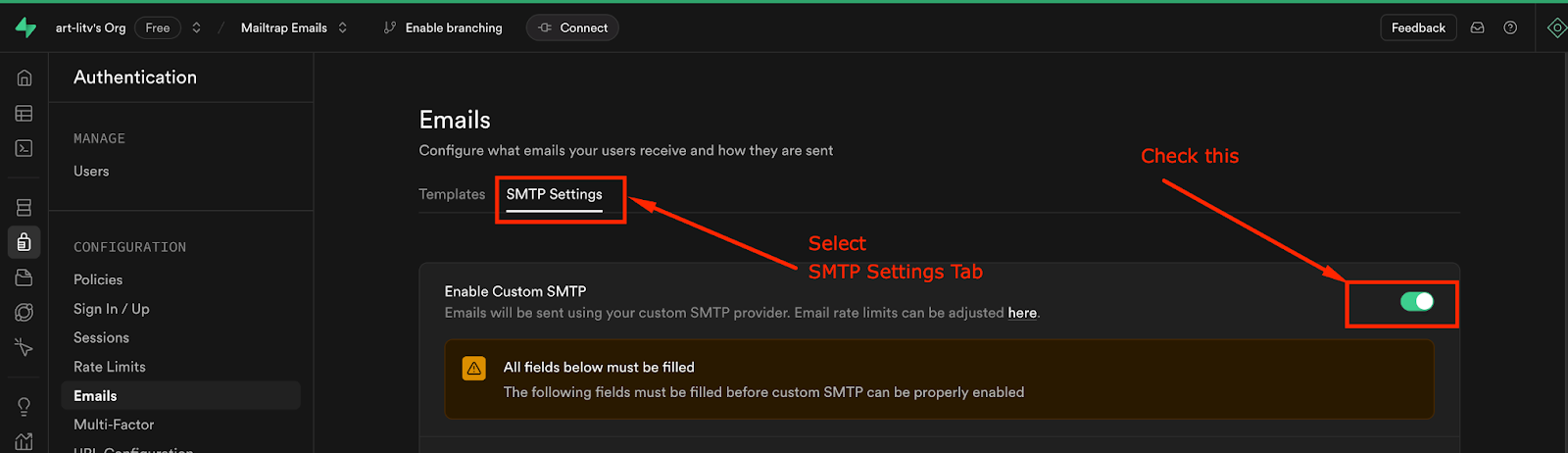
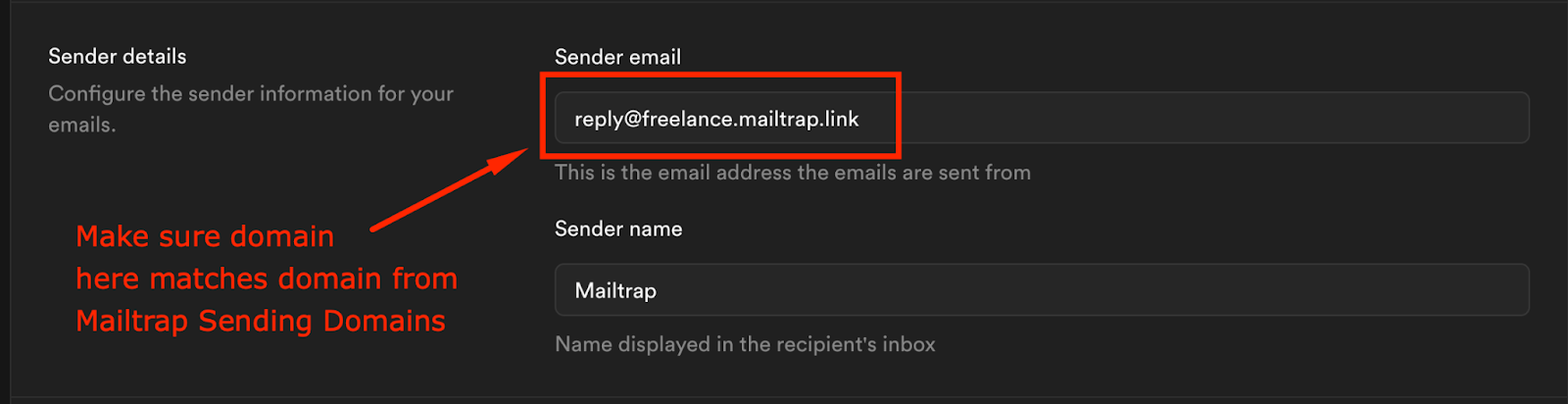
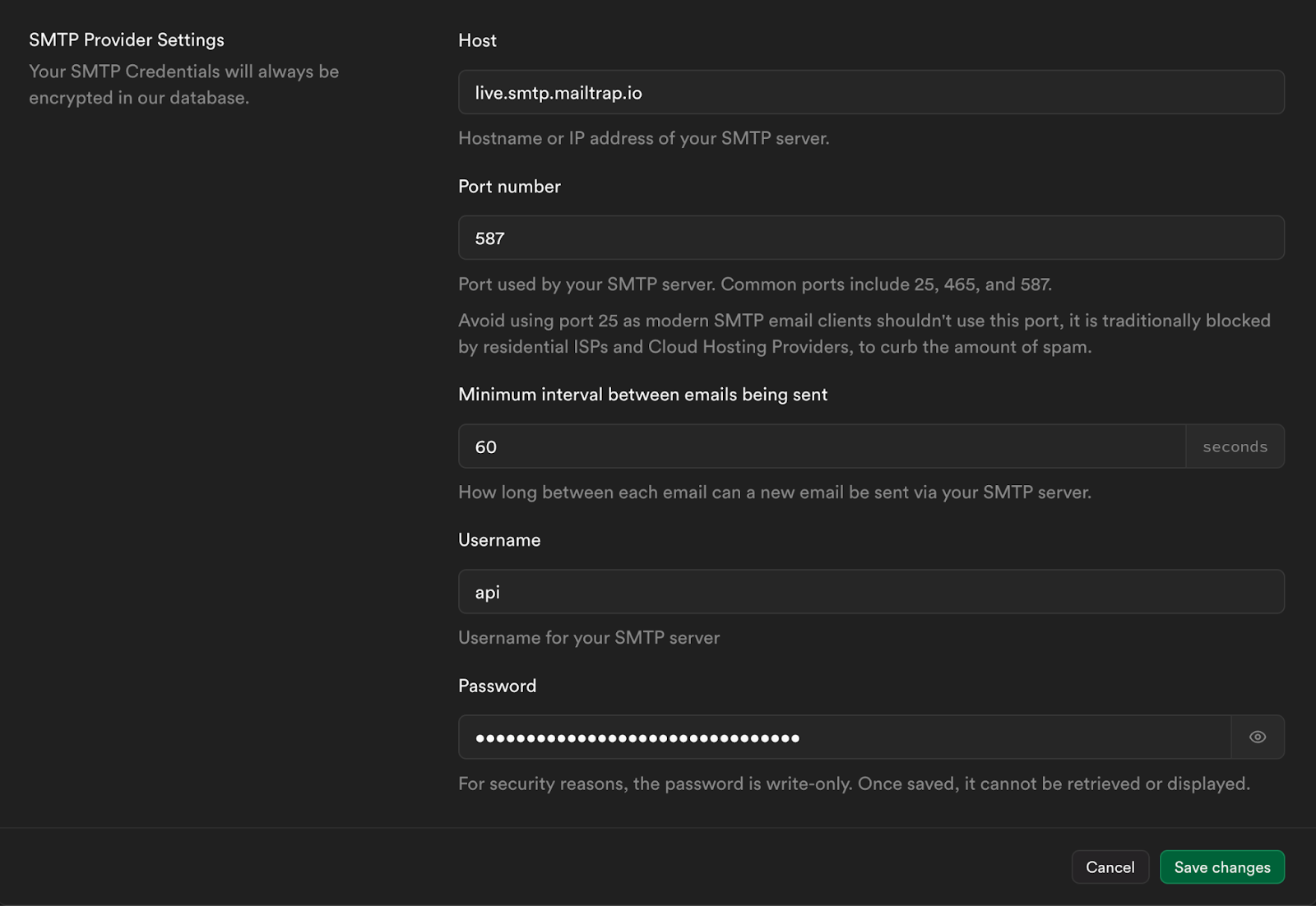
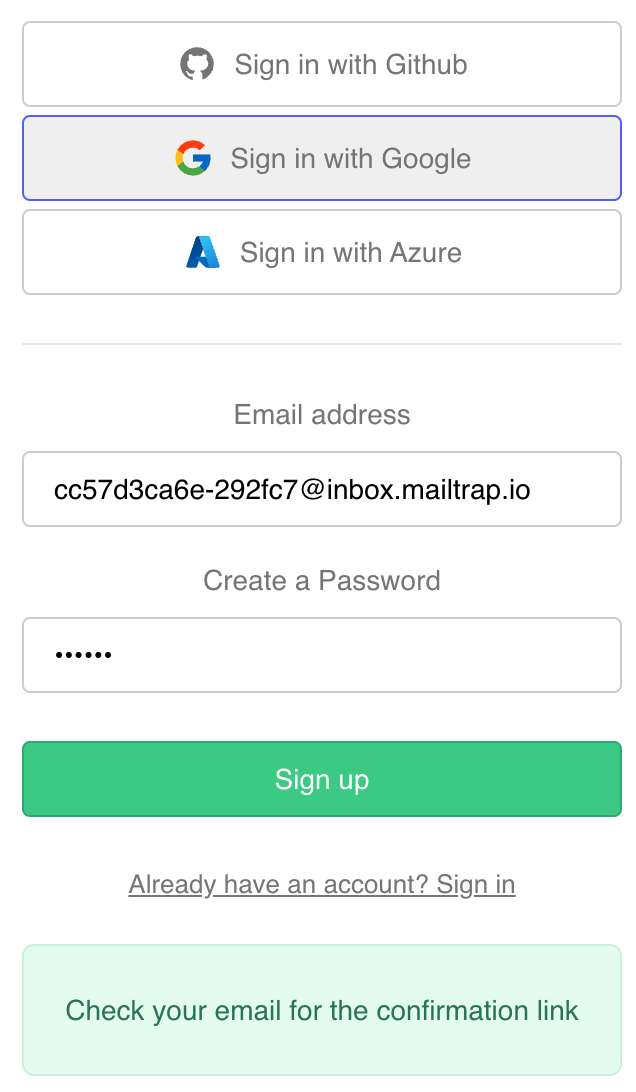
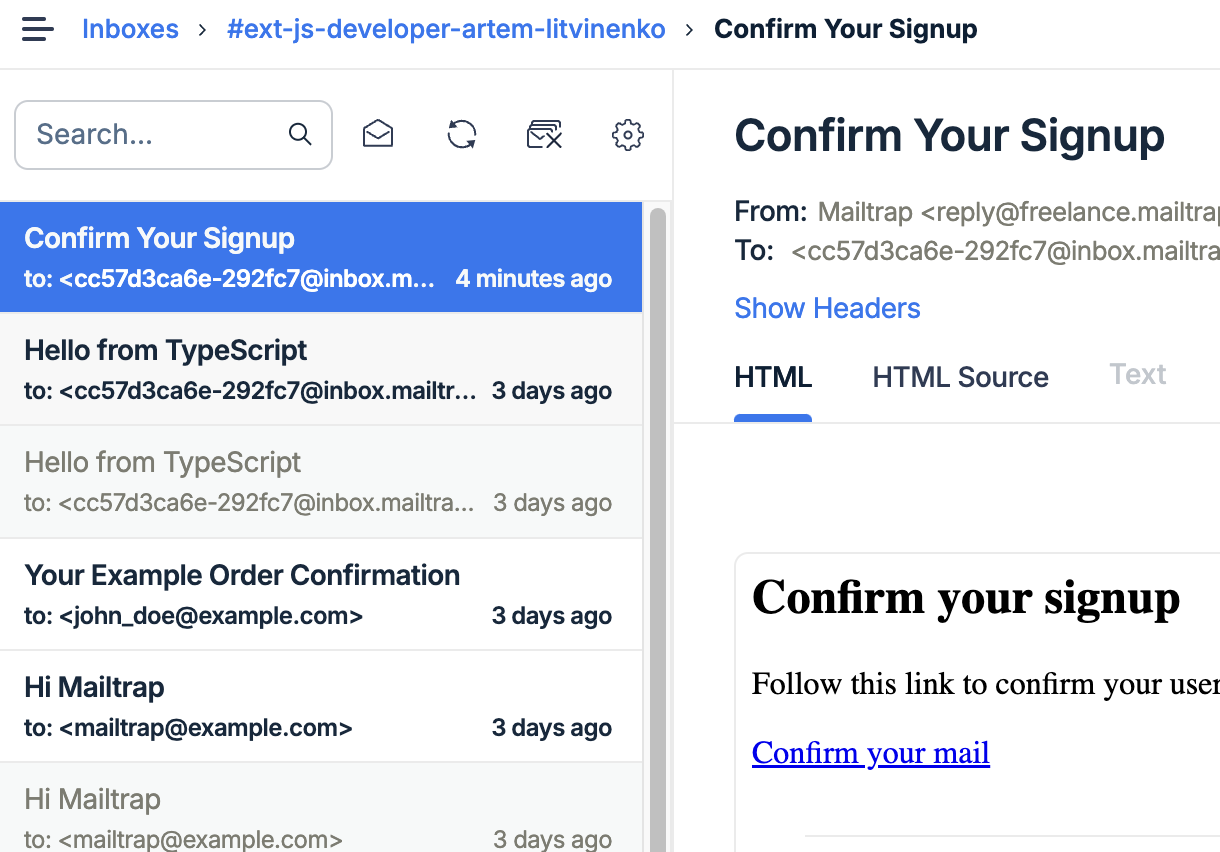
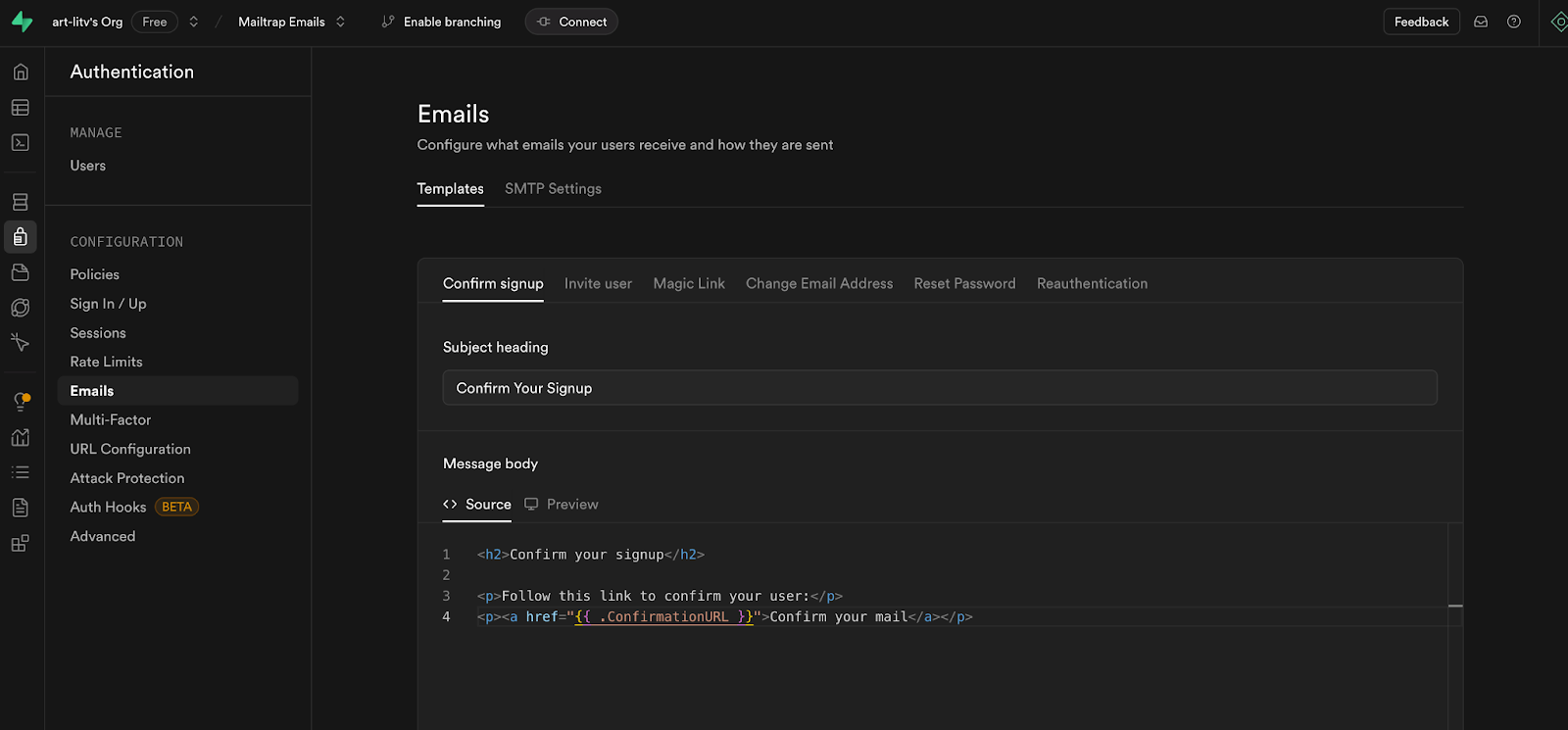
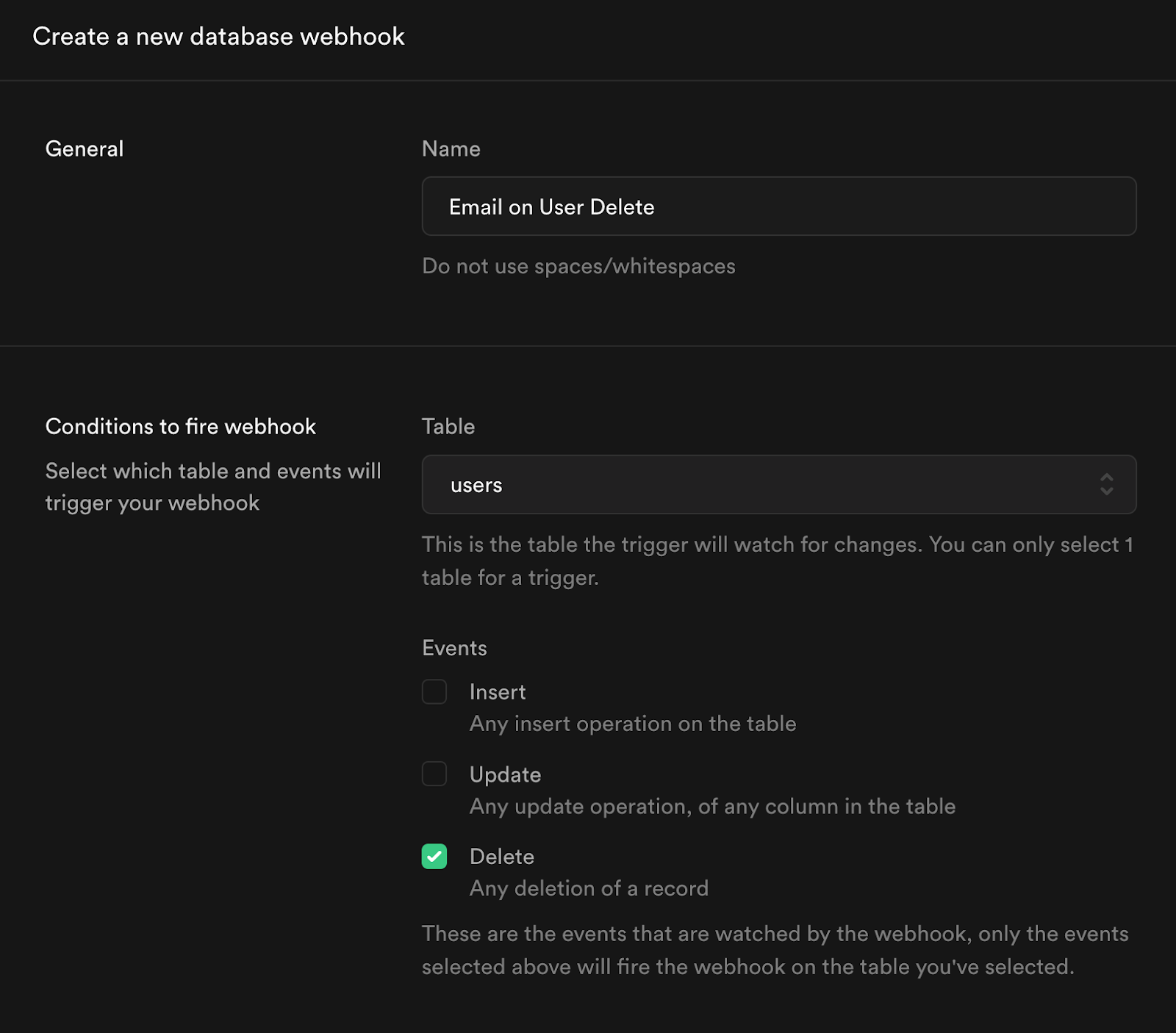
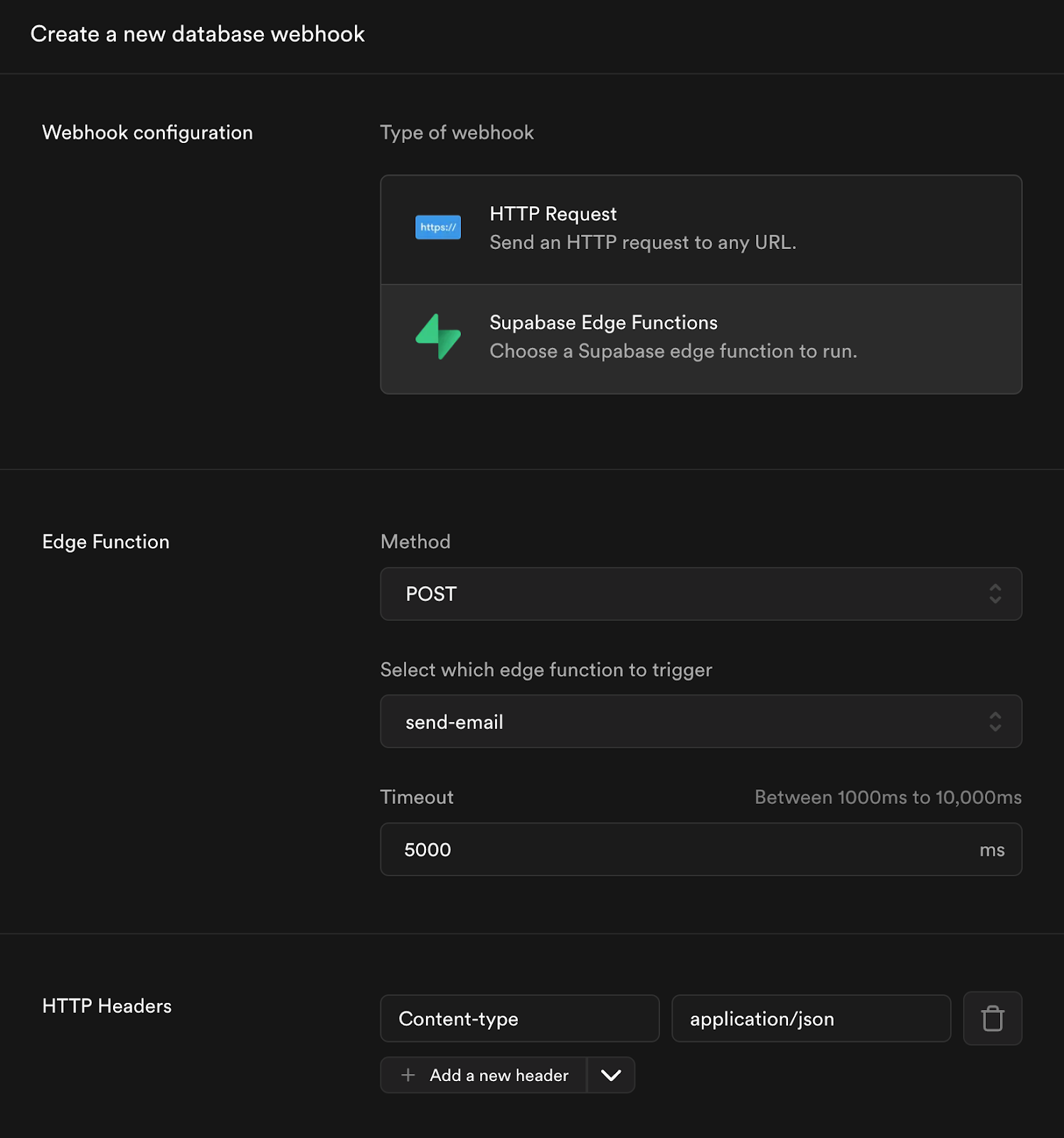
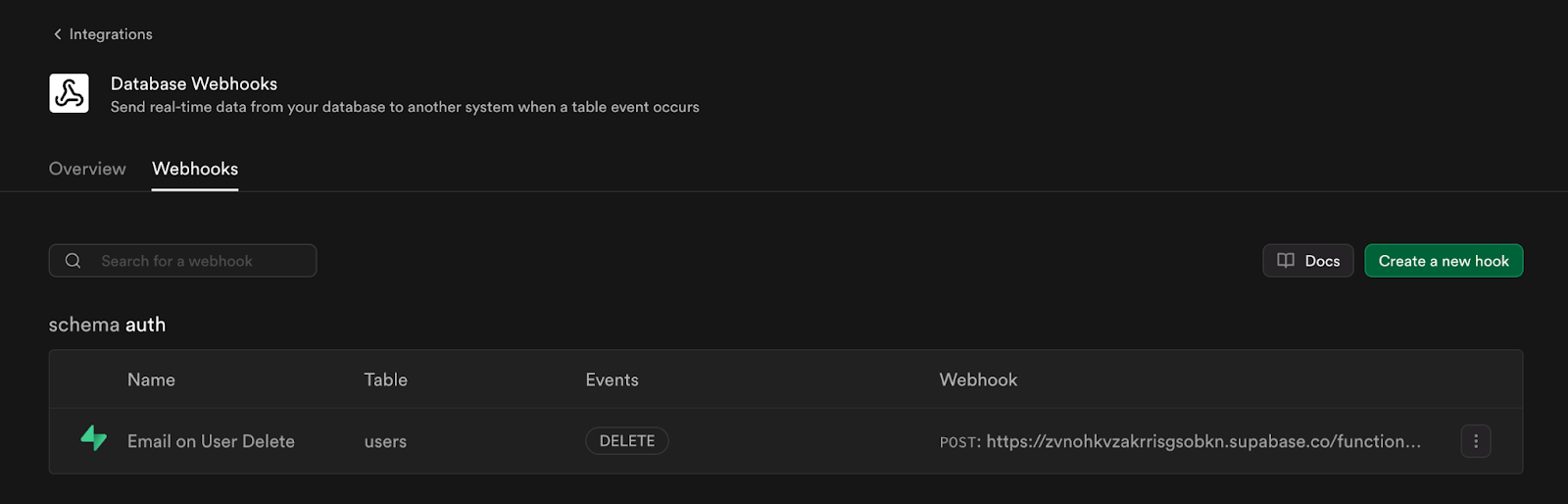
Additionally, you can edit and deploy your Email Templates locally.
Security considerations of using Supabase Auth
