
Solution diagram
In this post, I will show you to comply with the auditing requirement by configuring a notification rule to the AWS CodeCommit repository as they’re created.
Attach a notification rule to the AWS CodeCommit repository as they’re created.
If you’ve ever worked with git repositories with your fellow developers for the company or projects you’re working with, then you must have toppled many requirements to keep your projects in shape (branching strategies, change approvals, auditing, etc).
Auditing is the one I consider the most important because it keeps track of each specified action executed in your git repository (pull requests, approval rules override, commits, etc.).
Our tradition as developers is to mostly focus on our development instead of compliance issues. We might hate it, but sadly we must follow orders as the good soldiers they expect us to be.
Now besides the poem, I’ve just recited, in this post, I will show you to comply with the auditing requirement by configuring a notification rule to the AWS CodeCommit repository as they’re created.
Prerequisites
- IAM User used for this post must have permissions to AWS Lambda, AWS EventBridge, AWS CodeCommit, and Amazon SNS.
2. Create Amazon SNS Topic and Subscription. https://docs.aws.amazon.com/sns/latest/dg/sns-getting-started.html
3. Create AWS Lambda function (Python 3.9).
https://docs.aws.amazon.com/lambda/latest/dg/getting-started.html
AWS Lambda
We will be setting up the AWS Lambda function which assign the Amazon SNS Topic to every AWS CodeCommit repository when they’re created.
Go to AWS Lambda service:
Access the AWS Lambda function instance you will be using for this demo.
The following will display the required “Environment variables” the AWS Lambda function requires.
In this case, the Environment variable will be the Amazon SNS Topic ARN you will be using for AWS CodeCommit repository notifications.
Now you must access the Execution Role.
In the “Configuration” tab, click on “Permissions” and click the “Role Name”:
Once inside your Execution role.
On the “Permissions” tab click “Add permissions > Create inline policy”:
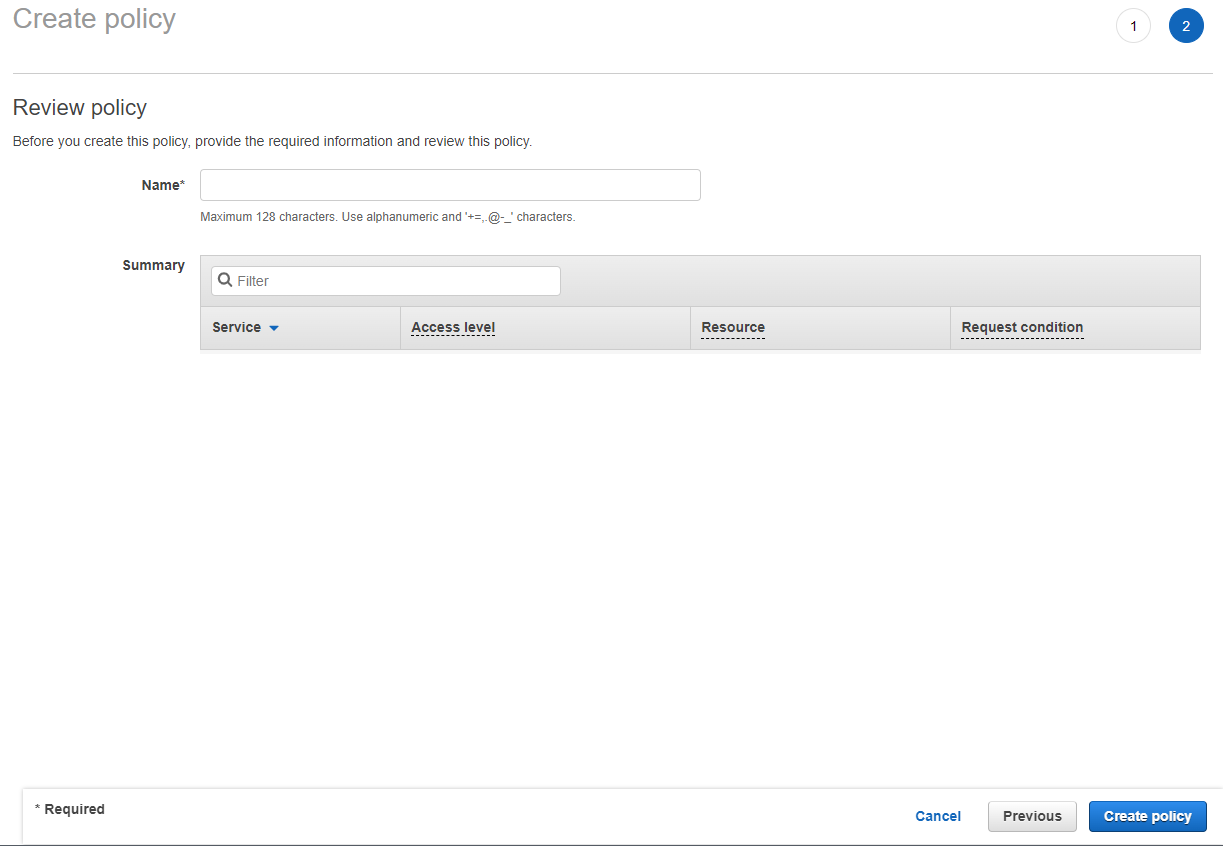
Click the “JSON” tab, copy-paste the following, then click “Review policy” (Remember to replace the placeholders):
Fill in the required fields and then click “Create policy”:
Now head back to the AWS Lambda function.
