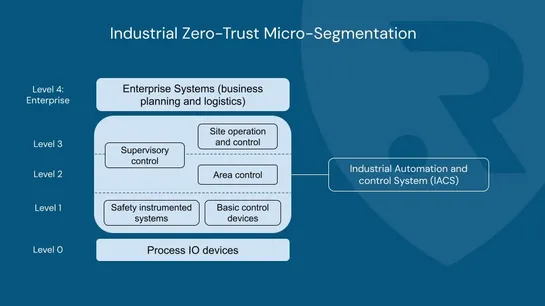
v1.34: Decoupled Taint Manager Is Now Stable
Kubernetes 1.34 graduates the taint eviction controller to GA. Now, the node lifecycle controller only applies taints, while a dedicated taint eviction controller manages pod eviction. First split in 1.29, now stable in 1.34... read more