Cloud Workstations managed development environment is now GA
Cloud Workstations, now GA, enables faster developer onboarding and increased productivity with an enhanced security posture... read more
Join us
Cloud Workstations, now GA, enables faster developer onboarding and increased productivity with an enhanced security posture... read more
Hey, sign up or sign in to add a reaction to my post.
To launch the collaboration, XContent is offering a complimentary Orca Security Score assessment, where companies can evaluate their cloud security posture and identify areas of vulnerability... read more

Hey, sign up or sign in to add a reaction to my post.
Azure IPVLAN for Docker containers can be confusing. Simply put, the host forwards and receives specific destination IP packets to the container. The IPVLAN works best when a container is completely separate from the host's IP address space. An alternative approach to using static routes is to use s.. read more
Hey, sign up or sign in to add a reaction to my post.
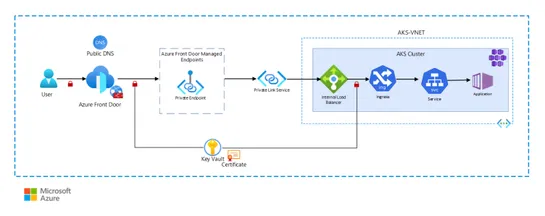
A blog post on securing AKS cluster with Azure Front Door and Private Link Service, discusses using different options to increase cluster security. It covers secure ingress setup using private link service, SSL termination with NGINX ingress controller, and the ability to store Kubernetes secrets in.. read more
Hey, sign up or sign in to add a reaction to my post.
There are three types of cloud encryption: data-at-rest, data-in-transit, and data-in-use. Encryption algorithms include symmetric and asymmetric encryption. Cloud encryption provides security, compliance, integrity, and risk reduction benefits, but challenges include time, expense, data loss, and k.. read more

Hey, sign up or sign in to add a reaction to my post.
Article on cloud native security principles and best practices to protect cloud environments using a combination of tools and technology. Includes key principles like devsecop, microservice architecture, automation, immutable infrastructure and zero trust security, as well as common challenges faced.. read more

Hey, sign up or sign in to add a reaction to my post.
This post walks through a timeline of how cloud security has grown over recent years to combat new and upcoming risks associated with its use. Following this timeline, security leaders can implement the latest in cloud security based on their own unique business requirements... read more

Hey, sign up or sign in to add a reaction to my post.
How feasible is high-reliability perfection and does it actually make a difference? In his latest blog for SHP, Dom Cooper unpacks the theory’s implementation and impact... read more

Hey, sign up or sign in to add a reaction to my post.
What does it mean to build a successful networking team? Is it hiring a team of CCIEs? Is it making sure candidates know public cloud inside and out? Or maybe it’s making sure candidates have only the most sophisticated project experience on their resume. In this post, the author discusses what a su.. read more

Hey, sign up or sign in to add a reaction to my post.
Trip.com plans to sell non-fungible tokens (NFTs) of its Singapore-based brand, Trekki, later this year... read more

Hey, sign up or sign in to add a reaction to my post.
This organization doesn't have a detailed description yet. If you are the administrator of this organization, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
