Post-Quantum Cryptography in Kubernetes
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses... read more
Join us
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses... read more
Hey, sign up or sign in to add a reaction to my post.
GitGuardian's 2024 reportsounds the alarm:23 million secrets slipped through leaks in 2023. A whopping 70% hung around for months. Talk about a security nightmare! EnterHashiCorp VaultandAkeyless. These tools mastered the multi-cloud juggling act and automated secrets management. Result? A satisfyin.. read more

Hey, sign up or sign in to add a reaction to my post.
Zendeskhas tossed out the old playbook with itsFoundation Interface. Forget the guessing games of infrastructure provisioning; engineers now scribble their demands in YAML, and voilà—magic happens. Kubernetes operators step in, spinning these requests into Custom Resources. It’s self-service nirvana.. read more

Hey, sign up or sign in to add a reaction to my post.
ArgoCD MCP Serverteams up withAmazon Q CLIto shake up Kubernetes with natural language controls. Finally, GitOps that even the non-tech crowd can handle. Kiss those roadblocks goodbye. No more brain strain from Kubernetes. Now, plain language syncs apps, reveals resource trees, and checks health sta.. read more
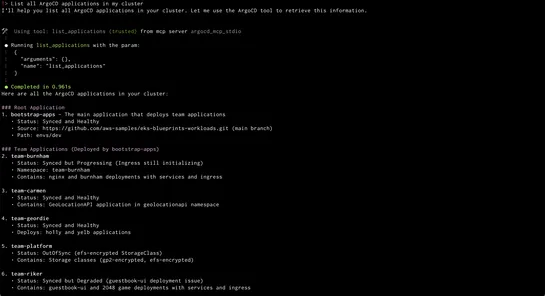
Hey, sign up or sign in to add a reaction to my post.
Amazon EKScranked up its gear—you can now spin up clusters with a staggering100,000 nodesat your beck and call. That’s a cozy home for either1.6 million AWS Trainium chipsor800,000 NVIDIA GPUs. Welcome to the playground for ultra-scale AI/ML. Performance soars skyward by ditching old etcd consensus .. read more
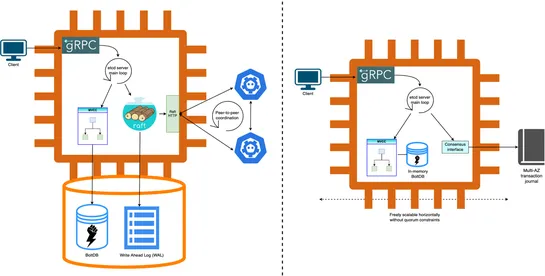
Hey, sign up or sign in to add a reaction to my post.
Edge systemseach have their eccentricities, needing solutions as unique as they are:Chick-fil-Aswears byKubernetesto herd its standard operations. TheAir Force, however, prizes nimbleness and ironclad security for deployments scattered across the globe. Smart edge management? It’s a mix ofInfrastruc.. read more
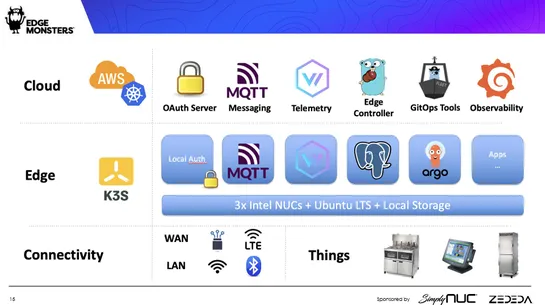
Hey, sign up or sign in to add a reaction to my post.
A cyberattack can strike at any time—causing operational disruption, financial loss, and reputational damage. Preparing for and effectively managing a cyber crisis is no longer optional—it's essential. At RELIANOID, we help businesses build robust cyber resilience through advanced solutions and expe..

Hey, sign up or sign in to add a reaction to my post.
Instrument NGINX with OpenTelemetry to capture traces, track latency, and connect upstream and downstream services in a single request flow.

Hey, sign up or sign in to add a reaction to my post.
In today's connected industrial world, the convergence of IT & OT brings efficiency—but also new risks. That’s why Zero-Trust Micro-Segmentation is no longer optional. 📌 It divides your network into isolated zones, applies strict access rules, and assumes no user or device is inherently trusted. ✅ K..
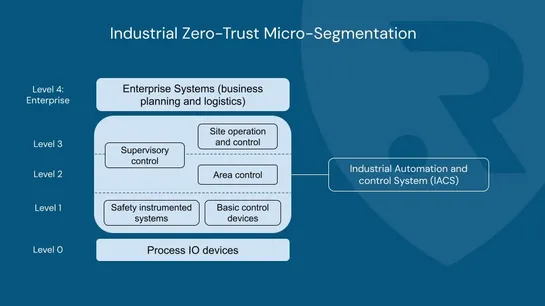
Hey, sign up or sign in to add a reaction to my post.
This organization doesn't have a detailed description yet. If you are the administrator of this organization, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
