System Design Made Easy: A Step-by-Step Guide for 2024
System Design Made Easy: A Step-by-Step Guide for 2024
Join us
System Design Made Easy: A Step-by-Step Guide for 2024
Hey, sign up or sign in to add a reaction to my post.
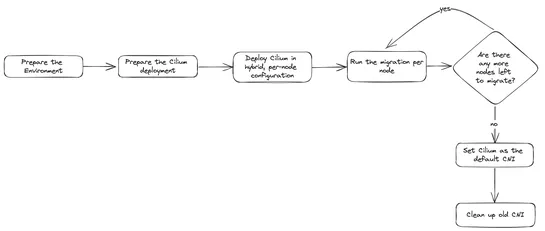
Kubernetes clusters can run on different CNIs, and switching between them is complex. Migrating from Calico to Cilium, for example, involves deploying Cilium alongside Calico, testing connectivity, and gradually switching workloads to use Cilium. This method ensures minimal downtime and service disr.. read more
Hey, sign up or sign in to add a reaction to my post.
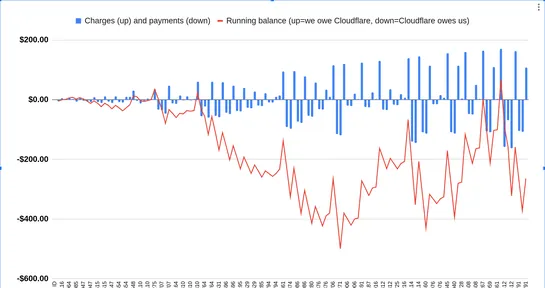
The author investigated unexpectedly high charges from Cloudflare Images forEphemeraSearch, involving complex billing cycles and credits. They discovered that changing image storage capacity triggers immediate charges, with credits applied the following month, leading to temporary overbilling. Despi.. read more
Hey, sign up or sign in to add a reaction to my post.
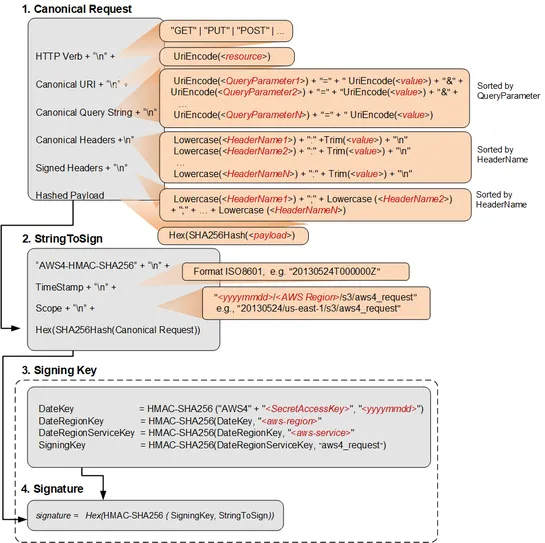
Researchers have successfullyreverse-engineeredAWS Session Tokens, revealing their internal structure and cryptographic methods. They created open-source tools for analyzing and modifying these tokens and tested their resilience against forging attacks, finding them robust. Additionally, they identi.. read more
Hey, sign up or sign in to add a reaction to my post.
Kubernetes 1.31 introduces several major enhancements, including AppArmor support for defining security profiles at the container or pod level. Another notable change is the removal of all in-tree integrations with cloud providers, pushing Kubernetes towards vendor neutrality. Additionally, improvem.. read more

Hey, sign up or sign in to add a reaction to my post.
CVE-2024-5535 is a bug in OpenSSL that has been present since 2011, allowing the leakage of up to 255 bytes of the client's heap data to the server when theSSL_select_next_protofunction is called with a client buffer that is not a valid list of protocols. This bug affects OpenSSL, BoringSSL, Node.js.. read more
Hey, sign up or sign in to add a reaction to my post.
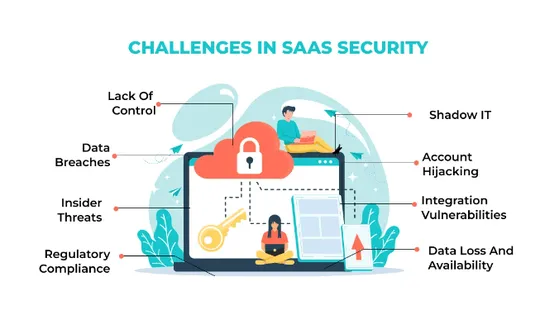
In February 2023, LastPass experienced a security breach involving a targeted attack on a DevOps engineer’s access to the corporate vault. This incident highlights the critical importance of robust access controls and security practices in SaaS environments, where customers must secure applications,.. read more
Hey, sign up or sign in to add a reaction to my post.
Cilium and Tetragon are two powerful tools combined to defend the Damn Vulnerable Web Application (DVWA) against attacks by harnessing the power of eBPF technology in the Kubernetes universe. By utilizing Cilium for process, file, HTTP, and network-based defenses alongside Tetragon for security obse.. read more
Hey, sign up or sign in to add a reaction to my post.
Google Cloud offers Y Combinator startups a dedicated subsidized cluster of Nvidia GPUs and Google TPUs, plus $350,000 in cloud credits over two years. This includes $12,000 in Enhanced Support credits, a free year of Google Workspace Business Plus, and access to Google's internal AI experts... read more

Hey, sign up or sign in to add a reaction to my post.
The author's research led to a new finding, prompting AWS to make significant changes to VPC Endpoint behavior by preventing information discovery using VPC endpoints. The change includes restrictions on the usage of wildcard characters in VPC Endpoint policies, specifically in relation to global co.. read more
Hey, sign up or sign in to add a reaction to my post.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
