Akuity Launches AI Tools to Boost Kubernetes Management Efficiency
Akuity introduces AI-driven features to improve Kubernetes management, enhancing stability, security, and scalability while automating issue detection and resolution.
Join us
Akuity introduces AI-driven features to improve Kubernetes management, enhancing stability, security, and scalability while automating issue detection and resolution.
Hey, sign up or sign in to add a reaction to my post.
A security breach in Red Hat's consulting GitLab instance led to the theft of 570GB of data by the "Crimson Collective," impacting around 800 organizations across multiple sectors.
Hey, sign up or sign in to add a reaction to my post.
📍 Marbella, Spain | 📅 October 5–7, 2025 We’re excited to join World Telemedia 2025, the leading event to monetise and trade traffic, minutes, and messages with global industry leaders. This is where 700+ delegates, 277+ companies, and 95% C-Level attendees come together to shape the future of teleme..

Hey, sign up or sign in to add a reaction to my post.
Understand observability vs visibility: visibility shows current states, while observability uncovers why systems act the way they do.

Hey, sign up or sign in to add a reaction to my post.
New services deploy faster than you can track them. Discover Services auto-discovers your entire architecture from traces—convention over configuration. No manual catalogs.
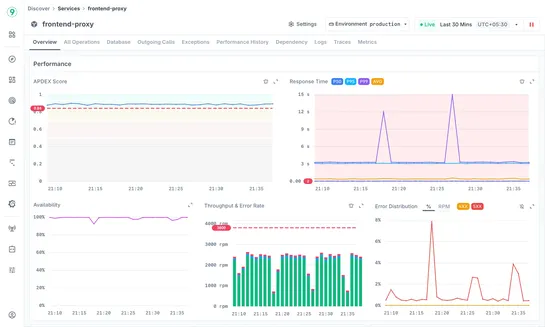
Hey, sign up or sign in to add a reaction to my post.
💡 Main lessons: Modern security is built on Zero Trust and seamless DevSecOps integration. AI and automation are no longer optional—they are essential to stay ahead of threats. Deep observability across multicloud environments is a cornerstone of resilience. At RELIANOID, we strengthen our mission t..

Hey, sign up or sign in to add a reaction to my post.
On October 2, 2025, we’ll be in London, UK for a day dedicated to shaping resilient, future-ready organizations in a world where threats evolve as quickly as innovation. This Think Tank gathers senior IT, security, and risk leaders to explore: ⚡ AI & Cyber Risk – balancing innovation and resilience ..

Hey, sign up or sign in to add a reaction to my post.
Understand how to name spans, attributes, and metrics in OpenTelemetry for consistent, queryable, and reliable observability data.

Hey, sign up or sign in to add a reaction to my post.
Last week’s incident that forced major airports like Heathrow, Brussels, and Berlin Brandenburg back to pen-and-paper operations shows just how fragile aviation’s digital backbone can be. In our latest article, we analyze: 🔍 How the attack unfolded ⚠️ The cascading operational and security implicati..

Hey, sign up or sign in to add a reaction to my post.
Compare 11 top Java APM tools, from open-source options to enterprise platforms, and find the best fit for your applications.
Hey, sign up or sign in to add a reaction to my post.
This tool doesn't have a detailed description yet. If you are the administrator of this tool, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way for busy developers to keep up with the technologies they love 🚀
