Smart Contract Security: A 2023 Survey
Smart Contract Security - A mini course on smart contract security, providing a list of issues and vulnerabilities that recur in Solidity smart contracts... read more
Join us
Smart Contract Security - A mini course on smart contract security, providing a list of issues and vulnerabilities that recur in Solidity smart contracts... read more
Hey, sign up or sign in to add a reaction to my post.
When most people think about web3 security, they think about smart contracts holding hundreds of millions of dollars of funds. But web3 security is much broader than that. This article explores the intersection between web2 and web3 in NFT marketplaces, and how you can find Cross-Site Scripting (XSS.. read more
Hey, sign up or sign in to add a reaction to my post.
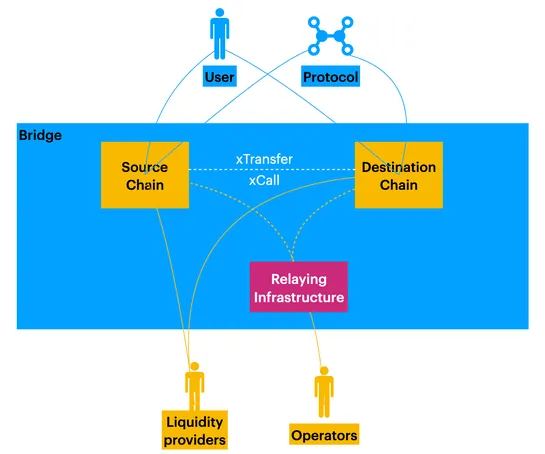
Bridge exploits account for ~50% of all DeFi exploits since September 2020, totaling ~$2.5B in lost assets, according to the Token Terminal. Ever since chain interoperability has become a hot topic, Web3 bridges became a popular target for hackers. This is due to the nature of Web3 projects (open-so.. read more
Hey, sign up or sign in to add a reaction to my post.
An updated version of the commodity malware called Legion comes with expanded features to compromise SSH servers and Amazon Web Services (AWS) credentials associated with DynamoDB and CloudWatch... read more

Hey, sign up or sign in to add a reaction to my post.
Legion hacker, a commercial malware tool, has widened its scope in targeting cloud services and can now compromise SSH servers and steal additional AWS-specific credentials, according to security firm Cado Security. The tool's main goal is to harvest credentials and store configuration files. Atta.. read more

Hey, sign up or sign in to add a reaction to my post.
Beginning August 2023, Azure storage will begin phased roll out of changes that disables anonymous access and cross tenant replication for all new storage accounts by default, to align with best practices for security and reduce the risk of data exfiltration. Existing storage accounts will not be im.. read more

Hey, sign up or sign in to add a reaction to my post.
GitLab 16 includes more than 55 improvements and new features. Learn about the most notable new technologies in this GitLab platform... read more

Hey, sign up or sign in to add a reaction to my post.
AWS IAM is a magnificent creation. But developers and security professionals continue to face some recurring challenges while dealing with the service. To that end, the author compiled a wishlist of 5 AWS IAM feature requests: - IAM Authorization Debugging - Mapping of API Calls, IAM Permissions, an.. read more

Hey, sign up or sign in to add a reaction to my post.
The article compares Privileged Access Management (PAM) vs Privileged User Management (PUM) approaches to managing privileged access. PAM manages onetime permission while PUM manages permanent access to critical assets and built-in admin accounts. Combining both approaches can enhance protection of .. read more

Hey, sign up or sign in to add a reaction to my post.
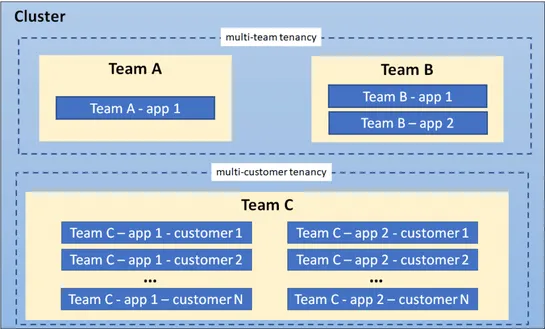
This post explores ways to optimize a Kubernetes cluster, including different cluster node tenancy configurations and sandbox solutions. It underlines the importance of considering critical factors such as resource utilization, network topology, and storage requirements, and provides good practices .. read more
Hey, sign up or sign in to add a reaction to my post.
This organization doesn't have a detailed description yet. If you are the administrator of this organization, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
