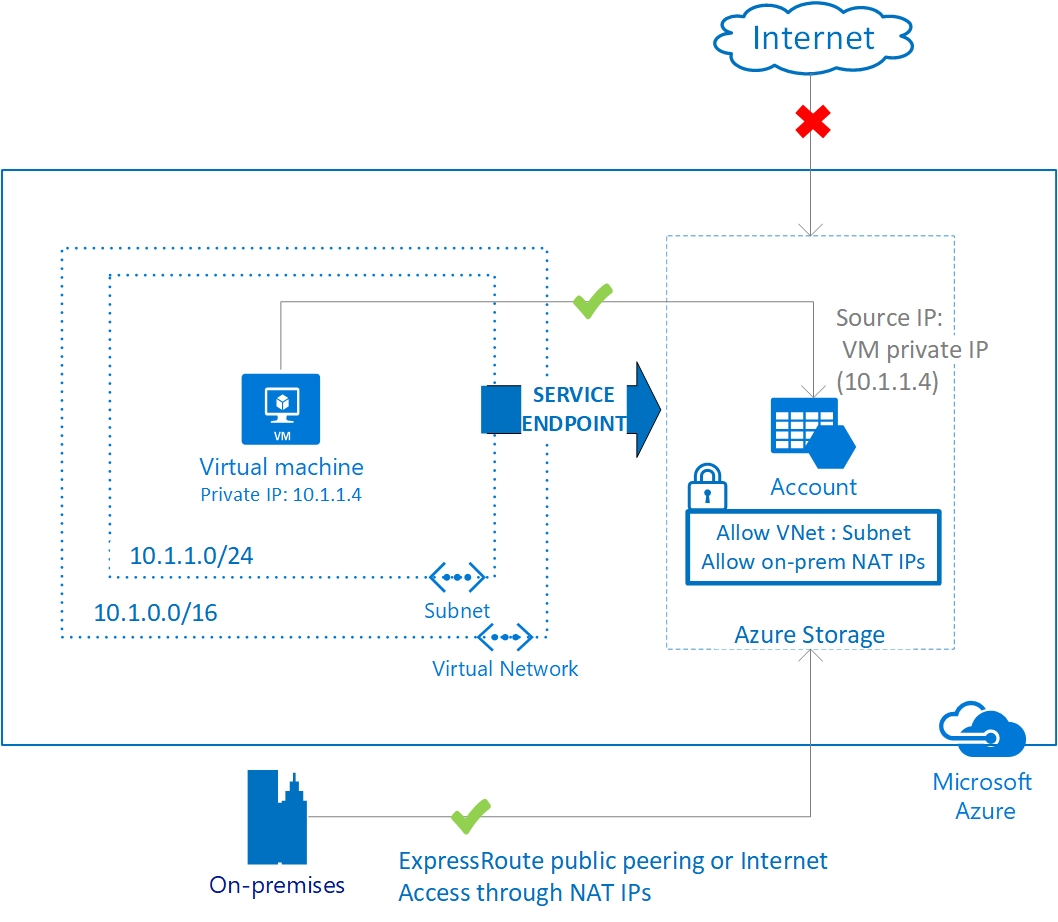
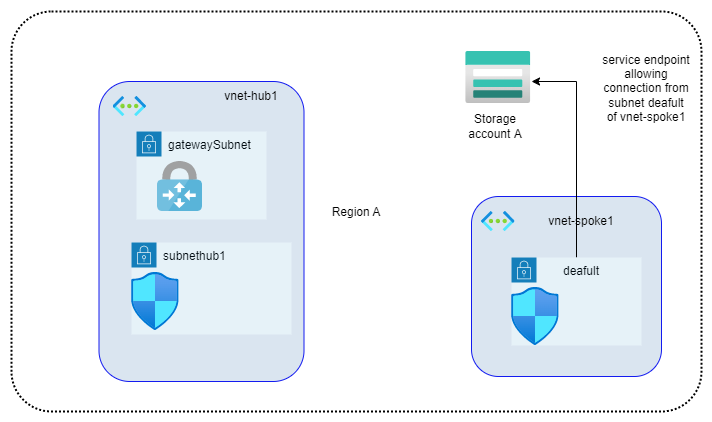
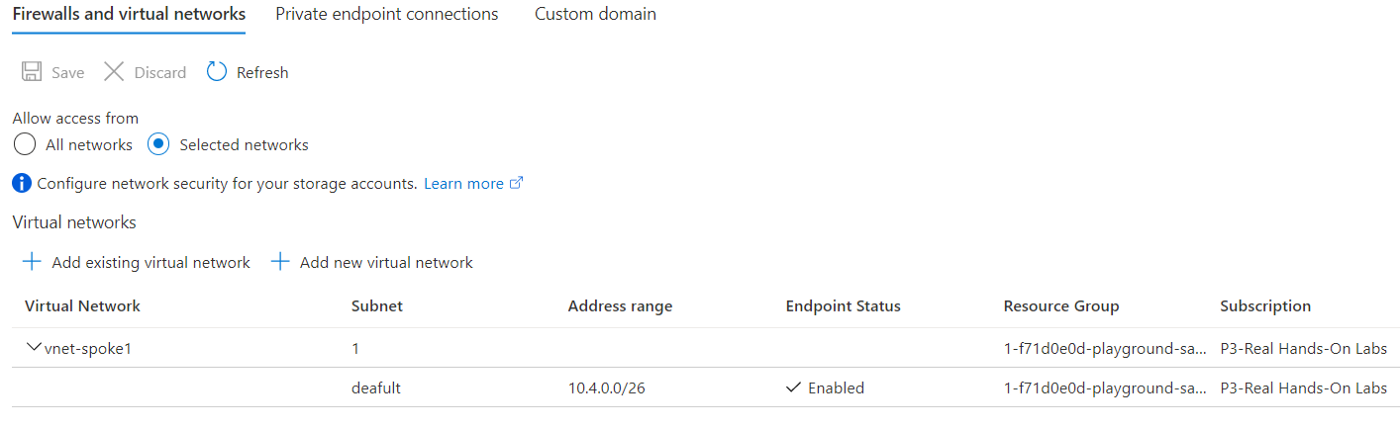
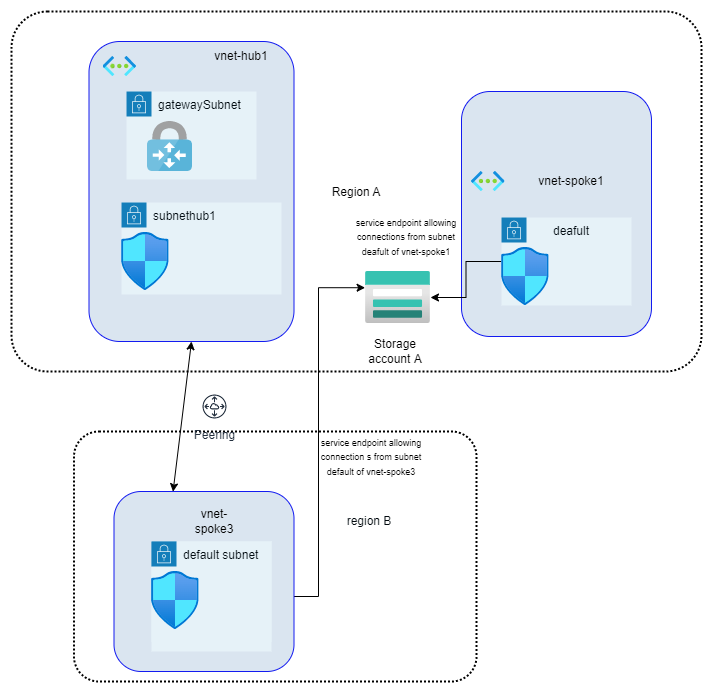
A service endpoint allows VNet resources to use private IP addresses to connect to an Azure service’s public endpoint, meaning traffic flows to the service resource over the Azure backbone network — instead of over the internet. In effect, you are extending the identity of the VNet to the service resource. You can then lock down the service resource so it only accepts traffic from the subnet associated with the service endpoint.