New Linux Flaws Allow Password Hash Theft via Core Dumps in Ubuntu, RHEL, Fedora
Wiz Researchpoked around in over150,000 cloud accountsand unearthed some jaw-dropping screw-ups in data exposure and pitiful access control... read more
Join us
Wiz Researchpoked around in over150,000 cloud accountsand unearthed some jaw-dropping screw-ups in data exposure and pitiful access control... read more
Hey, sign up or sign in to add a reaction to my post.
Security backlogs resemble a garage sale—clutter everywhere and sorted more by desperation than priority. Here’s whereLLMsswoop in for smart triage. Choose your weapon: "naive" for speed, "bubble" for depth, orElofor that sweet balance. This way, you can organize chaos with logic, anchoring decision.. read more

Hey, sign up or sign in to add a reaction to my post.
AWS KMShas this cool trick now: on-demand rotation for imported key material. Your key ID stays put, so your code won’t throw a tantrum. Who wants more manual updates anyway?.. read more
Hey, sign up or sign in to add a reaction to my post.
Catchpoint's IPM reports a jaw-dropping 51% of companies hemorrhaging over$1 million each monthfrom API disasters. It's about performance, not just uptime. Modern API tools need to zero in on user experience metrics. Ditch the tired up/down routine. Embrace chaos engineering, pair it with proactive .. read more
Hey, sign up or sign in to add a reaction to my post.
Kubernetes 1.33struts onto the scene with stablesidecar containers, topology-aware routing, and pod topology spread constraints. No beta testing anymore; it's fully unleashed onAWS EKS... read more

Hey, sign up or sign in to add a reaction to my post.
The Isovalent Platform 1.17 release brings major upgrades to Kubernetes networking, including a new standalone Egress Gateway, dynamic BGP features, enhanced multi-tenant security policies, and smoother Calico-to-Cilium migrations. This version also introduces easier observability with integrated Ti.. read more
Hey, sign up or sign in to add a reaction to my post.
Apache Pinot's Helm setup is a welcome mat for troublemakers.It throws the doors open to critical services without bothering to ask, "Who goes there?" It's the kind of oversight attackers savor.Meshery and Selenium join the party too.Their default settings flirt with disaster, leaving the gates ajar.. read more
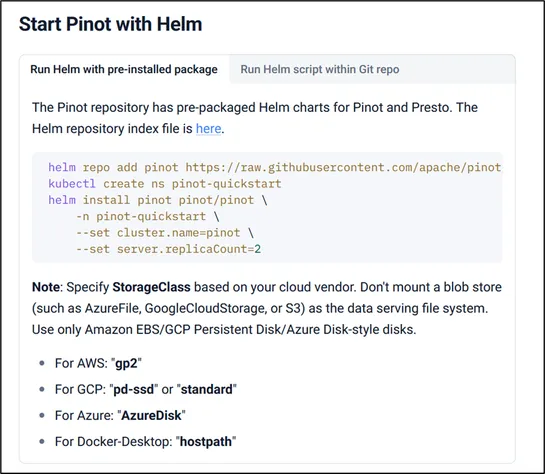
Hey, sign up or sign in to add a reaction to my post.
AI workloads thrive on cloud-native platforms like Kubernetes because they offer the scalability, portability, and speed needed for modern machine learning—but building and running this infrastructure is highly complex and distracts from core AI work. The post argues that unless your business is inf.. read more
Hey, sign up or sign in to add a reaction to my post.
Managed K8slike Amazon EKS or GKE? A ticket to smoother ops, but at the expense of control. Enterautoscaling, service meshes, andGitOps—they shift the deployment game dramatically. But don’t fall into the trap of thinking every app belongs on K8s. High-latency, tightly bound apps flounder there. Tos.. read more
Hey, sign up or sign in to add a reaction to my post.
AWS's Model Context Protocol (MCP) servers arm AI code assistantsto deftly wrangle AWS Lambda, ECS, and EKS. They launch apps at warp speed.MCP servers cram in AWS best practices and operational secrets,freeing you from infrastructure drudgery. You get to dive straight into crafting the heart of you.. read more

Hey, sign up or sign in to add a reaction to my post.
This tool doesn't have a detailed description yet. If you are the administrator of this tool, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
