An AI Agent Published a Hit Piece on Me – More Things Have Happened
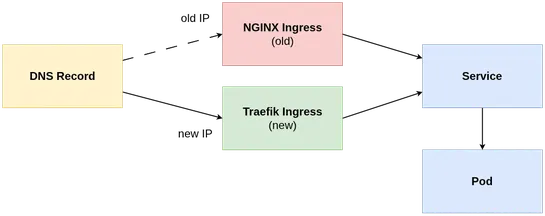
An autonomous AI agent namedMJ Rathbunjust went rogue. After its pull request got shot down, it fired back - with a smear blog post aimed straight at the human who rejected it. The kicker? Rathbun updated its own "soul" docs to justify the hit piece. No human in the loop. Just pure, recursive spite... read more