First, let’s talk about passwords. A strong password is more secure because it’s harder to guess or crack through brute-force attacks. Generally, longer passwords and those that use a wider variety of characters are more difficult to compromise.
Detailed control
Supabase Auth gives you detailed control over password strength for your project. For example, you can:
- Configure the minimum password length (e.g., avoid anything under 8 characters)
- Enforce the use of digits, lowercase and uppercase letters, and symbols for stronger passwords.
Integrations
Also, Supabase Auth integrates with the open-source HaveIBeenPwned.org Pwned Passwords API to block known compromised passwords.
Multi-Factor Authentication (MFA)
Beyond configuring secure password rules, encourage users to use a password manager to generate and store passwords, avoid reusing passwords across different platforms, steer clear of using personal information in passwords, and enable Multi-Factor Authentication (MFA) for added security. You can read more about password security in the official documentation. 🔐
Rate limits
Supabase Auth also provides rate limits to protect our app from abuse. For Sign up confirmation, we get a 60 seconds window before a new request is allowed. For other authentication methods, you can check the official documentation.
CAPTCHA
Also, Supabase offers protection from bots using CAPTCHA. Supabase supports hCaptcha and Turnstile providers; you can find more information about how to enable CAPTCHA for your project in the official documentation.
Row Level Security (RLS)
Supabase makes it easy and secure to access data directly from the browser (like in our React form example), provided that Row Level Security (RLS) is enabled. RLS must always be enabled on any tables within an exposed schema (typically the public schema by default). When you create tables using the Table Editor in the Supabase dashboard, RLS is enabled automatically. However, if you’re creating tables using raw SQL or the SQL Editor, you’ll need to manually enable it.
alter table <schema_name>.<table_name>
enable row level security;
RLS is a powerful and flexible Postgres feature that lets you define complex SQL rules tailored to your business logic. Combined with Supabase Auth, RLS ensures full end-to-end user-level data security, from the client to the database.