You will upload the following code:
https://github.com/jeanvelez2/assign_notification_to_codecommit_repository
AWS EventBridge
Now we will be creating the Amazon EventBridge Rule which invokes the AWS Lambda function from the previous only when an AWS CodeCommit repository is created.
Go to AWS EventBridge service:
On the left-hand menu you access “Rules”:
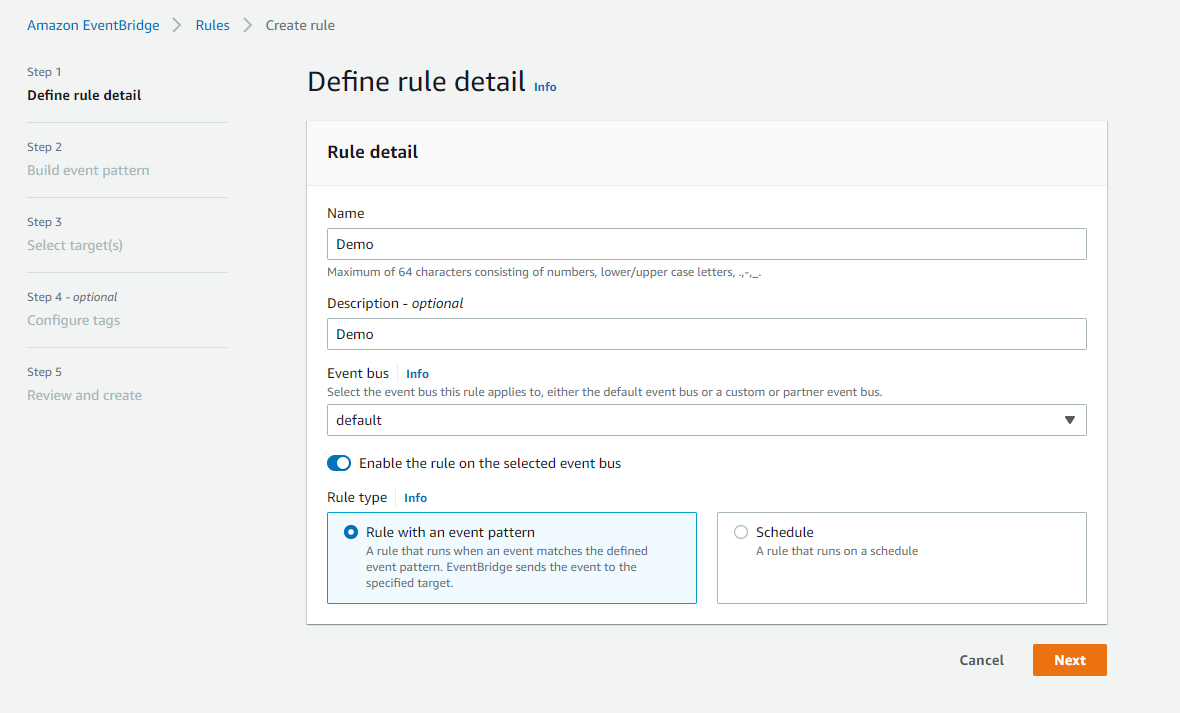
Then click the “Create rule” button:
Fill in the required fields, then click Next:
Select “AWS events or EventBridge partner events” as Event source:
Enter the following for the “Event pattern”, then click Next:
Now select the AWS Lambda function as target, the click Next:
Continue clicking Next until you arrive at the review page. If everything is in order, then click “Create rule” button:
AWS CodeCommit Repository
Everything is set up!
Now we must test it out (Fingers crossed).
Go to AWS CodeCommit service:
Click the “Create repository” button:
Enter the required fields, the click Create:
Wait around 5 seconds for AWS Lambda function to execute.
Access your AWS CodeCommit repository, then on the left-hand menu, click Settings:
Click the “Notifications” tab, there you should see the notification configuration:
Start pushing and pulling code using the AWS CodeCommit repository and you should see the Amazon SNS topic receiving the events as you decided to assign them (Email, SNS, HTTP, etc.).
Conclusion
You will have one less responsibility in regard to Auditing your repositories in AWS CodeCommit. This project was helpful for my AWS Accounts because many times I would forget to assign a notification rule to the AWS CodeCommit repository.
I did as a developer should do when that task got annoying: Automate it!!!
It has been fun writing this post, as always.
Any questions or comments, please let me know.
Hope you have a nice day, Thank you and Gracias!!!
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!
User Popularity
102
Influence
10k
Total Hits
6
Posts
























Only registered users can post comments. Please, login or signup.