Send email from Linux: a guide
Basic steps to successfully build your Linux emails
Join us
Basic steps to successfully build your Linux emails

Hey, sign up or sign in to add a reaction to my post.
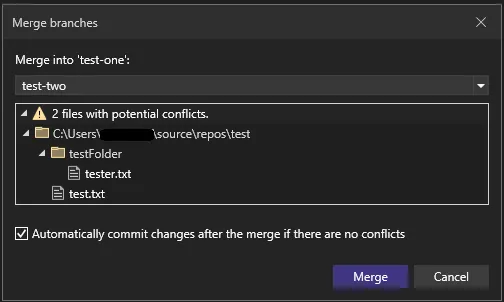
Microsoft has released Visual Studio version 17.6 Preview 2 with several Git improvements: - Improved Search for Related GitHub Issues and Azure DevOps Work Items: Find all your related issues and work items from your commits with better search results. - Merge Enhancements: Know when to expect merg.. read more
Hey, sign up or sign in to add a reaction to my post.
SynapseML v0.11, a distributed open-source machine learning library, has been released. - It includes new features such as OpenAI language models and embeddings, simple deep learning,LightGBM v2, ONNX Model Hub, and causal learning. - OpenAI language models enable the creation of complex LLM prompts.. read more

Hey, sign up or sign in to add a reaction to my post.
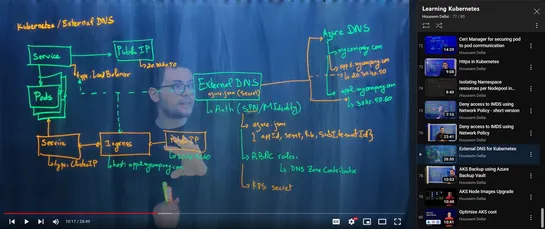
The tutorial explains how to use External DNS to manage custom domain names in Azure DNS using AKS. - External DNS is a Kubernetes controller that creates DNS records in Azure DNS automatically when new Ingresses or Services with specific annotations are created. - It is available as an open-source .. read more
Hey, sign up or sign in to add a reaction to my post.
This article explains how to deploy a secure file transfer protocol (SFTP) service on Microsoft Azure Container Apps, which is a more secure and cost-effective alternative to traditional FTP services. The article discusses the limitations of using Azure Container Instances (ACI) and introduces the .. read more
Hey, sign up or sign in to add a reaction to my post.
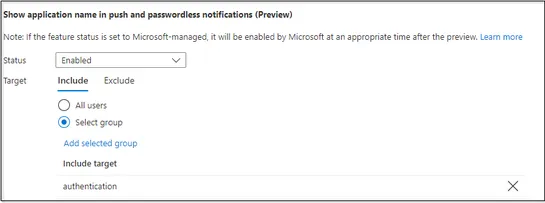
Multi-factor authentication (MFA) is essential to protect against password attacks, but it is vulnerable to various MFA attacks such as: - Man-in-the-middle attacks, - MFA Spamming, - SIM-Swapping attacks, - Pass-the-cookie attacks.MFA Fatigueattack is one such attack that tricks users into approvin.. read more
Hey, sign up or sign in to add a reaction to my post.
A zero-day flaw called GhostToken was discovered and disclosed by cybersecurity researchers that could have allowed threat actors to hide a malicious app in a victim's Google account. - The flaw affected all Google accounts, including enterprise-focused Workspace accounts. Google patched the issue a.. read more

Hey, sign up or sign in to add a reaction to my post.
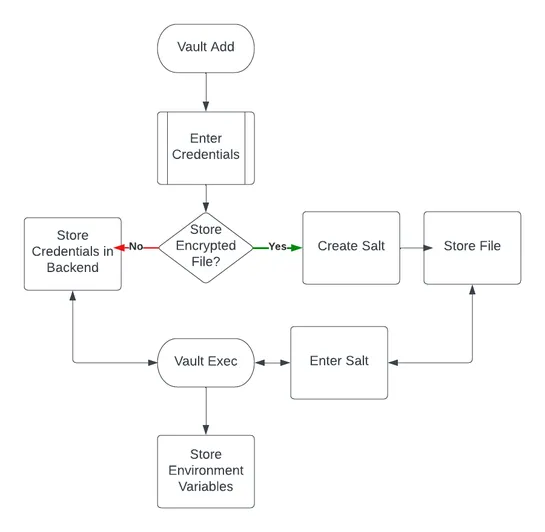
AWS Vaultis a tool that helps manage AWS credentials securely by avoiding the use of plaintext credentials and cumbersome token refreshing. - It simplifies the process of managing multiple AWS accounts and profiles, and supports roles and Multi-Factor Authentication (MFA) for extra security. - It of.. read more
Hey, sign up or sign in to add a reaction to my post.
AWShas released new policy optionsto secure instance credentials and reduce the risk of attackers stealing and abusing them. - There are multiple techniques for containing compromised instance credentials, but the easy ones are most likely to break things. - More creative options are available to lo.. read more
Hey, sign up or sign in to add a reaction to my post.
This organization doesn't have a detailed description yet. If you are the administrator of this organization, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