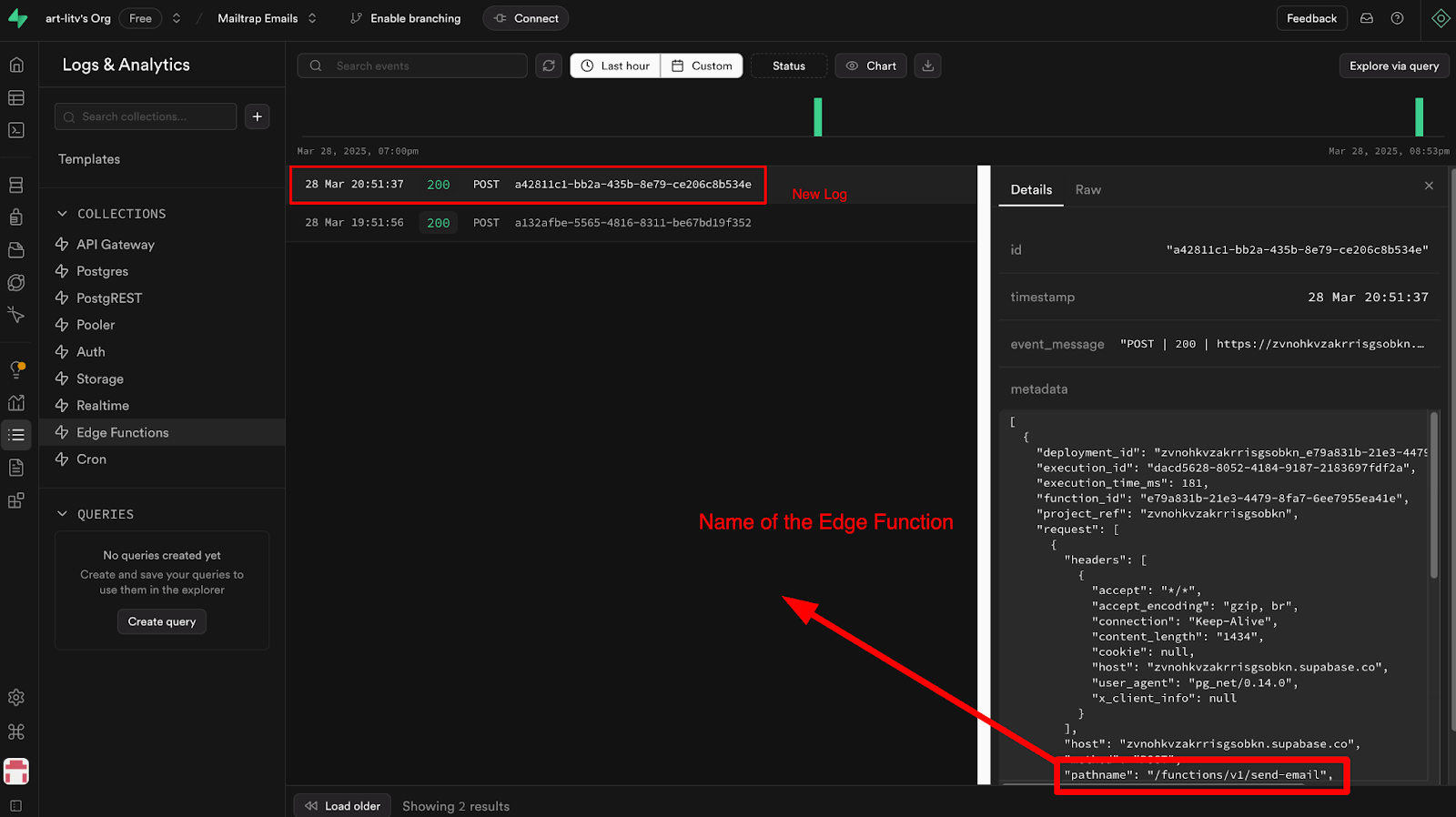
Configure Supabase Edge Functions and Database Webhooks
Edge Functions are server-side TypeScript functions deployed globally at the edge, close to your users, providing ultra-low latency. They’re ideal for handling webhooks or connecting your Supabase project with third-party services like Stripe.
Built with Deno, Edge Functions offer several advantages, like the ability to run them locally or on any Deno-compatible (even self-hosted) platform.
They can also be used to send emails efficiently, which I will cover further in the article.
Set up and deploy Supabase Edge Function
Now, let’s use the same project from the previous example to implement Supabase Edge Functions (or, alternatively, you could create a new project in a similar way).
First, make sure to install Supabase CLI to use it in the local environment.
npm:
npm install supabase --save-dev
yarn:
yarn add supabase --dev
Having set up Supabase CLI, let’s create our first Edge Function. You can do that by using the supabase functions new function-name command. This will create a new folder supabase/functions/send-email with a TypeScript starter file.
npm:
npx supabase functions new send-email
yarn:
yarn supabase functions new send-email
If you open the supabase/functions/send-email/index.ts file, your code should look like this:
// Follow this setup guide to integrate the Deno language server with your editor:
// https://deno.land/manual/getting_started/setup_your_environment
// This enables autocomplete, go to definition, etc.
