A Comprehensive Guide to Building Event-Driven Architecture on Azure, AWS, and Google Cloud
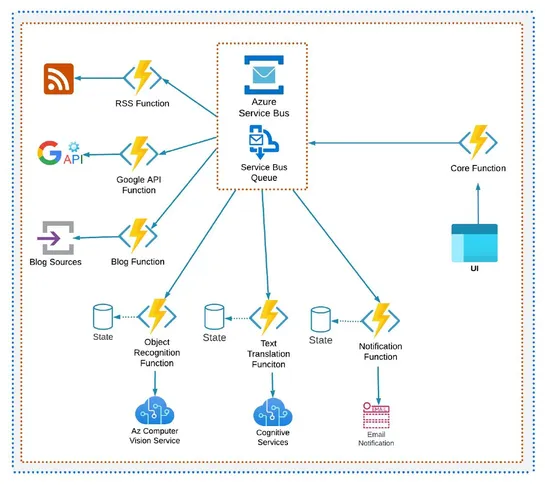
Cloud providers like Azure, AWS, and Google Cloud have various resources and components that can be used to build event-driven architectures. Azure Event Grid and Google Cloud Eventarc are event-driven platforms that enable event-based communication and workflows between services and applications... read more