Avoiding Zombie Cluster Members When Upgrading to etcd v3.6
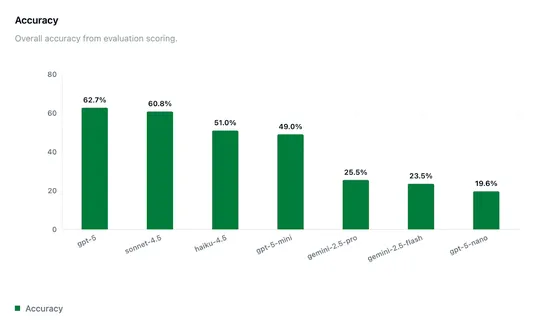
etcd v3.5.26 patches a nasty upgrade bug. It now syncsv3storefromv2storeto stop zombie nodes from corrupting clusters during the jump to v3.6. The core issue: Older versions let stale store states bring removed members back from the dead... read more