// Setup type definitions for built-in Supabase Runtime APIs
import "jsr:@supabase/functions-js/edge-runtime.d.ts";
console.log("Hello from Functions!");
Deno.serve(async (req) => {
const { name } = await req.json();
const data = {
message: `Hello ${name}!`,
};
return new Response(JSON.stringify(data), {
headers: { "Content-Type": "application/json" },
});
});
/* To invoke locally:
1. Run `supabase start` (see: https://supabase.com/docs/reference/cli/supabase-start)
2. Make an HTTP request:
curl -i --location --request POST 'http://127.0.0.1:54321/functions/v1/send-email' \
--header 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJzdXBhYmFzZS1kZW1vIiwicm9sZSI6ImFub24iLCJleHAiOjE5ODM4MTI5OTZ9.CRXP1A7WOeoJeXxjNni43kdQwgnWNReilDMblYTn_I0' \
--header 'Content-Type: application/json' \
--data '{"name":"Functions"}'
*/
Code breakdown:
- The first
import statement is related to supabase internal configurations for Supabase Runtime APIs. - When the Edge Function file is executed, it will print “Hello from Functions!” in the console before initializing the Edge Function.
- We call Deno.serve to set up the actual Edge Function. In the example implementation, that allows us to send a greeting for the specified name when we call the Edge Function.
Before deploying your Edge Function to Supabase, make sure to link your project using your Project ID, which is a part of your Public URL (https://<project-id>.supabase.co). Before you link, you can get a list of your Project IDs by running the projects list command.
npm:
npx supabase projects list
npx supabase link --project-ref <project-id>
yarn:
yarn supabase projects list
yarn supabase link --project-ref <project-id>
Important: If you get asked to enter your database password, you can skip by pressing enter.
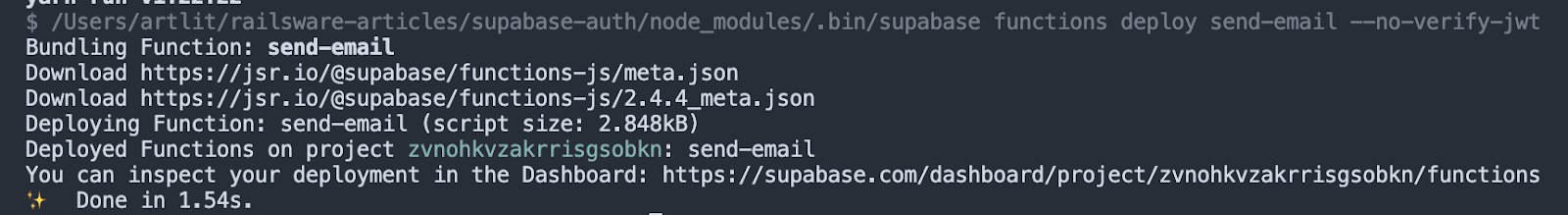
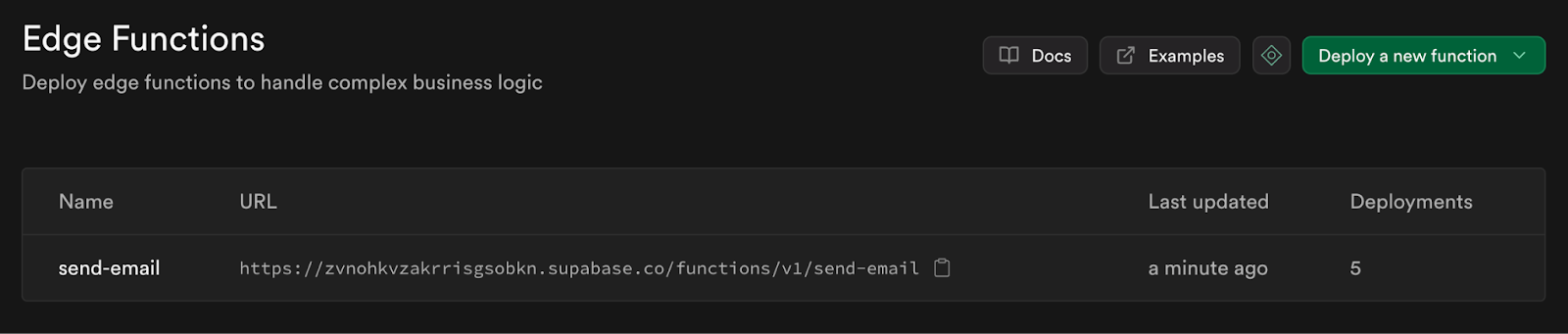
Now, let’s deploy the Edge Function to Supabase so that we can interact with it. By default, Edge Functions require a valid JWT in the authorization header. Since we want to use Edge Functions without Authorization checks, let’s pass --no-verify-jwt flag when deploying.
Before deploying, please make sure that you have installed Docker Desktop as I’ve mentioned in the beginning of the article, and then run one of the following commands:
npm:
npx supabase functions deploy send-email --no-verify-jwt
yarn:
yarn supabase functions deploy send-email --no-verify-jwt
You should see the following message in your code editor: